A high-risk security vulnerability has been found in the open-source Prometheus systems and service monitoring system that could be exploited by an attacker to access systems and data.
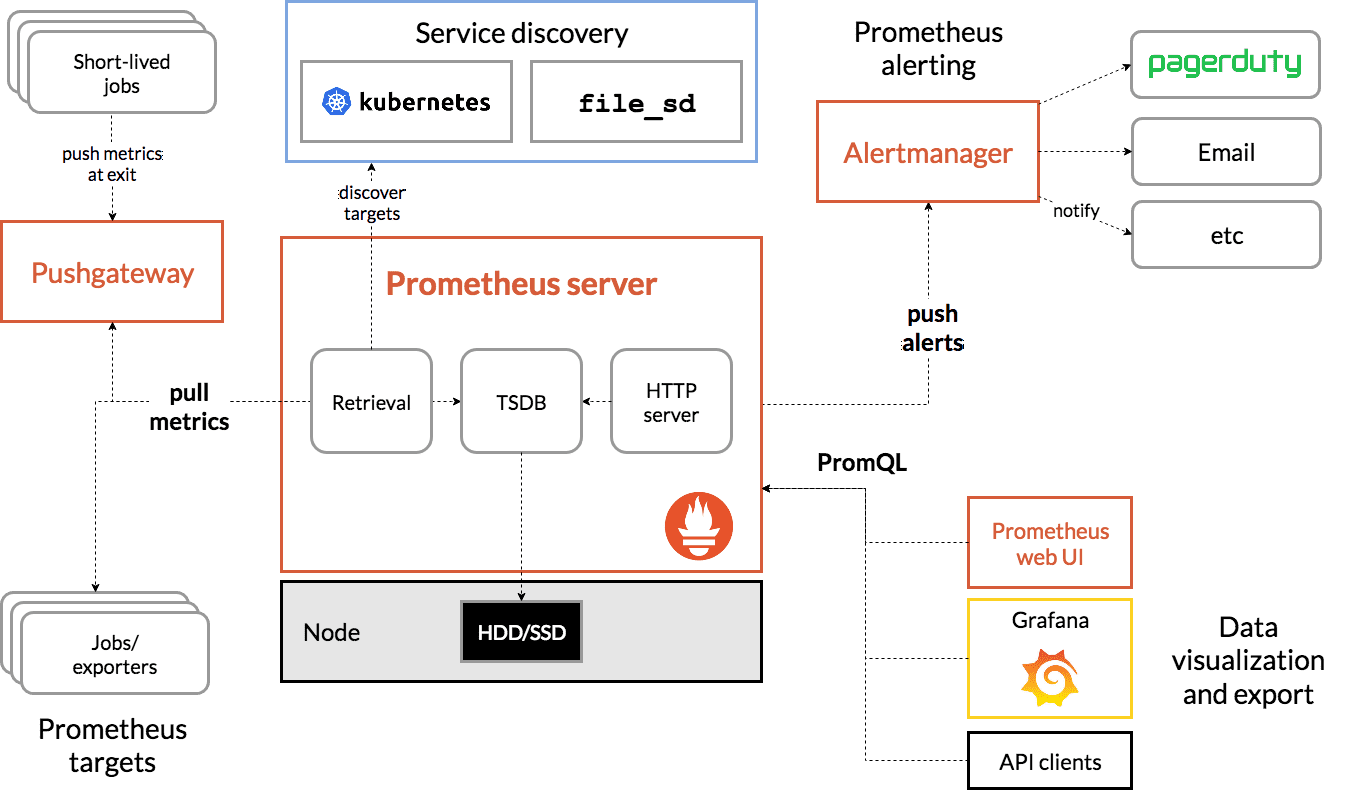
Prometheus, a Cloud Native Computing Foundation project, is a systems and service monitoring system. It collects metrics from configured targets at given intervals, evaluates rule expressions, displays the results, and can trigger alerts when specified conditions are observed.

Tracked as CVE-2022-46146 (CVSS score: 7.2), the flaw exists in the exporter toolkit that allows hackers who know the hashed password to authenticate against Prometheus.
“Prometheus can be secured by a web.yml file that specifies usernames and hashed passwords for basic authentication. Passwords are hashed with bcrypt, which means that even if you have access to the hash, it is very hard to find the original password back. However, a flaw in the way this mechanism was implemented in the exporter toolkit makes it possible with people who know the hashed password to authenticate against Prometheus,” the developer roidelapluie noted in an advisory posted on GitHub today.
“A request can be forged by an attacker to poison the internal cache used to cache the computation of hashes and make subsequent requests successful. This cache is used in both happy and unhappy scenarios in order to limit side channel attacks that could tell an attacker if a user is present in the file or not.”
Luckily, an attacker must have access to the hashed password, stored on disk, to bypass the authentication. So the impact of the CVE-2022-46146 is lower.
The weakness was identified and reported by Lei Wan, following which the project maintainers released patches (2.37.4 (LTS) and 2.40.4).