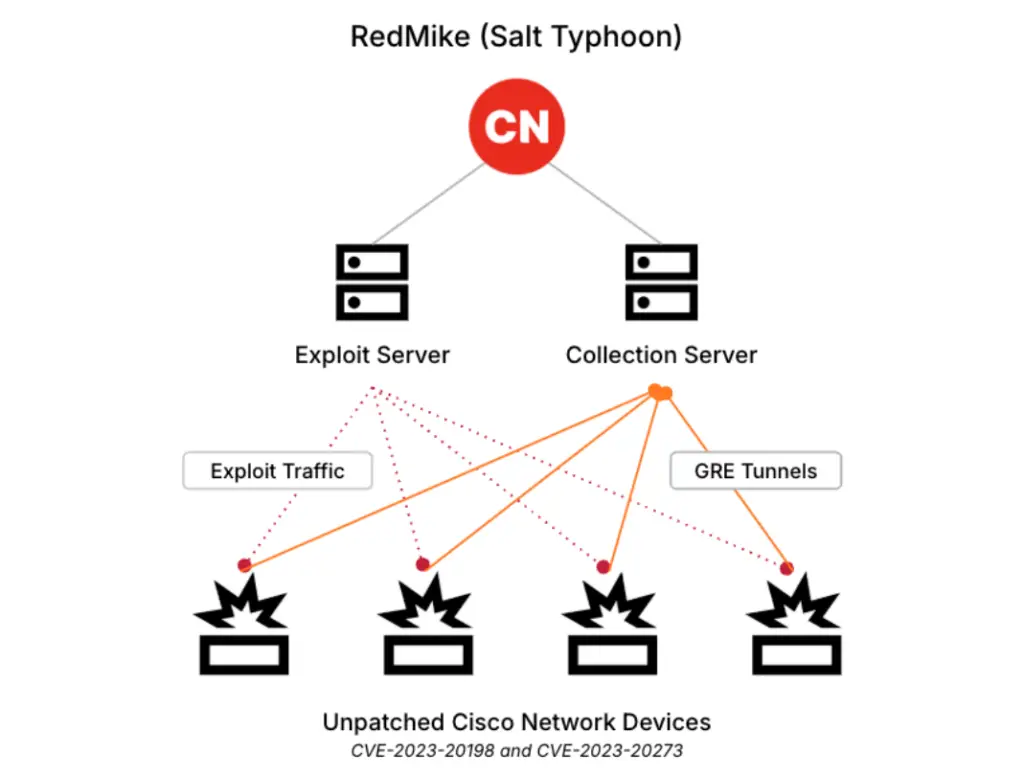
RedMike Cisco network device exploitation infrastructure (Source: Recorded Future)
Cybersecurity researchers at Insikt Group have identified an ongoing cyber espionage campaign by RedMike (also tracked as Salt Typhoon) targeting telecommunications providers worldwide. This Chinese state-sponsored group is exploiting privilege escalation vulnerabilities (CVE-2023-20198 and CVE-2023-20273) in Cisco IOS XE devices, enabling them to gain persistent access to critical network infrastructure.
Despite U.S. sanctions and extensive media coverage, RedMike continues to target high-value organizations, including a U.S.-based affiliate of a UK telecom company, a South African telecommunications provider, and over 1,000 Cisco devices globally between December 2024 and January 2025.
“RedMike’s exploitation of telecommunications infrastructure goes beyond technical vulnerabilities and represents a strategic intelligence threat,” Insikt Group warns.
The Cisco IOS XE web user interface (UI) vulnerability (CVE-2023-20198) allows attackers to escalate privileges and create a new high-level user account. This is the first stage of RedMike’s attack, enabling them to execute arbitrary commands on vulnerable devices.
Once initial access is established, RedMike exploits CVE-2023-20273, an associated privilege escalation flaw, to obtain root privileges. With full administrative access, the attackers can modify device configurations and establish persistent backdoors.
“RedMike reconfigures the device, adding a generic routing encapsulation (GRE) tunnel for persistent access,” Insikt Group reports.
By leveraging GRE tunnels, RedMike maintains covert, encrypted communication channels, enabling them to exfiltrate data undetected while bypassing security controls.
RedMike’s targets extend beyond telecommunications companies. Universities across Argentina, Bangladesh, Indonesia, Malaysia, Mexico, the Netherlands, Thailand, the United States, and Vietnam have also been compromised, particularly those engaged in research on telecommunications, engineering, and emerging technologies.
Among the affected institutions are:
- University of California, Los Angeles (UCLA) – U.S.
- Technische Universiteit Delft (TU Delft) – Netherlands
- Universitas Negeri Malang – Indonesia
- University of Malaya – Malaysia
- Universidad Nacional Autónoma – Mexico
“Universities are prime targets for Chinese state-sponsored threat activity groups to acquire valuable research data and intellectual property,” the report notes, citing previous cyberattacks by APT40, RedGolf (APT41), and RedBravo (APT31) on academic institutions.
Insikt Group confirmed that seven Cisco devices communicating with RedMike’s infrastructure were linked to:
- A U.S.-based affiliate of a UK telecommunications provider
- A major South African telecommunications company
- An Italian internet service provider (ISP)
- A large telecom provider in Thailand
These compromised devices provide RedMike with persistent access to high-value networks, facilitating data interception, surveillance, and potential service disruption.
“RedMike’s targeting of lawful intercept programs and U.S. political figures highlights the strategic intelligence objectives behind these operations,” Insikt Group explains.
RedMike’s campaign is part of a larger shift by Chinese state-sponsored hackers toward exploiting unpatched public-facing appliances for initial access.
“Sophisticated Chinese threat activity groups have shifted heavily toward exploiting these devices for initial access over the past five years,” the report states.
Related Posts:
- CVE-2023-20273: Cisco IOS XE Zero-Day Vulnerability
- Cisco Zero-Day Exploit Code Goes Public: Patch Now or Face Total System Takeover
- CVE-2023-20198 (CVSS:10): Cisco IOS XE Zero Day Vulnerability
- Threat Actors Exploit GitHub to Spread Malware, Targeting Multiple Operating Systems
- UK National Cyber Security Centre: Do not use ZTE equipment and services in the telecommunications industry