CVE-2022-39197: critical Cobalt Strike bug could lead to RCE attacks
The maintainers of the Cobalt Strike project, HelpSystems has pushed out-of-band software updates to its adversary simulation tool to contain a critical-impact security vulnerability.
The flaw, now assigned the identifier CVE-2022-39197, has been described as an XSS vulnerability in the teamserver that affected the Cobalt Strike version prior to 4.7.1.
Cobalt Strike was one of the first public red team command and control frameworks. In 2020, HelpSystems acquired Cobalt Strike to add to its Core Security portfolio and pair with Core Impact. Today, Cobalt Strike is the go-to red team platform for many U.S. government, large businesses, and consulting organizations. However, Cobalt Strike is also widely used by hackers, including ransomware gangs, to infiltrate targeted networks.
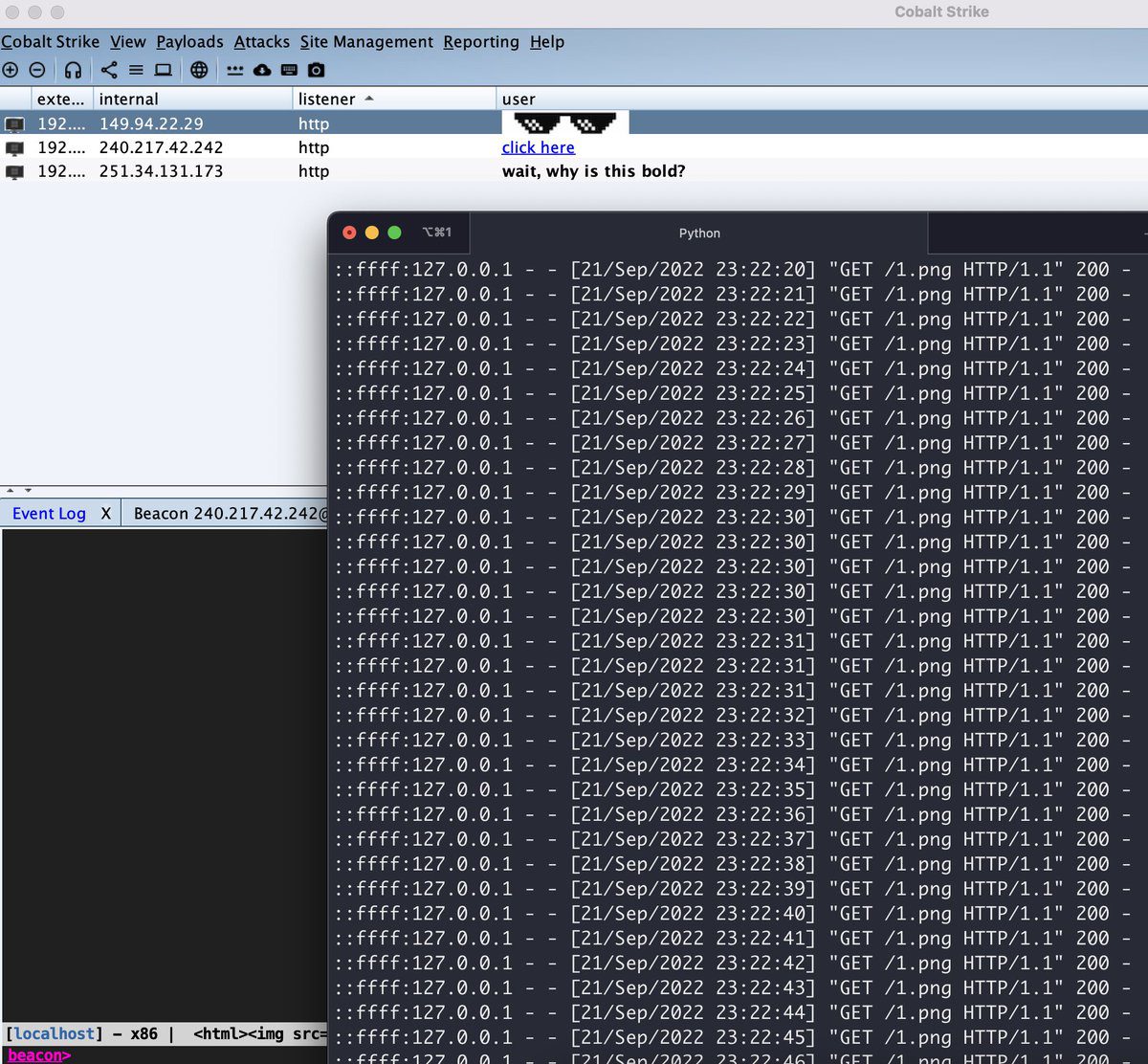
“This would allow an attacker to set a malformed username in the Beacon configuration, allowing them to remotely execute code,” the advisory noted. An independent researcher identified as “Beichendream”, has been credited with reporting the flaw to HelpSystems.

Image: buffaloverflow
To patch this flaw, the new Cobalt Strike version added a new property (limits.beacons_xssvalidated is set to true) to the TeamServer.prop file. Users of the library are recommended to upgrade to Cobalt Strike version 4.7.1 to mitigate any potential threats.