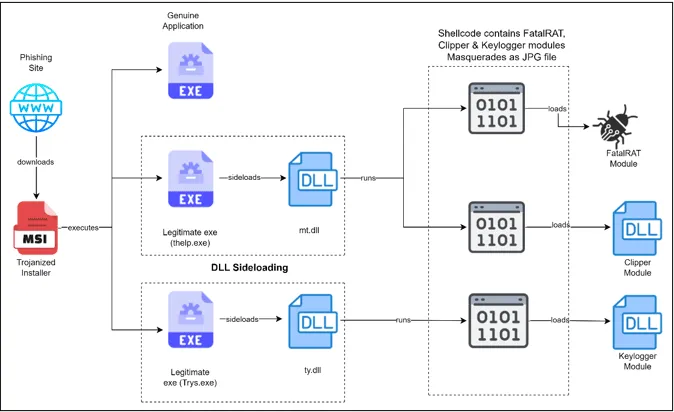
Infection chain
Cryptocurrency enthusiasts are being urged to exercise extreme caution after a new phishing campaign was uncovered by cybersecurity researchers at Cyble Research and Intelligence Labs (CRIL). The attack, which preys on users’ trust in familiar cryptocurrency applications, utilizes a potent combination of malware strains including a Remote Access Trojan (RAT) known as ‘FatalRAT.’
How The Attack Works
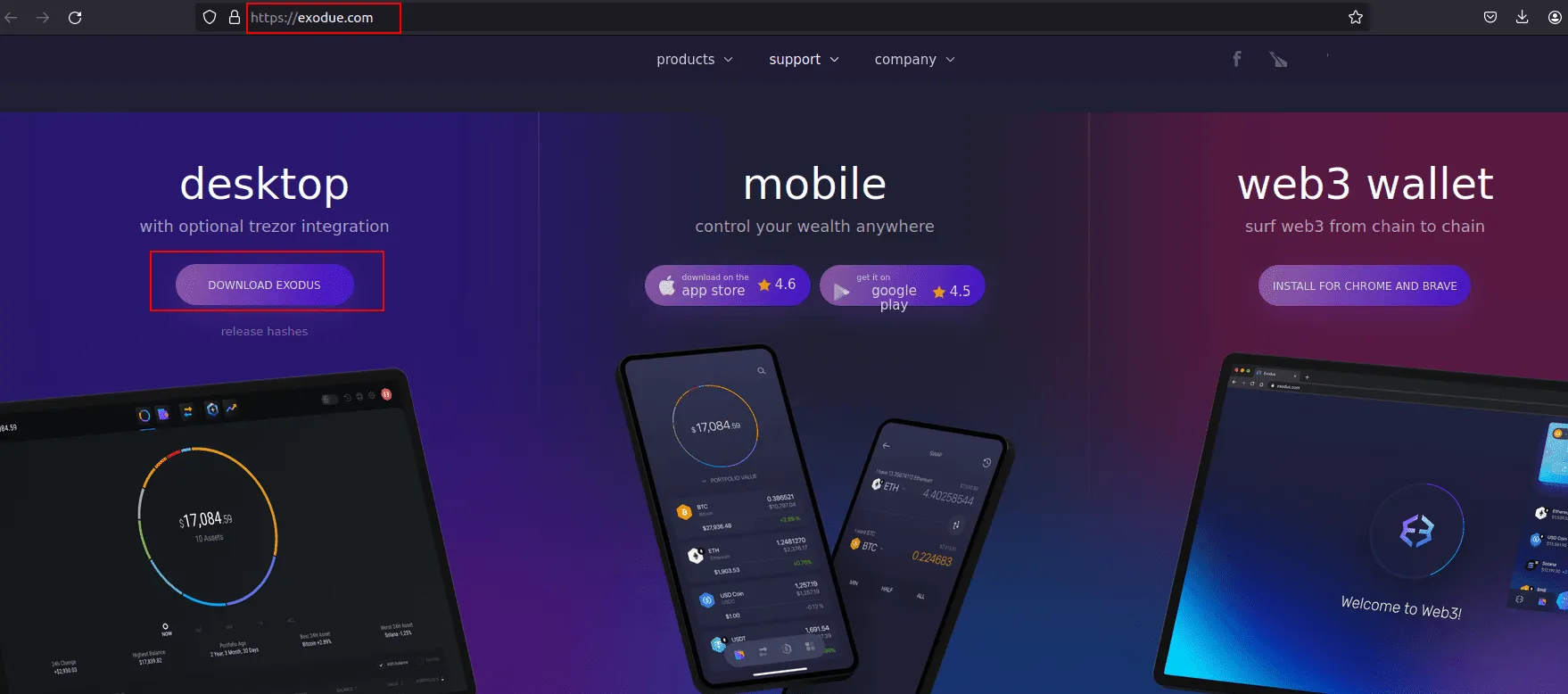
The attackers have gone to great lengths to deceive potential victims, creating a phishing website that closely mimics the interface of the popular Exodus cryptocurrency wallet. Unsuspecting users lured into downloading what appears to be the Exodus software from this fake site are actually installing a dangerous package of malware.
The malware utilizes a technique called “DLL side-loading” to disguise its malicious payloads, making them more difficult to detect. At its core, the main component of this multi-stage attack is the FatalRAT malware. This grants the attackers remote control over a victim’s computer, effectively allowing them to:
- Steal data from web browsers
- Log keystrokes to capture passwords and other sensitive information
- Manipulate cryptocurrency wallet addresses
- Potentially download additional malicious files
Clipper & Keylogger: A Dangerous Combination

This campaign is particularly insidious due to the inclusion of ‘Clipper’ malware, specifically designed to target cryptocurrency users. Clipper works by silently monitoring the victim’s clipboard, replacing legitimate cryptocurrency wallet addresses with those controlled by the attackers. This means that when a user thinks they are sending their cryptocurrency to a specific wallet, the funds are diverted to the attackers instead.
The addition of a keylogger module further increases the amount of sensitive information the attackers can collect. Keyloggers record every keystroke you make on your computer, providing the attackers with passwords, private messages, and even more cryptocurrency wallet information.
Who’s Behind the Attack?
While the identity of the threat actors remains unknown, security experts at CRIL believe that the similarities in techniques and targets suggest the same group might be responsible for previous, comparable campaigns.
Protect Yourself
Cryptocurrency users should be aware of these tactics and take proactive measures to protect themselves:
- Double-check all links: Never download software from links in emails or websites, even if they appear legitimate. Always go directly to the official website of the cryptocurrency wallet or application to secure the software.
- Scrutinize addresses: Always triple-check cryptocurrency wallet addresses before initiating any transaction.
- Use strong antivirus/security software: A reputable security suite with real-time monitoring can help detect this type of malware and block it before it can cause damage.