Microsoft late Thursday raised the alarm after discovering Chinese cyber-espionage operators chaining two zero-day exploits to achieve remote code execution on affected Microsoft Exchange servers.
Microsoft said the two under-attack vulnerabilities exist in Microsoft Exchange Server Server 2013, 2016, and 2019, widely deployed products in the Windows ecosystem.
“The first vulnerability, identified as CVE-2022-41040, is a Server-Side Request Forgery (SSRF) vulnerability, while the second, identified as CVE-2022-41082, allows remote code execution (RCE) when PowerShell is accessible to the attacker,” Microsoft said.
“At this time, Microsoft is aware of limited targeted attacks using the two vulnerabilities to get into users’ systems.”
CVE-2022-41040 was caused by improper validation of user-supplied input within the Exchange OWA interface. By sending a specially-crafted request, an attacker could exploit this vulnerability to conduct SSRF attack.
CVE-2022-4104 and CVE-2022-41082 are being tracked by the Zero Day Initiative as ZDI-CAN-18333 (CVSS score: 8.8) and ZDI-CAN-18802 (CVSS score: 6.3). Microsoft warned that an authenticated attacker can launch code execution attacks. The company did not share details on the pre-patch attacks.
According to Vietnamese cybersecurity company GTSC, who first reported the active attacks, the attacks are likely originating from a Chinese hacking group owing to the web shell’s encoding.
“We detected webshells, mostly obfuscated, being dropped to Exchange servers,” the company noted. “Using the user-agent, we detected that the attacker uses Antsword, an active Chinese-based open source cross-platform website administration tool that supports web shell management.”
