Networking equipment maker Zyxel has released security updates for a critical vulnerability affecting its business firewall and VPN products that could enable an attacker to take control of the devices.
The flaw has been assigned the identifier CVE-2022-30525. Credited with reporting the bug is Jake Baines of Rapid7, and it is being disclosed in accordance with Rapid7’s vulnerability disclosure policy.
Rapid 7 writes in a blog published, “Rapid7 discovered and reported a vulnerability that affects Zyxel firewalls supporting Zero Touch Provisioning (ZTP), which includes the ATP series, VPN series, and the USG FLEX series (including USG20-VPN and USG20W-VPN). The vulnerability, identified as CVE-2022-30525, allows an unauthenticated and remote attacker to achieve arbitrary code execution as the nobody user on the affected device.”
A new Metasploit module to exploit this flaw is available. The module can be used to establish a nobody Meterpreter session.
The following Zyxel products are impacted
Affected Model Affected Firmware Version USG FLEX 100, 100W, 200, 500, 700 ZLD5.00 thru ZLD5.21 Patch 1 USG20-VPN, USG20W-VPN ZLD5.10 thru ZLD5.21 Patch 1 ATP 100, 200, 500, 700, 800 ZLD5.10 thru ZLD5.21 Patch 1
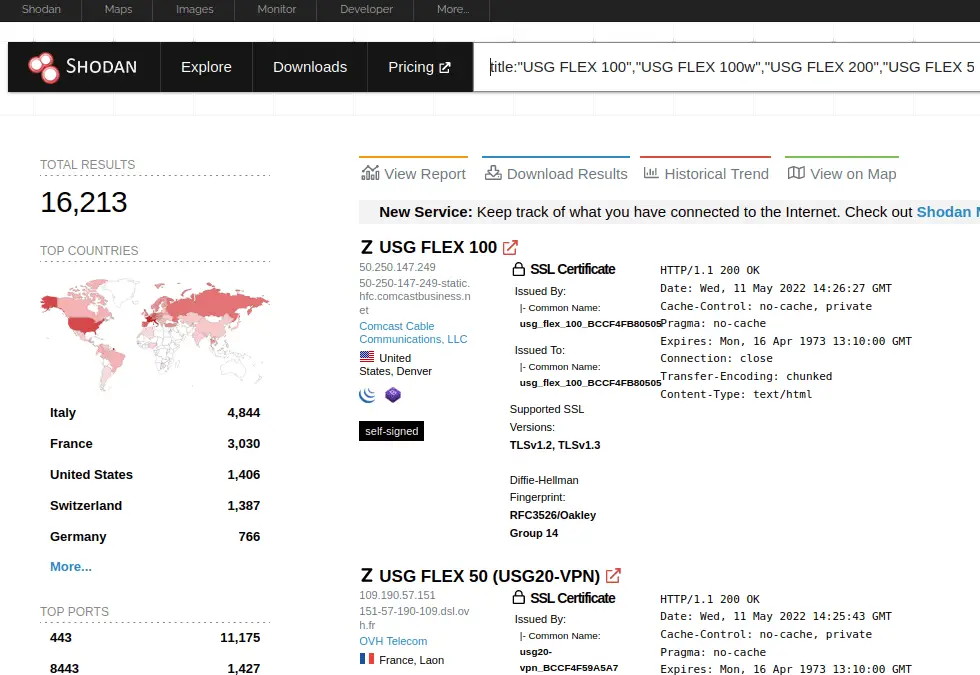
The critical bug may affect more than 15,000 systems, according to a new query searched today on Shodan, a search engine that scans for vulnerable devices.

It’s recommended that users install the firmware updates to prevent any potential threats. Also, disable WAN access to the administrative web interface of the system.