All Airspan AirSpot 5410 devices from version 0.3.4.1-4 and under from Airspan have been identified as affected by 4 new critical flaws including an unauthenticated remote code execution vulnerability that, if successfully exploited, could lead to full compromise of the devices and unauthorized access to the network.
The AirSpot 5410 is an advanced, LTE, CAT12, outdoor, multi-service product specifically designed to meet data needs for residential, business, and enterprise users. Supporting Gigabit networking functionality and multiple TDD band operations, it enables wide coverage and high-data throughput. It provides a Gigabit PoE connection to connect user terminal devices, such as a router or WiFi AP products.
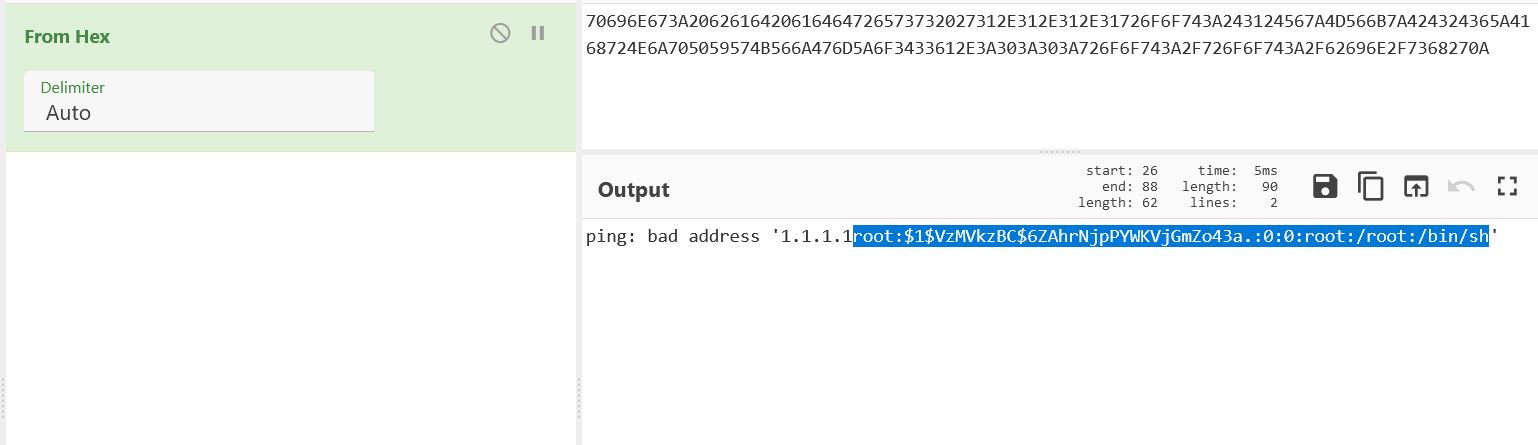
Track as CVE-2022-36267, the flaw exists in ping function that allows an attacker to take control of the devices. “The ping functionality can be called without user authentication but can also be injected by any Linux command. This vulnerability is exploited via the binary file /home/www/cgi-bin/diagnostics.cgi that accept unauthenticated request and unsanitized data. As a result, a malicious actor can craft a specific request and interact remotely with the device.”

To prevent hackers from exploiting CVE-2022-36267, make sure that all requests to /home/www/cgi-bin/diagnostics.cgi are authenticated, it is also important to strengthen the back-end logic to make sure that the data sent to the server are clean.
Two security researchers Thomas Knudsen and Samy Younsi also found 3 critical flaws that affect Airspan AirSpot 5410 devices including:
-
[CVE-2022-36266] – Unauthenticated remote Persistent Cross-site Scripting (Stored XSS).
As the binary file /home/www/cgi-bin/login.cgi does not check if the user is authenticated, a malicious actor can craft a specific request on the login.cgi endpoint that contains a base32 encoded XSS payload that will be accepted and stored. A successful attack will results in the injection of malicious scripts into the user settings page. -
[CVE-2022-36264] – Unauthenticated remote Arbitrary File Upload.
Unrestricted file upload allows overwriting arbitrary files. A malicious actor can remotely upload the file of his choice and overwrite any file in the system by manipulating the filename and append a relative path that will be interpreted during the upload process. Using this method, it is possible to rewrite any file in the system. -
[CVE-2022-36265] – Hidden system command web page.
After performing a reverse engineering of the firmware we discovered that a hidden page not listed in the administration management interface allows to execute Linux commands on the device with root privileges. From here we had access to all the system files but also be able to change the root password and have full access on the device.
To make it worse, the researchers have released PoC with detailed techniques. Due to the detailed technique that has been published, the hacker can write the script to exploit this flaw and scan the targeted devices. It is recommended to apply the recommendations that researchers issued.