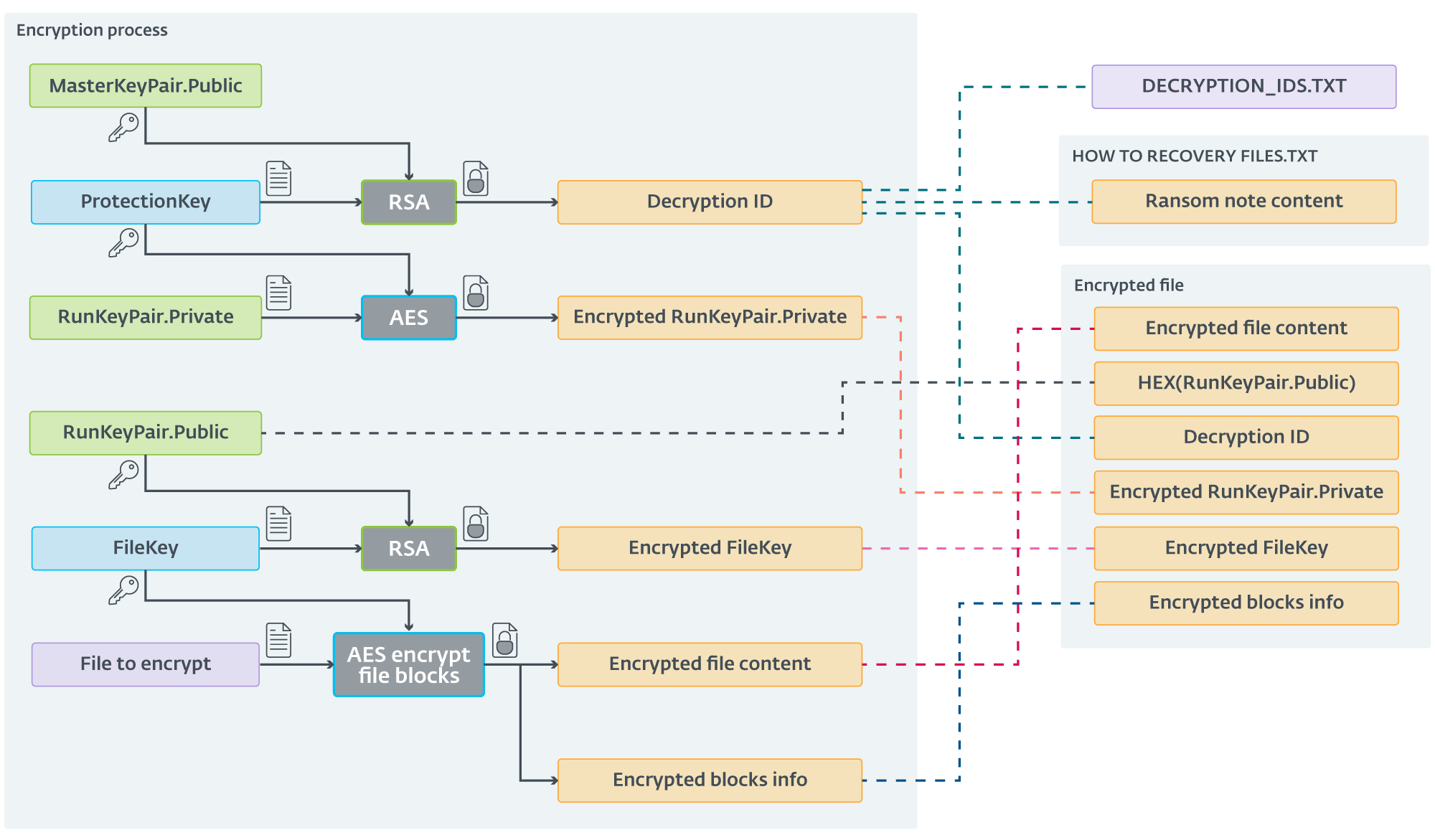
Encryption scheme utilized by the latest ScRansom samples | Image: ESET
In a significant development tracked by ESET researchers, the threat actor known as CosmicBeetle has intensified its ransomware operations, replacing its previous Scarab ransomware with a custom tool called ScRansom. As CosmicBeetle continues to target small and medium-sized businesses (SMBs) across Europe and Asia, its evolving tactics are catching the attention of cybersecurity professionals worldwide.
