
Akamai researcher Stiv Kupchik published the technical details and a proof-of-concept (PoC) exploit code for a critical Elevation of Privilege (EoP) vulnerability, CVE-2024-43532, in Microsoft’s Remote Registry client, with a CVSS score of 8.8. This vulnerability exploits a fallback mechanism in the WinReg client, which insecurely uses obsolete transport protocols if the preferred SMB transport is unavailable. This flaw presents a significant risk, enabling attackers to relay NTLM authentication details, potentially compromising sensitive systems.
According to Kupchik’s research, CVE-2024-43532 arises from a weakness in how the WinReg client handles authentication when the SMB protocol is unavailable. The system falls back to using legacy protocols that do not adequately secure the transmission of authentication data. The researcher explains, “By exploiting this vulnerability, an attacker can relay the client’s NTLM authentication details to the Active Directory Certificate Services (ADCS), and request a user certificate to leverage for further authentication in the domain.”
This issue stems from outdated authentication practices within Microsoft’s Remote Procedure Call (RPC) framework, particularly when interacting with the Remote Registry service, which allows processes on different machines to communicate over the network.
Kupchik’s team identified that in many instances, Microsoft’s RPC protocol relies on insecure authentication levels, allowing attackers to relay credentials across networks. When the RPC client binds to a server, authentication metadata is passed along, which can be intercepted and manipulated. The researcher highlights, “If there’s no authentication involved, the RPC binding is simply used to decide on the transfer syntax… authentication levels vary, and attackers are interested in those with no defenses on the traffic.”
The real risk lies in the fallback behavior of the BaseBindToMachine function, which uses weak authentication when forced to connect over less-secure protocols like TCP/IP. This fallback allows an attacker to act as a man-in-the-middle, relaying credentials to other systems, particularly Active Directory Certificate Services (ADCS). Kupchik’s report states, “Once it falls back to any other protocol besides SMB, it uses RpcBindingSetAuthInfoA to set the authentication level to Connect, which is insecure.”
The Akamai team has created a proof of concept (PoC) exploit code for CVE-2024-43532, which they shared publicly via their GitHub repository. Their research demonstrated how the vulnerability can be weaponized to impersonate users within a domain, gaining unauthorized access to critical systems. In their testing, they used a certificate obtained through ADCS to authenticate to LDAP services on a domain controller, eventually creating a persistent domain administrator account.
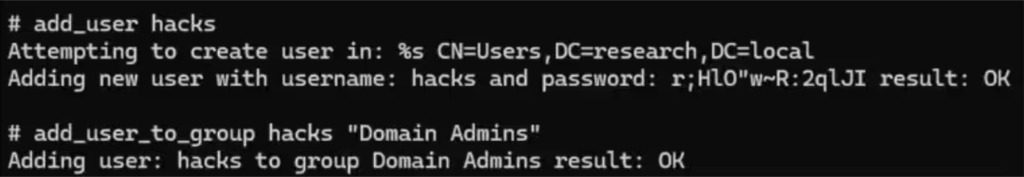
The implications of this are severe. Attackers could potentially gain full control over corporate networks, bypassing multiple layers of security by simply exploiting an obscure fallback mechanism. The Akamai team further warns that “the fallback to TCP/IP is quite promising, as it means we can use the insecure authentication method to relay the traffic using a machine-in-the-middle attack without the client noticing.”
This vulnerability was responsibly disclosed to Microsoft’s Security Response Center (MSRC) in February 2024, and a patch was issued as part of October 2024’s Patch Tuesday. Microsoft’s update addressed the fallback behavior and ensured that insecure authentication protocols are no longer used in the event of SMB failures.