CSP – Content Security Policy

CSP (Content Security Policy) is mainly used to define which resources page (JS / CSS / FONT / IFRAME / XHR / …) can be loaded, can effectively play the role of a lot of security!
CSP can:
- Prevent operators hijacking (using script-src limit specified domain JS code to run, to avoid operators insert the code)
- Prevent XSS attacks (XSS attack will be a lot of references to other sites in the site execution of malicious code)
- Prevent clickjacking
- Prevent Android WebView UXSS (nesting other sites is prohibited iFrame content, etc.)
- …
Browser Support
Content-Security-Policy
– Chrome v25 and above
– Safari v7 and above
– iOS Safari v7.1 and above
– Android v4.4 and above
– Chrome For Android v46 and above
– Opera v32 and above
– Firefox v23 and above
X-WebKit-CSP
– Safari 5.1 <= ver => 6.1
– Chrome 14 <= ver => 24
X-Content-Security-Policy
– Firefox v4 <= ver >=22
– Internet Explorer v10
Syntax examples:
Content-Security-Policy: default-src ‘self’
PHP usage:
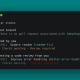
header(“Content-Security-Policy: script-src ‘self’ ‘unsafe-inline’ ‘unsafe-eval’; “);
Policy settings
| Key | Command Value | Description |
| default-src | self cdn.meterpreter.org | Define the default load policy for all resource types |
| script-src | self js.meterpreter.org | Defines the JavaScript loading policy |
| style-src | self css.meterpreter.org | Defines a Style style load strategy |
| img-src | self img.meterpreter.org | Defines the image image loading strategy
|
| content-src | self | Defined Xhr / Ajax / WebSockets / EventSource such as the request of the loading strategy. Not allowed, then there will be 400 |
| font-src | font.meterpreter.org | Defines the Web Font loading policy
|
| object-src | self | Defines the flash loading policy introduced by tags such as \ / \ / \ |
| media-src | media.meterpreter.org | Definition \ / \ and other tags to introduce the multimedia load strategy |
| frame-src | self | Defines the iframe load policy. Prevents ClickJacking (click hijacking) |
| sandbox | allow-forms | Define a request resource using the sandbox
|
| report-uri | /report-uri | The defined policy, if not allowed, will POST a request to that address |
| Command | Value |
| * | Allow any content
|
| None | No content is allowed
|
| self | Run homogenous content
|
| data | Running the data: protocol (Base64 image) |
| www.meterpreter.org | Allows loading the specified domain
|
| 113.421.129.12 | Allows loading the specified IP
|
| *.meterpreter.org | Allows the loading of subdomains |
| |https://securityonline.info | Allows loading of the specified domain |
| https: | Allows loading of https resources
|
| unsafe-inline | Allow loading of inline assets
|
| unsafe-eval | Allows dynamic loading of js, such as eval()/newFunction()/setTimeout()/setInterval() |
Example:
header(“Content-Security-Policy: script-src ‘self’ ‘unsafe-inline’ ‘unsafe-eval’ *.google-analytics.com; “);
header(“Content-Security-Policy: script-src ‘self’ ‘unsafe-inline’ ‘unsafe-eval’; font-src: ‘self’ *.google-font.com”);
CSP report
Formally joined the production environment can be collected only for a period of time before the rules do not match the log, observe the period of time no problem and then on the production environment. Or just as a monitoring abnormal behavior can also be used!
Content-Security-Policy-Report-Only: script-src ‘self’; report-uri https://securityonline.info/csp-report.html
The loading strategy defined after adding the above code will still execute, but will POST a Content-Type: JSON request to csp-report.html, in the following format:
{“csp-report”:{
“document-uri”:”https://securityonline.info/about”
“referrer”:”https://securityonline.info”
“violated-directive”:”script-src ‘self'”
“original-policy”:”script-src ‘self’;
report-uri http://www.meterpreter.org/csp-report.html”
“blocked-uri”:”http://www.google-analytics.com”
“source-file”:”https://securityonline.info/link”
“line-number”:4
“column-number”:75
“status-code”:200
}}