CosmicBeetle, active since 2020, has shifted from deploying the Scarab ransomware to developing its own custom ransomware, ScRansom. Although ScRansom lacks the sophistication of ransomware like LockBit, it has already caused significant damage to targeted organizations. ESET researchers attribute this shift to CosmicBeetle’s ongoing development of more specialized tools, allowing them to create greater disruption despite their relatively immature status in the ransomware ecosystem.
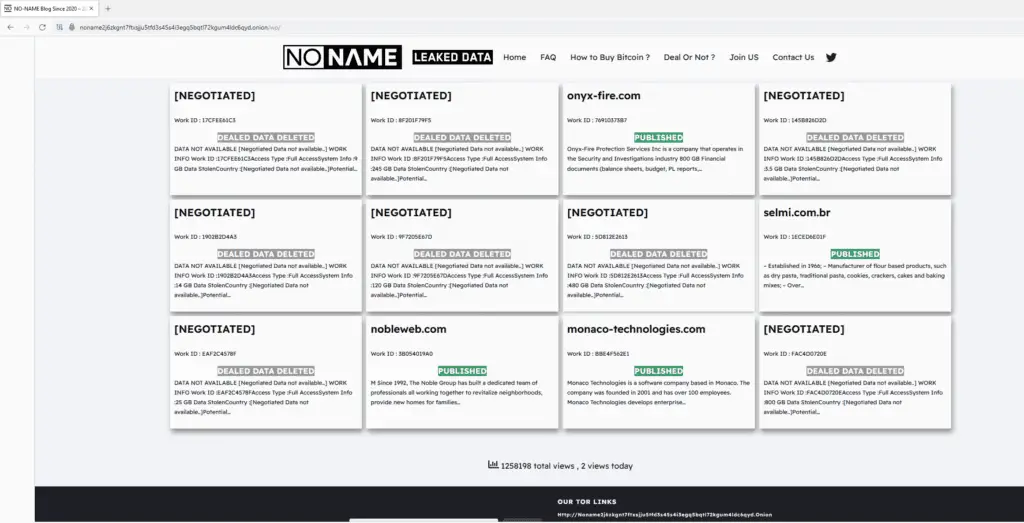
To bolster its reputation and increase ransom payments, CosmicBeetle has impersonated the infamous LockBit gang, one of the most well-known ransomware groups. Using the leaked LockBit builder, CosmicBeetle has crafted fake ransom notes and mimicked LockBit’s dedicated leak site to further convince victims to pay. This tactic, while deceptive, highlights the resourcefulness of this up-and-coming ransomware group.
One of the most recent developments surrounding CosmicBeetle is its suspected affiliation with RansomHub, a relatively new ransomware-as-a-service (RaaS) platform. ESET researchers believe CosmicBeetle is using RansomHub’s tools alongside its own, blending its ScRansom payload with RansomHub’s EDR-killing tools to gain access to high-value targets. This partnership suggests that CosmicBeetle is expanding its operations and seeking collaboration with more established ransomware actors in the cybercriminal underworld.
CosmicBeetle’s primary targets are SMBs across a variety of sectors, including manufacturing, healthcare, education, and financial services. These businesses, often lacking robust patch management or cybersecurity measures, are particularly vulnerable to ransomware attacks. CosmicBeetle exploits vulnerabilities such as CVE-2017-0144 (EternalBlue) and CVE-2023-27532 (Veeam Backup & Replication) to breach systems.
Although ScRansom is not as polished as other ransomware families, it is under continuous development. The encryption process employed by ScRansom is notably complex, making decryption challenging for victims. In some cases, multiple decryption keys are required, and even then, victims may lose files permanently depending on the mode CosmicBeetle applied during encryption.
As CosmicBeetle continues to grow its presence in the ransomware ecosystem, its tactics, alliances, and evolving tools make it a threat to watch. The group’s use of ScRansom, along with its collaboration with RansomHub, indicates that CosmicBeetle is stepping up its game, targeting a wider range of industries and posing an increasing risk to organizations around the globe.
SMBs are urged to remain vigilant and update their cybersecurity defenses to mitigate the growing threat posed by CosmicBeetle and similar ransomware groups.
Related Posts:
- RansomHub: A New Ransomware-as-a-Service Threatens Multiple Operating Systems
- Ransomhub’s SCADA Hack: A Wake-Up Call for Industrial Cybersecurity
- Zerologon Vulnerability Strikes Again: RansomHub Exploits Legacy Flaw
- Unveiling RansomHub Ransomware: New Infection Chains and Rising Threats
- Leaked LockBit Tools: Novice Hackers Target Vulnerabilities