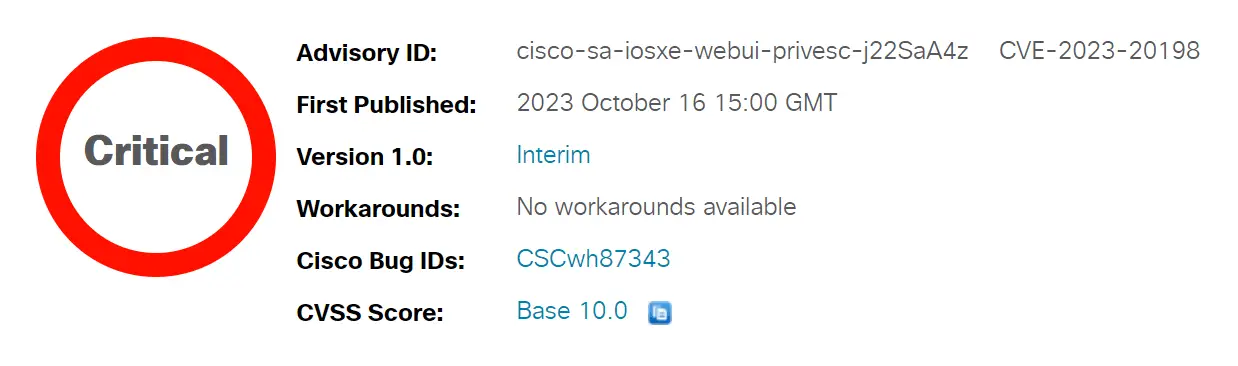
Cisco unveiled a previously undisclosed vulnerability within the Web UI feature of its IOS XE Software. This flaw allows unauthenticated attackers to remotely craft an account on the affected system with the highest privilege level, level 15. Once the attacker possesses such an account, they can exercise complete control over the affected system. Bearing the identifier CVE-2023-20198, this vulnerability carries a maximum CVSS score of 10, signifying its critical severity.

“Cisco is aware of active exploitation of this vulnerability,” the company wrote.
The Web UI, an integral component of Cisco’s offering, is an embedded GUI-based tool designed to facilitate system management. Its user-friendly interface aids users in configuring, monitoring, and troubleshooting systems without requiring extensive CLI knowledge. As a default feature, it doesn’t require any additional licenses or activation.
However, its convenience also makes it an attractive target. If exposed to the internet or untrusted networks, the Web UI becomes vulnerable. The threat becomes especially dire when the HTTP Server feature, enabling the Web UI, is switched on using the `ip http server` or `ip http secure-server` commands.
To ascertain if a system has the CVE-2023-20198 vulnerability:
1. Access the system and execute `show running-config | include ip http server|secure|active`.
2. Check for the presence of the `ip http server` or `ip http secure-server` commands. If either is visible, the Web UI feature is activated.
However, there are conditions that render the vulnerability non-exploitable. If the configuration contains `ip http active-session-modules none` alongside the `ip http server` command or `ip http secure-active-session-modules none` with the `ip http secure-server` command, exploitation is averted.
For systems possibly compromised:
1. Monitor system logs for specific log messages indicating unauthorized activities, especially with unfamiliar usernames.
2. Execute the command provided by Cisco Talos: `curl -k -X POST “https://systemip/webui/logoutconfirm.html?logon_hash=1”`. The return of a hexadecimal string implies the presence of a malicious implant.
It’s imperative to note that there are currently no workarounds addressing the CVE-2023-20198 vulnerability.
Cisco’s sleuths identified the earliest traces of possible malicious activity on September 28, 2023. The strange behavior of a customer device revealed an authorized user’s suspicious account creation from an irregular IP address. This event seemingly ended by October 1, but on October 12, another surge of related activities was detected. This time, unauthorized access led to the deployment of an implant: the configuration file “cisco_service.conf”. These back-to-back occurrences seemed linked, with the October incidents likely building upon the earlier ones.
In light of these events, Cisco emphatically advises users to deactivate the HTTP Server feature on all systems exposed to the internet. To achieve this, use the `no ip http server` or `no ip http secure-server` commands. Following this, save the running-configuration to prevent accidental reactivation of the feature.