
A serious security flaw has been uncovered in Dragonfly2, an open-source, peer-to-peer-based file distribution and image acceleration system. The vulnerability, CVE-2023-27584, carries a CVSS score of 9.8, reflecting its critical nature. This flaw arises from the use of a hard-coded cryptographic key in the authentication process, leaving systems open to devastating attacks, including the possibility of unauthorized access with admin privileges.
Hosted by the Cloud Native Computing Foundation (CNCF) as an incubating-level project, Dragonfly2 is designed to tackle distribution challenges within cloud-native architectures. By leveraging peer-to-peer (P2P) file sharing, Dragonfly2 accelerates image distribution and deployment in cloud environments, making it a key tool for developers and organizations using cloud-native technologies.
However, the discovery of this vulnerability raises significant concerns about the security of any systems running Dragonfly2 versions 2.0.8 and earlier.
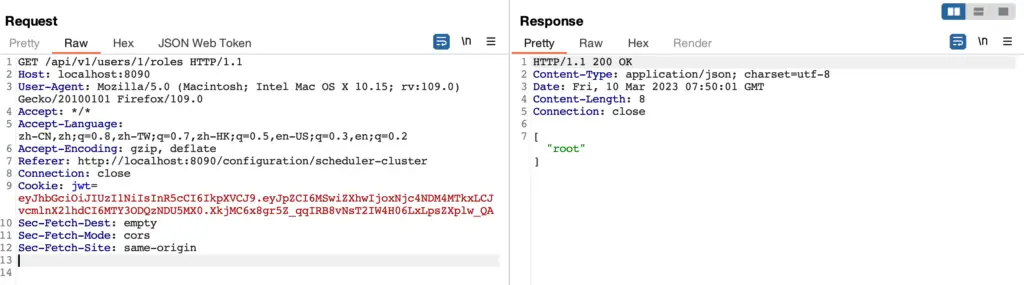
The vulnerability centers around JSON Web Tokens (JWT), which Dragonfly2 uses to verify user identities. Typically, JWT relies on a secret key to ensure the authenticity and integrity of the token. However, in Dragonfly2, this key was hard-coded as “Secret Key” in the source code, creating a serious security loophole. This allows an attacker to generate a valid JWT token using the known key, effectively bypassing authentication measures entirely.
The vulnerability is trivially easy to exploit. An attacker can use the following steps to generate a malicious JWT token:
Once the token is generated, the attacker can send requests using this forged JWT token and gain access to sensitive data and services without any restrictions. Essentially, the attacker can impersonate any user, including those with admin-level privileges.
The developers of Dragonfly2 addressed this vulnerability. All users and organizations are strongly advised to update to version 2.0.9 or later to prevent any exploitation.