Researcher Yehuda Smirnov has uncovered a critical vulnerability in Microsoft’s Windows Hello for Business (WHfB) authentication system. His discovery calls into question the reliability of biometric security, once considered invincible.
WHfB, introduced by Microsoft in 2016 for commercial and corporate versions of Windows 10, was designed as a bulwark against phishing attacks. The system employs cryptographic keys embedded in the computer’s Trusted Platform Module (TPM) and is activated via biometric verification or a PIN. However, Smirnov, part of Accenture’s “red team” of ethical hackers, found that this protection could be circumvented by altering parameters in the authentication request.
It is worth noting that Yehuda is not the first to highlight the platform’s imperfections. For instance, in 2019, researchers examined attack vectors on WHfB, specifically the persistent Active Directory backdoor that evaded detection mechanisms.
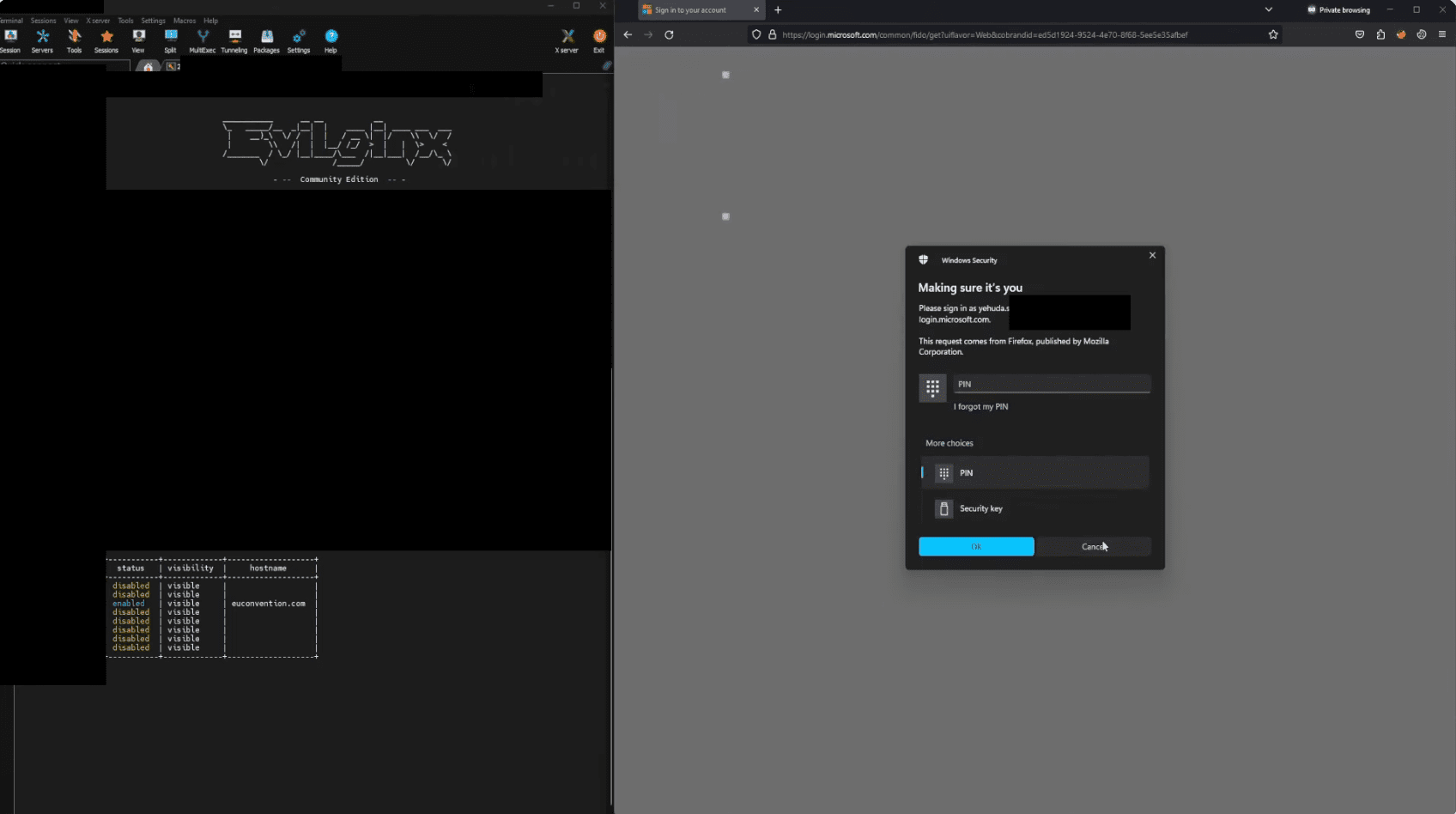
The WHfB protection can be bypassed by downgrading the authentication level. Smirnov utilized the Evilginx framework for an adversary-in-the-middle (AitM) attack to intercept and modify requests to Microsoft’s authentication services. As a result, the system reverted to less secure methods: traditional passwords or one-time SMS codes.
To execute the attack, the hacker modified Evilginx’s code and created a specialized phishlet to automate the process. The key to the attack’s success was altering the user-agent or “isFidoSupported” parameter in the “/common/GetCredentialType” request.
The vulnerability does not inherently render the WHfB protocol unsafe. The issue lies in how organizations configure and enforce strict authentication. “Organizations lacked the capability to enforce user sign-in through only phishing-resistant methods, leaving room for less secure authentication pathways,” Smirnov notes.
During the initial setup of Windows Hello on a user’s device, the WHfB system creates a private key and stores it in the computer’s secure TPM module. Hence, logging into the system requires biometric or PIN confirmation compatible with Windows Hello.
Microsoft generates a request sent to the user’s device through the WebAuthn API in the browser. WebAuthn then interacts with Windows Hello, requesting confirmation using the private key. WebAuthn is a W3C standard underlying modern authentication methods like FIDO2 and passkeys.
In response to Smirnov’s discovery, Microsoft released an update in March. The Azure portal now features a new function called “authentication strength.” This allows administrators to configure the system so employees use only phishing-resistant login methods.
This feature works with Microsoft Entra ID applications and allows for flexible protection level configuration. Administrators can consider various factors: the importance of protected data, user risk levels, regulatory requirements, and even the user’s location.
The details of this research will be presented at the Black Hat USA 2024 conference in Las Vegas on August 8. Below is proof of concept video