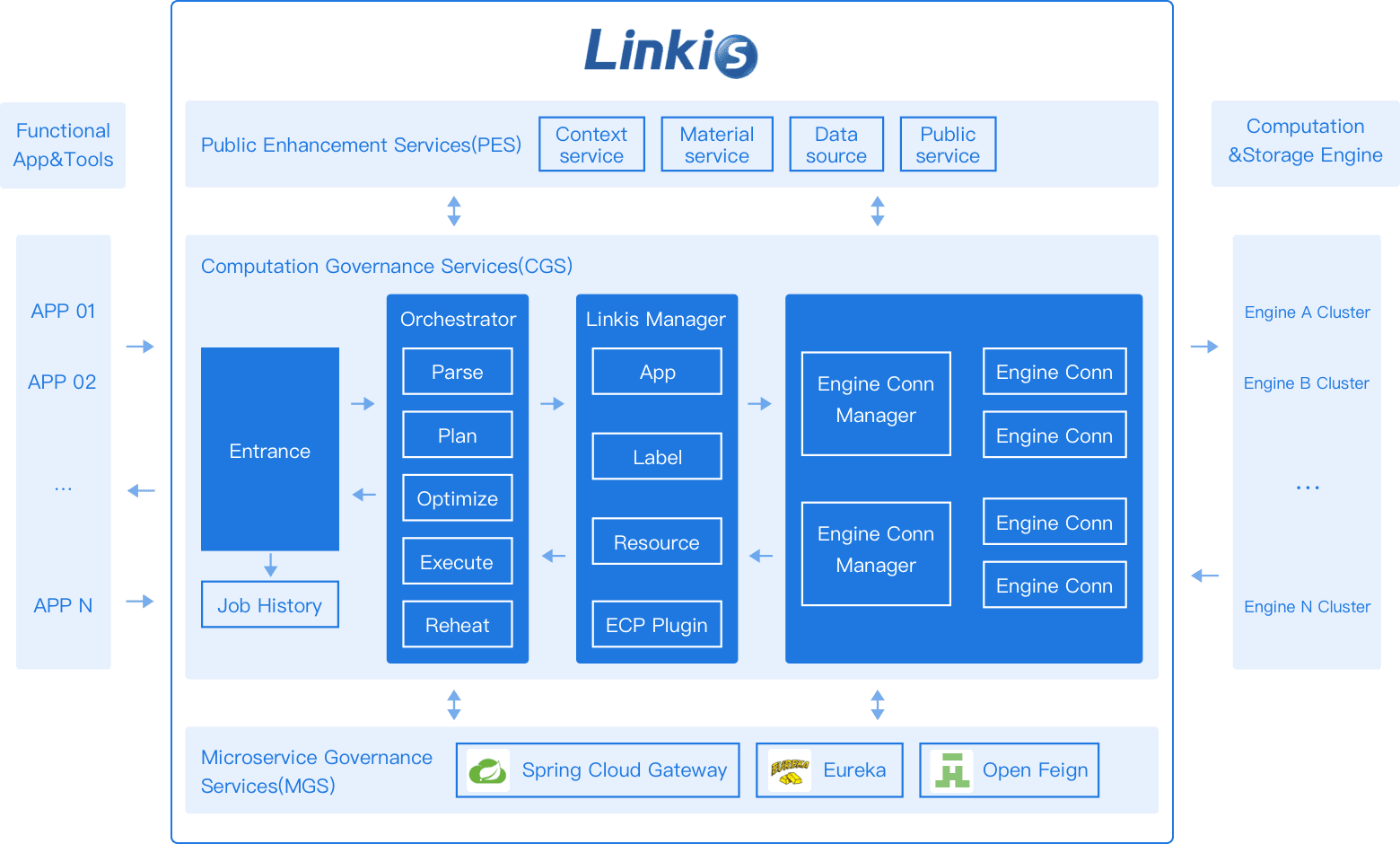
Apache Linkis, the popular computation middleware widely used to connect applications with various data processing engines, has addressed two significant security vulnerabilities that could have exposed users to potential attacks.
Apache Linkis simplifies the process for upper applications to access various engines such as MySQL, Apache Spark, Apache Hive, Presto, and Apache Flink through standardized interfaces like REST/WS/JDBC. It also offers data source and metadata management services via REST interfaces, making it a crucial tool for many organizations. However, recent findings have exposed vulnerabilities that could undermine its security.
The first vulnerability, tracked as CVE-2024-27181, is a privilege escalation flaw in the basic management services component of Linkis versions 1.3.2 to 1.5.0. This flaw could allow an attacker with a trusted account to access sensitive token information, potentially compromising the security of connected systems.
The second vulnerability, identified as CVE-2024-27182, is an arbitrary file deletion vulnerability also affecting the basic management services in the same Linkis versions. This vulnerability could enable an administrator to delete any file accessible by the Linkis system user, leading to data loss or disruption of critical operations.
Both vulnerabilities have been patched in the latest Apache Linkis release, version 1.6.0. Users are strongly advised to upgrade to this version immediately to protect their systems from potential exploitation.
The Apache Software Foundation has not provided specific details about the vulnerabilities or the potential impact of successful attacks. However, given the critical nature of these flaws, it is crucial for organizations using Apache Linkis to prioritize patching their systems as soon as possible.
Related Posts:
- Apache Linkis patched several important security vulnerabilities
- Apache Linkis RCE Vulnerability
- Security Vulnerabilities in Apache Linkis Expose Systems to Arbitrary File Reading and RCE
- Apache HTTP Server Hit by Triple Vulnerabilities – Users Urged to Update