Critical Security Flaws Uncovered in Cisco Small Business Series Switches
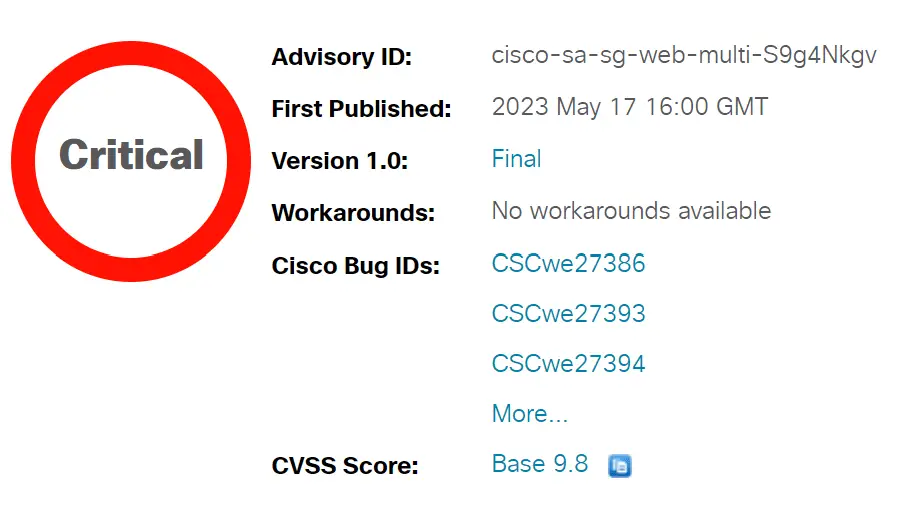
Multiple critical vulnerabilities have been exposed in a range of Cisco products, potentially paving the way for cyber attackers to exploit these flaws, leading to severe consequences such as remote code execution, privilege escalation, sensitive information disclosure, and even denial of service. These vulnerabilities are notable for their severity, as expressed by their Common Vulnerability Scoring System (CVSS) score of 9.8, placing them in the “critical” category.

It’s important to note that, although proof-of-concept exploit codes are available for these vulnerabilities, Cisco’s Product Security Incident Response Team (PSIRT) reported that, to their knowledge, there have been no instances of these vulnerabilities being exploited in cyber attacks so far. However, the existence of these exploit codes implies the urgency of patching these vulnerabilities.
One important point for the network administrators and users of affected Cisco products to take note of is that firmware updates addressing these vulnerabilities will not be provided for the products that have already entered the end-of-life process.
List of Affected Products
The vulnerabilities impact a slew of Cisco Small Business Switches if they are operating on susceptible firmware releases, including but not limited to:
– 250 Series Smart Switches
– 350 Series Managed Switches
– 350X Series Stackable Managed Switches
– 550X Series Stackable Managed Switches
– Business 250 Series Smart Switches
– Business 350 Series Managed Switches
– Small Business 200 Series Smart Switches
– Small Business 300 Series Managed Switches
– Small Business 500 Series Stackable Managed Switches
A Closer Look at the Vulnerabilities
Cisco has identified and reported four vulnerabilities, all with an alarming CVSS score of 9.8.
The four vulnerabilities, CVE-2023-20159, CVE-2023-20160, CVE-2023-20161, and CVE-2023-20189, all stem from a security hole in the web-based user interface of the Cisco Small Business Series Switches. The vulnerabilities are caused by improper validation of requests sent to the web interface. This lack of validation could allow a rogue request to execute arbitrary code with root privileges on the affected device.
This means that a remote attacker, without requiring authentication, could potentially send a tailored request through the web interface and execute arbitrary code with root privileges on the target device. The consequences of such an exploit are grave, giving the attacker a high level of control over the compromised device.
To mitigate these vulnerabilities, Cisco has released software updates. It’s essential for users and administrators of vulnerable Cisco devices to install these updates as soon as possible since there are currently no viable workarounds.
This week, Cisco also released patches for five other high-severity flaws, including an unauthenticated configuration reading vulnerability (CVE-2023-20162), an unauthenticated Denial-of-Service vulnerability (CVE-2023-20158), and an unauthenticated heap buffer overflow vulnerability (CVE-2023-20024, CVE-2023-20156, CVE-2023-20157) in its Small Business Series Switches. Additional information on the addressed vulnerabilities can be found on Cisco’s product security page.





