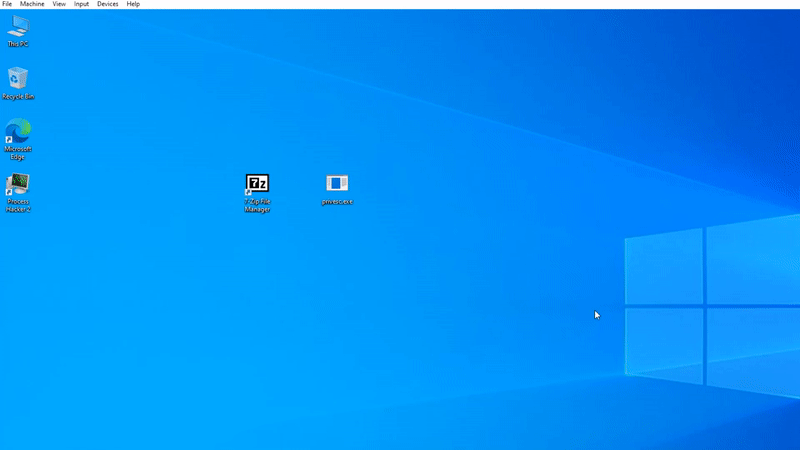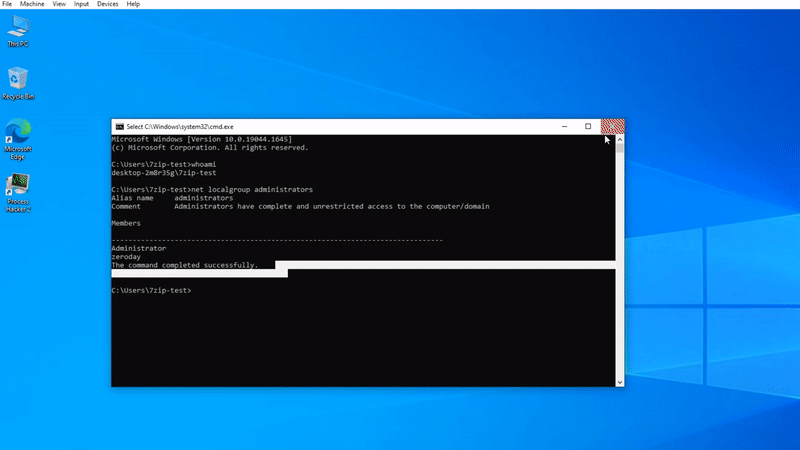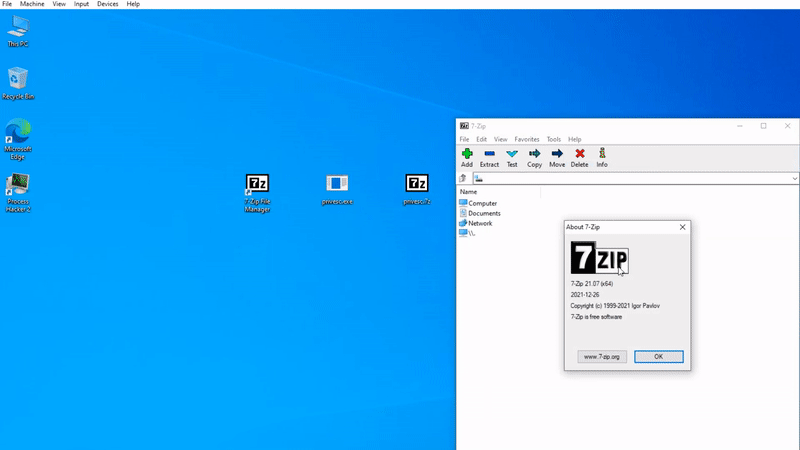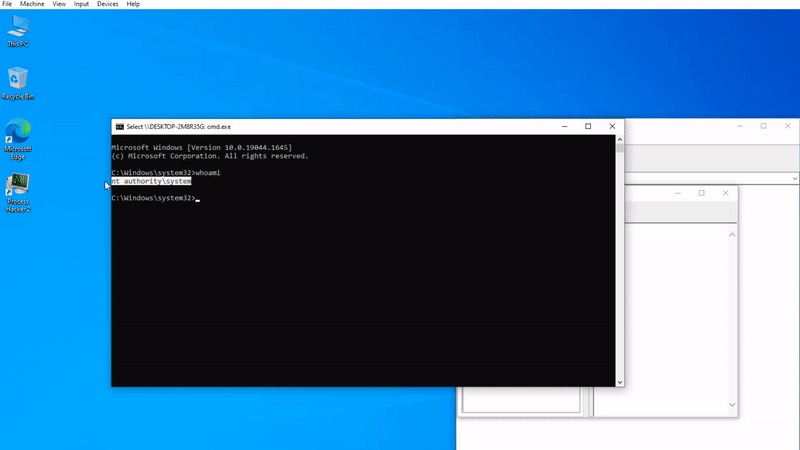
The current version and some earlier versions of the popular open-source compression manager 7-Zip have a security vulnerability, numbered CVE-2022-29072, which could allow hackers to escalate privileges. At present, 7-Zip has not released a security update to address this vulnerability, which means that all current versions of 21.07 are vulnerable.
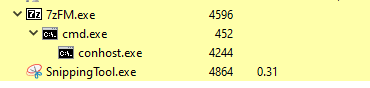
The vulnerability stems from a misconfiguration of 7z.dll and a heap overflow. The content area of help works through Windows HTML Helper. If command injection is performed, a child process will appear under 7zFM.exe. Due to the memory interaction in the 7z.dll file, the called cmd.exe child process will be granted administrator mode.

After the installation of 7-zip software, the help file in the HELP > contents content works through the Windows HTML Helper file, but after the command injection, a child process appeared under the 7zFM.exe process,
which is seen after the command injection, which is quite interesting, after this situation, 7-zip with WinAFL The fuzzing process was carried out. Thanks to the overflow vulnerability and wrong authorization based on the heap, it was noticed that when the process injection technique was applied (in memory) by using the powers of the 7z.dll file and the command prompt was called again, it was authorized on cmd.exe with the administrator mode. In the payload developed after this process, the psexec.exe file was used as raw;
NT AUTHORITY\SYSTEM privilege has been accessed thanks to the command “psexec -s cmd.exe -nobanner”.