Cuckoo Sandbox is the leading open source automated malware analysis system.
What does that mean? It simply means that you can throw any suspicious file at it and in a matter of seconds Cuckoo will provide you back some detailed results outlining what such file did when executed inside an isolated environment.
It’s used to automatically run and analyze files and collect comprehensive analysis results that outline what the malware does while running inside an isolated operating system.
It can retrieve the following type of results:
- Traces of calls performed by all processes spawned by the malware.
- Files being created, deleted and downloaded by the malware during its execution.
- Memory dumps of the malware processes.
- Network traffic trace in PCAP format.
- Screenshots taken during the execution of the malware.
- Full memory dumps of the machines.
Cuckoo is designed to be used both as a standalone application as well as to be integrated in larger frameworks, thanks to its extremely modular design.
It can be used to analyze:
- Generic Windows executables
- DLL files
- PDF documents
- Microsoft Office documents
- URLs and HTML files
- PHP scripts
- CPL files
- Visual Basic (VB) scripts
- ZIP files
- Java JAR
- Python files
- Almost anything else
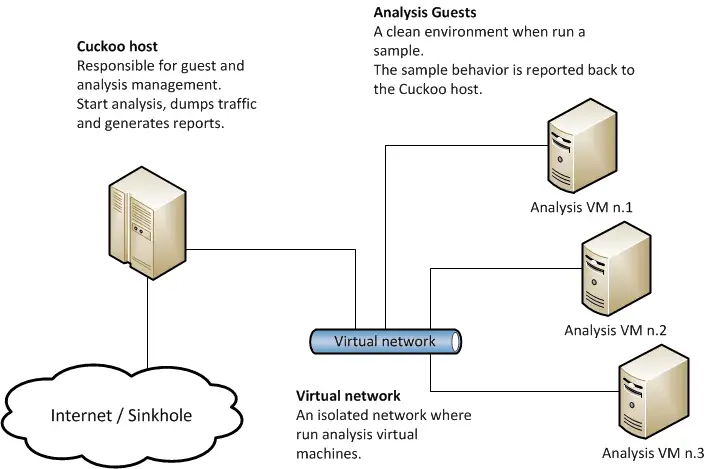
Cuckoo Sandbox consists of central management software which handles sample execution and analysis.
Each analysis is launched in a fresh and isolated virtual or physical machine. The main components of Cuckoo’s infrastructure are a Host machine (the management software) and a number of Guest machines (virtual or physical machines for analysis).
The Host runs the core component of the sandbox that manages the whole analysis process, while the Guests are the isolated environments where the malware samples get actually safely executed and analyzed.
The following picture explains Cuckoo’s main architecture:
Install && Use
© Copyright 2010-2019, Cuckoo Foundation