TAG-100’s Global Espionage Campaign: Exploiting Open-Source Tools
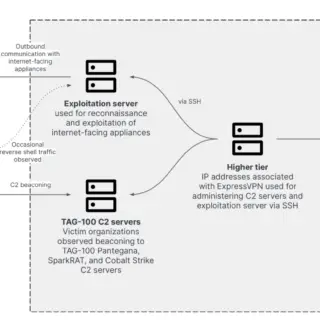
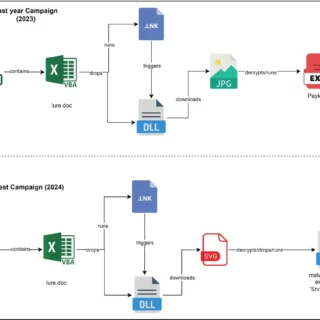
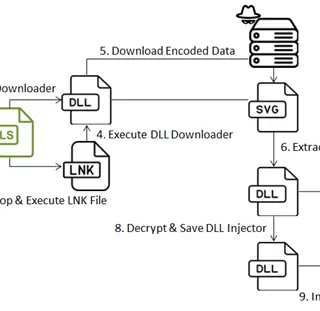
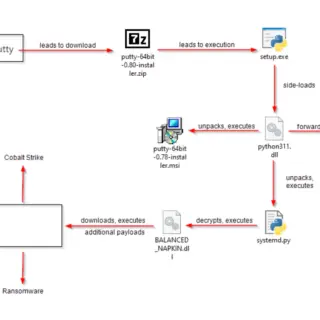
A newly identified cyberespionage group, dubbed TAG-100 by cybersecurity firm Recorded Future, has been linked to a series of sophisticated attacks targeting high-profile government, intergovernmental, and private sector organizations worldwide. The group’s modus operandi...