How to migrate Zero-day Vulnerabilities in Microsoft Exchange Server
Microsoft wrote:
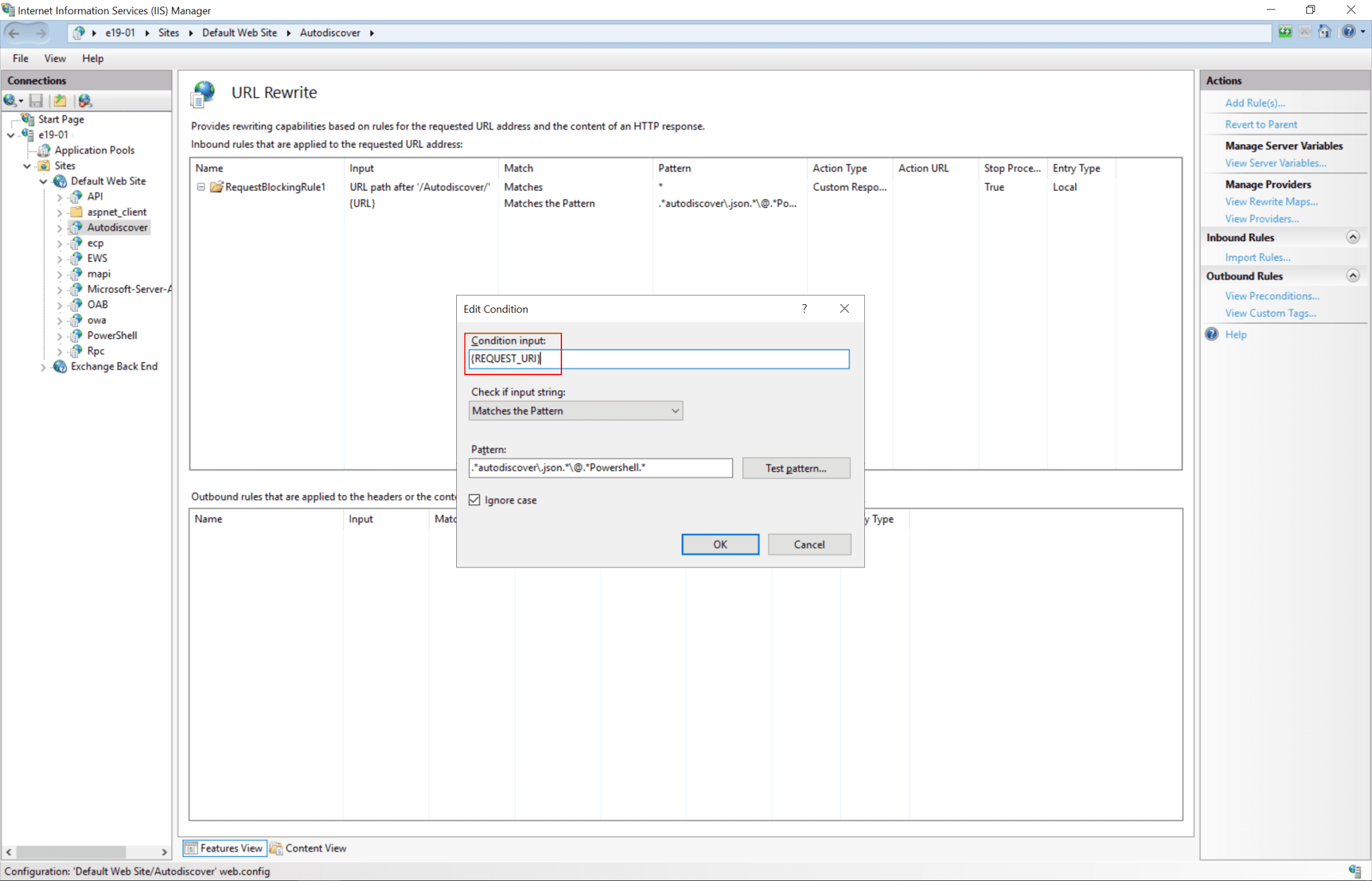
“On premises Microsoft Exchange customers should review and apply the following URL Rewrite Instructions and block exposed Remote PowerShell ports. The current mitigation is to add a blocking rule in “IIS Manager -> Default Web Site -> Autodiscover -> URL Rewrite -> Actions” to block the known attack patterns.”

The user needs to do the following step:
- Open the IIS Manager.
- Expand the Default Web Site.
- Select Autodiscover.
- In the Feature View, click URL Rewrite.
- In the Actions pane on the right-hand side, click Add Rules.
- Select Request Blocking and click OK.
- Add String “.*autodiscover\.json.*\@.*Powershell.*” (excluding quotes) and click OK.
- Expand the rule and select the rule with the Pattern “.*autodiscover\.json.*\@.*Powershell.*” and click Edit under Conditions.
- Change the condition input from {URL} to {REQUEST_URI}
Authenticated attackers who can access PowerShell Remoting on vulnerable Exchange systems will be able to trigger RCE using CVE-2022-41082. Blocking the ports used for Remote PowerShell can limit these attacks.
- HTTP: 5985
- HTTPS: 5986
System administrators can also consider running the following PowerShell command to search through their IIS logs to determine if their Exchange Servers have been compromised by the zero-day vulnerabilities:
Get-ChildItem -Recurse -Path <Path_IIS_Logs> -Filter “*.log” | Select-String -Pattern ‘powershell.*autodiscover\.json.*\@.*200
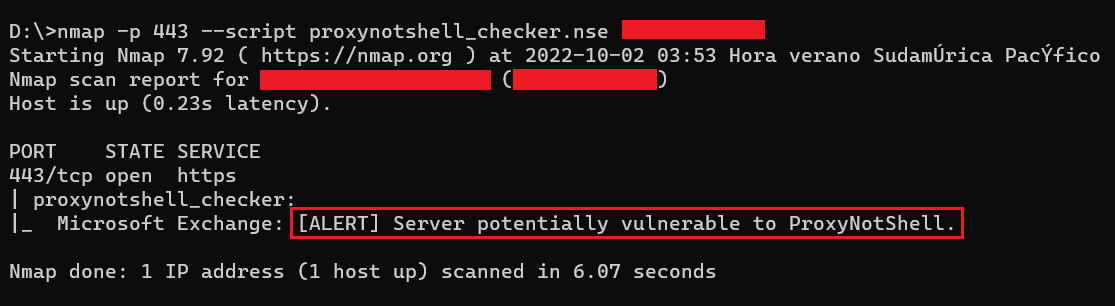
You can use the Nmap script to scan for servers potentially vulnerable to these vulnerabilities: