CVE-2022-20696: Cisco SD-WAN vManage Software Security Bypass Flaw
Cisco on Wednesday announced that it has patched a vulnerability in its SD-WAN solution, that has been assigned a “high severity” rating, based on its CVSS score (7.5/10).
The high-severity vulnerability was reported to Cisco by Orange Business. Track as CVE-2022-20696, the bug is caused by the messaging server container ports on an affected system lack sufficient protection mechanisms. By connecting to the messaging service ports, an attacker could exploit this vulnerability to view and inject messages into the messaging service.
According to Cisco, “An attacker could exploit this vulnerability by connecting to the messaging service ports of the affected system. To exploit this vulnerability, the attacker must be able to send network traffic to interfaces within the VPN0 logical network. This network may be restricted to protect logical or physical adjacent networks, depending on device deployment configuration. A successful exploit could allow the attacker to view and inject messages into the messaging service, which can cause configuration changes or cause the system to reload.”
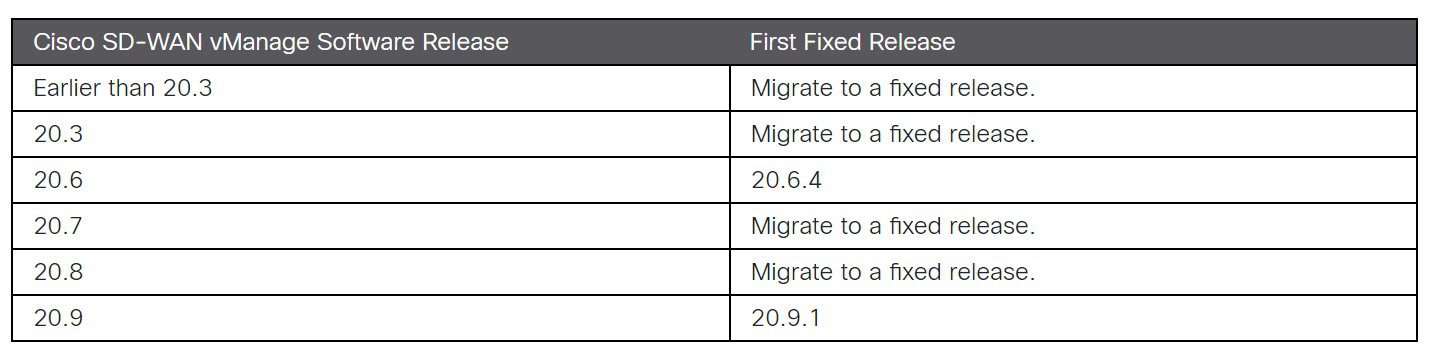
The CVE-2022-20696 hole can impact several Cisco products if they are running a Cisco SD-WAN vManage Software prior to 20.9.1.

Image: Cisco
Administrators can use access control lists (ACLs) to block ports 4222, 6222, and 8222, which are used by Cisco SD-WAN vManage Software messaging services.
Cisco says there is no evidence that this flaw has been exploited in malicious attacks.





