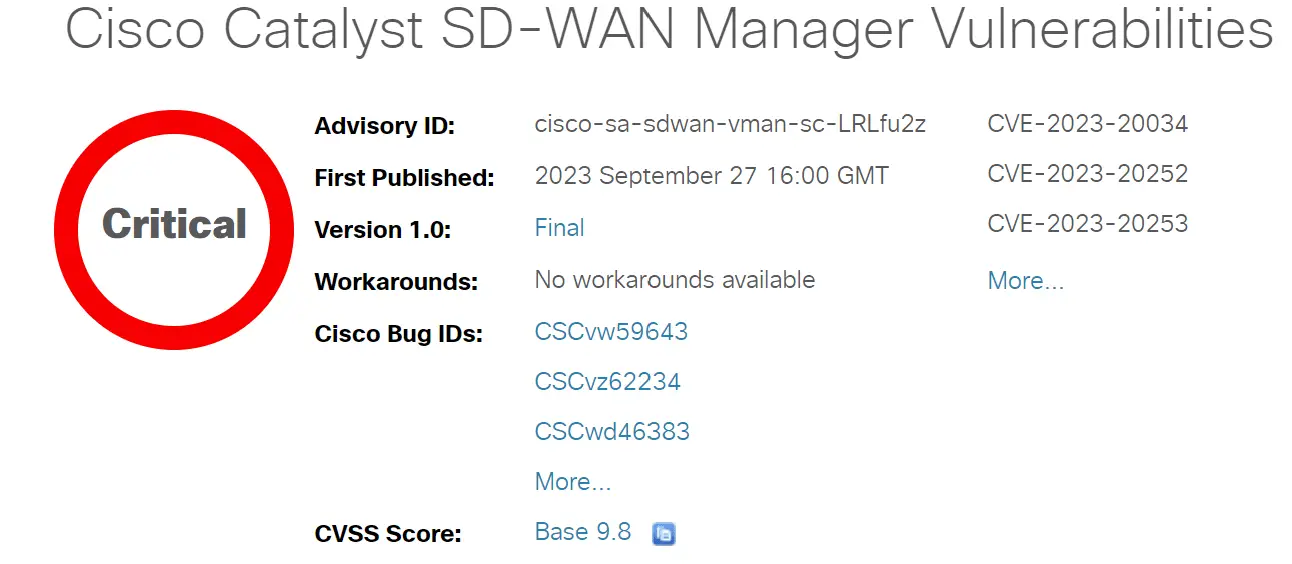
Cisco Catalyst SD-WAN Manager, formerly Cisco SD-WAN vManage, is a network management platform that provides a centralized view and control of Cisco SD-WAN networks. It is a critical component of many organizations’ SD-WAN infrastructure, and its security is essential to protecting their networks.
Recently, Cisco has released security updates to address multiple vulnerabilities in Cisco Catalyst SD-WAN Manager. These vulnerabilities could allow an attacker to access an affected instance, cause a denial of service (DoS) condition, or disclose sensitive information.
1. CVE-2023-20252: Unauthorized Access Vulnerability (CVSS 9.8)
This vulnerability resides in the Security Assertion Markup Language (SAML) APIs of Cisco Catalyst SD-WAN Manager, allowing an unauthenticated, remote attacker to gain unauthorized access as an arbitrary user. Exploitation of this vulnerability is possible by directly sending requests to the SAML APIs, leading to unauthorized access to the application.
2. CVE-2023-20253: Unauthorized Configuration Rollback Vulnerability (CVSS 8.4)
An authenticated, local attacker with read-only privileges can exploit this vulnerability in the CLI of Cisco Catalyst SD-WAN Manager. The attacker can bypass authorization and roll back controller configurations, which could then be deployed to downstream routers.
3. CVE-2023-20034: Information Disclosure Vulnerability (CVSS 7.5)
This vulnerability in the access control implementation for Elasticsearch could allow an unauthenticated, remote attacker to access the Elasticsearch database with the privileges of the Elasticsearch user, potentially viewing sensitive database content.
4. CVE-2023-20254: Authorization Bypass Vulnerability (CVSS 7.2)
This vulnerability could permit an authenticated, remote attacker to access another tenant that is being managed by the same Cisco Catalyst SD-WAN Manager instance, providing they send a crafted request to an affected system.
5. CVE-2023-20262: Denial of Service Vulnerability (CVSS 5.3)
In this vulnerability, an unauthenticated, remote attacker could cause a process crash in the SSH service, resulting in a DoS condition for SSH access only.
Cisco has released security updates to address all of the vulnerabilities listed above. The details are listed in the following table:
| Release | CVE-2023-20252 Critical SIR |
CVE-2023-20253 High SIR |
CVE-2023-20034 High SIR |
CVE-2023-20254 High SIR |
CVE-2023-20262 Medium SIR |
|---|---|---|---|---|---|
| Earlier than 20.3 | Not affected. | Migrate to a fixed release. | Migrate to a fixed release. | Migrate to a fixed release. | Migrate to a fixed release. |
| 20.3 | Not affected. | Migrate to a fixed release. | 20.3.4 | Migrate to a fixed release. | 20.3.7 |
| 20.4 | Not affected. | Migrate to a fixed release. | Migrate to a fixed release. | Migrate to a fixed release. | Migrate to a fixed release. |
| 20.5 | Not affected. | Migrate to a fixed release. | Migrate to a fixed release. | Migrate to a fixed release. | Migrate to a fixed release. |
| 20.6 | Not affected. | 20.6.2 | 20.6.1 | 20.6.3.4 | Migrate to a fixed release. |
| 20.7 | Not affected. | 20.7.1 | 20.7.1 | Migrate to a fixed release. | Migrate to a fixed release. |
| 20.8 | Not affected. | 20.8.1 | Not affected. | Migrate to a fixed release. | Migrate to a fixed release. |
| 20.9 | 20.9.3.41 | 20.9.1 | Not affected. | 20.9.3.2 | 20.9.3 |
| 20.10 | Not affected. | 20.10.1 | Not affected. | 20.10.1.2 | Migrate to a fixed release. |
| 20.11 | Migrate to a fixed release.1 | 20.11.1 | Not affected. | 20.11.1.2 | 20.11.1 |
| 20.12 | Not affected. | Not affected. | Not affected. | Not affected. | 20.12.1 |
Ensuring the security of systems is an ongoing process and requires continuous vigilance. It is essential for organizations utilizing Cisco Catalyst SD-WAN Manager to update their software to the latest versions to mitigate these vulnerabilities. Additionally, regular monitoring and assessment of systems can further enhance security and prevent unauthorized access and potential damage to the systems.
The Cisco PSIRT assures there have been no malicious uses or public announcements regarding these vulnerabilities. However, users should act promptly, updating their systems to ensure maximum security.