Image: DEFCON
A comprehensive security audit by the Faraday Team has unveiled a series of critical vulnerabilities in DrayTek Vigor routers, exposing widespread security weaknesses that could allow attackers to gain complete control over affected devices.
DrayTek, a popular choice for small office/home office (SOHO) environments, has been found to harbor numerous flaws, including weak authentication mechanisms, insecure kernel module updates, and persistent backdoor opportunities. The Faraday Team’s research, driven by the challenge of DrayTek’s proprietary firmware format, has resulted in the discovery of multiple high-severity vulnerabilities.
The research revealed a range of vulnerabilities, including:
- CVE-2024-41335 (CVSS 7.5): Non-constant time password comparison: This flaw allows potential timing attacks to extract sensitive information.
- CVE-2024-41336 (CVSS 7.5): Insecure password storage: Passwords are stored in plaintext, enabling attackers with physical or memory access to retrieve credentials.
- Predictable 2FA code generation: WAN login second-factor authentication codes can be calculated based on boot time, bypassing this security measure.
- CVE-2024-41338 (CVSS 7.5): DHCP server NULL pointer dereference: Crafted DHCP requests can cause denial-of-service (DoS) attacks.
- CVE-2024-41339 (CVSS 9.8): Undocumented kernel module installation through CGI configuration endpoint: Attackers can upload crafted kernel modules for arbitrary code execution.
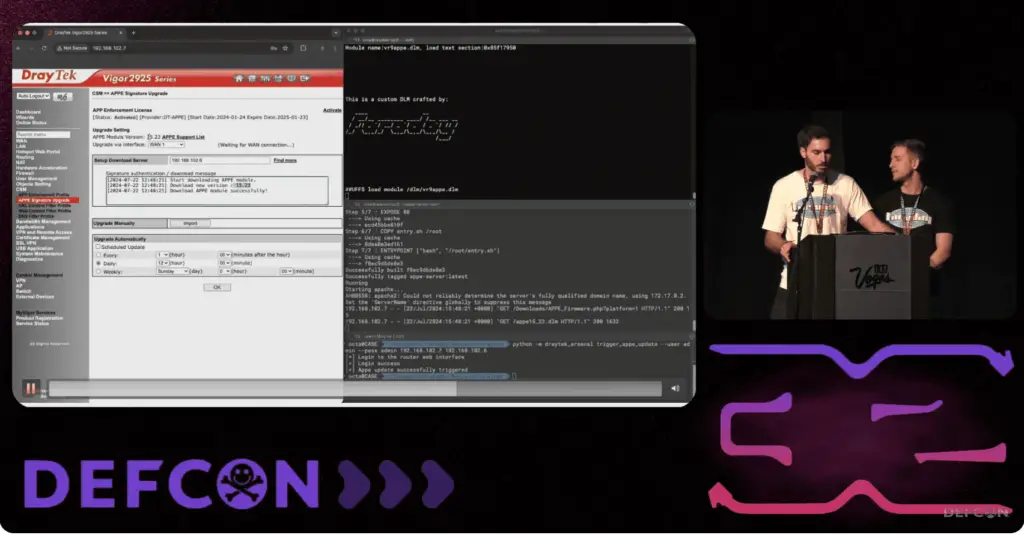
- CVE-2024-41340 (CVSS 8.4): APP Enforcement signature update allows arbitrary kernel module installation: Attackers can upload arbitrary APP Enforcement signatures, leading to arbitrary code execution.
- CVE-2024-41334 (CVSS 9.8): Missing SSL certificate validation for APP Enforcement signature updates: Attackers can install crafted APPE modules from non-official servers, leading to arbitrary code execution.
- CVE-2024-51138 (CVSS 9.8): TR069 STUN server buffer overflow: Remote attackers can execute arbitrary code via a stack-based buffer overflow in the TR069 STUN server’s URL parsing.
- CVE-2024-51139 (CVSS 9.8): CGI POST integer overflow: Integer overflow in the CGI parser can lead to heap overflows and arbitrary code execution.
The most critical vulnerabilities, CVE-2024-41339, CVE-2024-41340, CVE-2024-41334, CVE-2024-51138, and CVE-2024-51139, all carry a CVSS score of 9.8, indicating a severe risk. These flaws allow attackers to execute arbitrary code, potentially leading to complete system compromise.
“Affected Vigor routers allow kernel modules to be uploaded through the CGI endpoint used for restoring saved configurations,” the advisory notes regarding CVE-2024-41339. “Attackers can exploit this undocumented feature to upload a crafted kernel module, obtaining arbitrary code execution.”
Similarly, CVE-2024-41334 reveals that “Affected Vigor routers do not validate SSL certificates when downloading APP enforcement signatures from Draytek servers, allowing attackers to install crafted APPE modules from nonofficial servers.”
The security flaws impact various Draytek Vigor models, including Vigor165, Vigor2862, Vigor3912, and others. Vulnerable firmware versions range from 3.9.7 to 4.4.5.8, depending on the router model.
The Faraday Team has provided a detailed list of affected firmware versions. Users are strongly advised to update their DrayTek Vigor routers to the latest firmware versions to mitigate these critical vulnerabilities.
Affected users should consult the Faraday Team’s advisory and DrayTek’s official website for detailed information and firmware updates. The Faraday Team plans to release further details on CVE-2024-51138 and CVE-2024-51139 in future posts.