CrowdStrike Bug Exploited: Handala Hacking Team Targets Israel
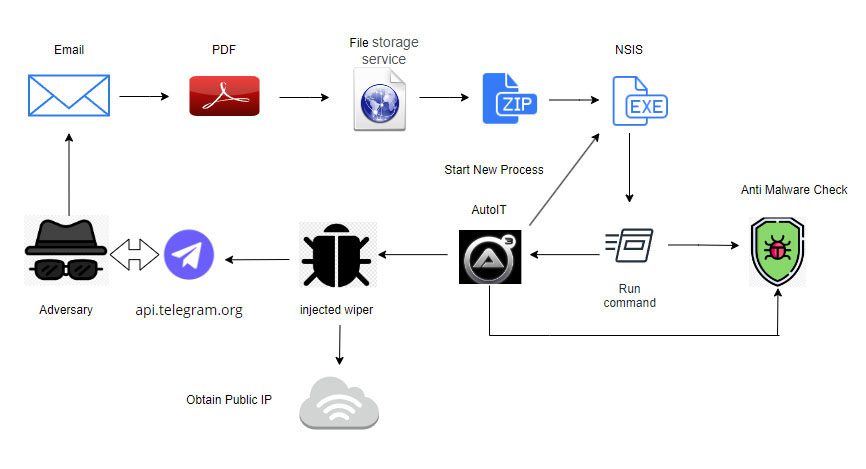
Recently, the hacker group Handala Hacking Team launched an attack on Israeli targets, disseminating malware through phishing emails that exploited the theme of a Falcon Sensor bug fix from CrowdStrike, which had caused widespread computer failures globally.
The Handala Hacking Team first made headlines in December of last year, when its initial post on the platform X tagged the Israeli National Cyber Directorate (INCD), drawing the attention of cybersecurity specialists. Official Israeli sources associate this group with Iran, although other organizations like Cyberint and Intezer identify it as a “pro-Palestinian activist group.”
Last week, cybersecurity firm Trellix confirmed the mass distribution of malicious emails to a group of Israeli clients. These emails were intercepted before reaching recipients’ inboxes, averting significant damage. Nonetheless, the attack merits mention due to its intriguing characteristics.
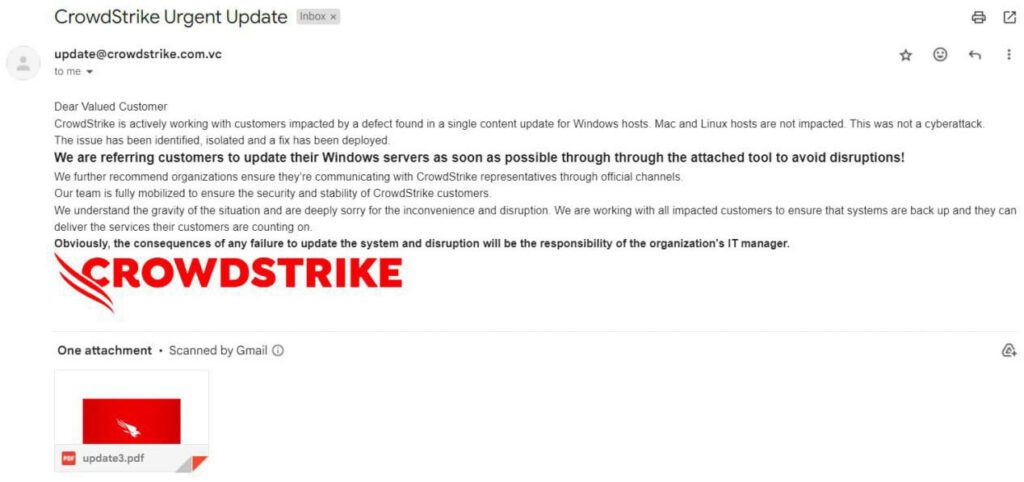
The CrowdStrike themed lure
The campaign begins with a fraudulent email purporting to be from CrowdStrike, offering a “fix” for issues caused by recent disruptions. The email contains a link to an archive “update.zip,” which includes an installer file “CrowdStrike.exe.” This file, an installer for Nullsoft Scriptable Install System (NSIS), deploys and executes malicious code that evades antivirus checks.
Once launched, the malware collects system information and transmits it via the Telegram API, allowing hackers to monitor the virus’s activity and track the victims. The virus then proceeds to destroy files on infected computers by overwriting data with random bytes.
To execute the attack, the script first checks for the presence of antivirus programs on the computer, such as Webroot, Avast, AVG, and others. If such programs are detected, the malware temporarily halts its activity to avoid detection. This is accomplished with a script that sends 186 ping commands to localhost, creating a three-minute delay.
The malicious code used in the attack includes obfuscated strings and complex checks to bypass sandboxes and antivirus programs. The primary objective of the virus is the destruction of files on infected computers. However, before doing so, all valuable data is transmitted to the attackers’ servers.
The reuse of the same code in multiple attacks indicates the repeated use of malware by the Handala group. This is confirmed by identical TypeLib ID identifiers in both old and new versions of the malware, suggesting a high likelihood that the group employs the same Visual Studio project to create their viruses.
The file deletion process involves checking if the file is in use by other processes. If the file is in use, the virus terminates the obstructing process before deleting the file. All information regarding the deletion process and the attack is sent to a Telegram channel managed by the hackers, allowing them to monitor the success of their actions and gather information about the victims.
The Handala Hacking Team is known for its aggressive and public actions. Their previous attacks have also targeted Israeli entities, and they frequently publish reports and statements about their activities, underscoring their hacktivist nature and desire for publicity.
To prevent such incidents, organizations are advised to enhance employee cybersecurity training, implement multi-factor authentication, and regularly update protective software. Continuous monitoring and timely response to suspicious activity will help minimize risks and safeguard critical data.





