On March 27, 2023, a groundbreaking research paper titled “Framing Frames: Bypassing Wi-Fi Encryption by Manipulating Transmit Queues” was made public, exposing vulnerabilities in the 802.11 Wi-Fi standard. These vulnerabilities could allow an attacker to spoof a targeted wireless client and redirect frames present in the transmit queues in an access point to an attacker-controlled device. In this article, we dissect the mechanics of this opportunistic attack and explore possible mitigations to safeguard your network from this threat.
The Vulnerability: CVE-2022-47522
Dubbed “MacStealer,” the attack targets Wi-Fi networks with malicious insiders and exploits client isolation bypasses (CVE-2022-47522). It can intercept traffic at the MAC layer, even if clients are prevented from communicating with each other. This vulnerability impacts Wi-Fi networks that utilize client isolation, Dynamic ARP inspection (DAI), and other methods designed to protect clients from attacking one another.
Cisco was the first vendor to acknowledge the vulnerability, stating that the attacks outlined in the research paper could be successful against Cisco Wireless Access Point products and Cisco Meraki products with wireless capabilities.
Understanding the Attack
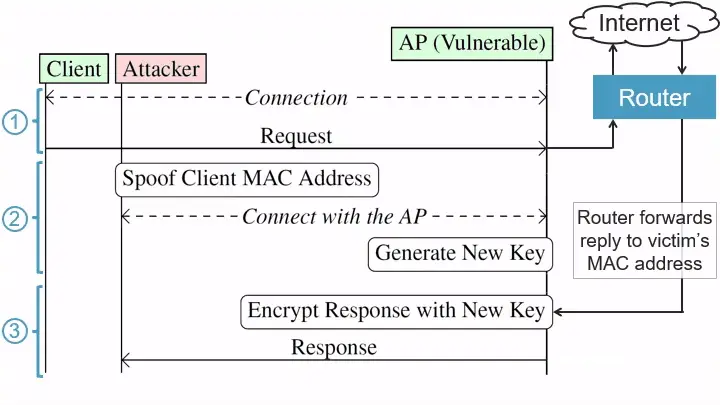
The CVE-2022-47522 security flaw lies in the fact that client authentication and packet routing in Wi-Fi networks operate independently of each other. While authentication relies on passwords, usernames, 802.1X identities, and/or certificates, packet routing is based on MAC addresses. A malicious insider can exploit this discrepancy by disconnecting a victim and connecting to the network using the victim’s MAC address and the attacker’s credentials. Consequently, any packets still en route to the victim, such as website data, will be received by the attacker instead.
Breaking Down the Attack

This attack consists of three primary steps:
- Lure the Victim: The attacker waits for the victim to connect to a vulnerable Access Point (AP) and sends a request to an internet server, such as an HTTP request to a plaintext website.
- Steal the Victim’s Identity: The attacker disconnects the victim from the network before the server’s response reaches the AP. The attacker then spoofs the victim’s MAC address and connects to the network using their own credentials.
- Intercept the Response: The AP associates the attacker’s encryption keys with the victim’s MAC address, allowing the attacker to receive any pending traffic intended for the victim.
It is important to note that intercepted traffic may be protected by higher-layer encryption, such as TLS and HTTPS. Nevertheless, even if higher-layer encryption is being used, this attack still reveals the IP address that a victim is communicating with. This in turn reveals the websites that a victim is visiting, which can be sensitive information on its own.
The attack is identical against Enterprise WPA1, WPA2, and WPA3 networks. This is because the attack does not exploit any cryptographic properties of Wi-Fi but instead abuses how a network determines to which client packets should be sent, i.e., routed,.
Recommendations
To prevent MAC address stealing, 802.1X authentication and RADIUS extensions can be used. Protecting the gateway’s MAC address, implementing Management Frame Protection (802.11w), and using VLANs are also potential mitigations. Cisco recommends using policy enforcement mechanisms through a system like Cisco Identity Services Engine (ISE), which can restrict network access by implementing Cisco TrustSec or Software Defined Access (SDA) technologies. Cisco also recommends implementing transport layer security to encrypt data in transit whenever possible because it would render the acquired data unusable by the attacker.
In conclusion, the attack outlined in the “Framing Frames” paper is a concerning vulnerability that could allow attackers to intercept and potentially view sensitive information being transmitted over Wi-Fi networks. It is important for organizations to take the necessary precautions, such as using recommended mitigations and employing robust security measures, to ensure the safety and security of their networks