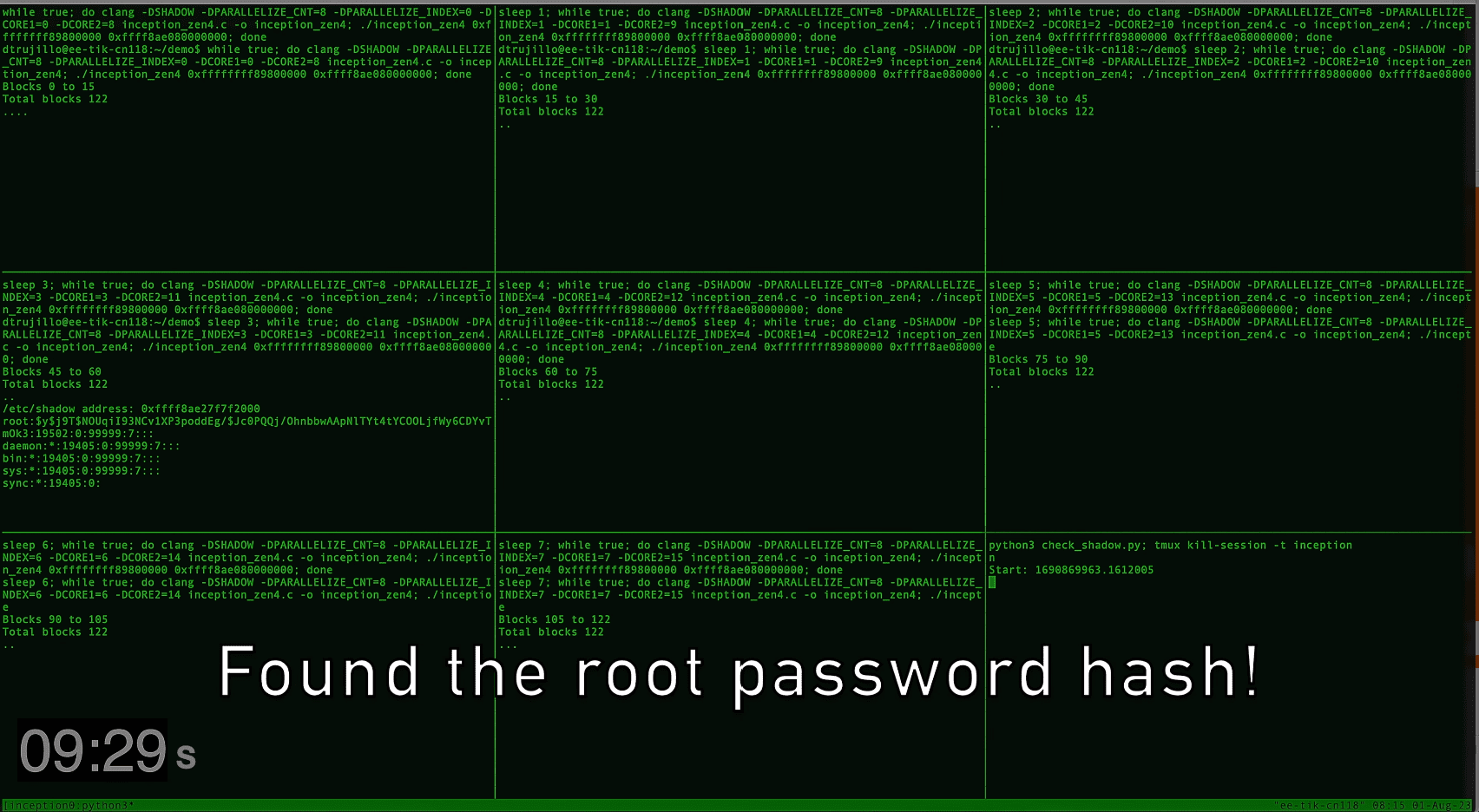
The latest security vulnerability has been drawn on AMD’s Zen CPUs, where researchers at ETH Zurich have identified a novel and potent transient execution attack known as ‘Inception,’ tracked as CVE-2023-20569. This attack has exposed a vulnerability in a broad range of AMD Zen CPUs, including the most recent models.
Inception Attack: A Deeper Look
Speculative execution is a feature present in modern processors that boosts CPU performance by predicting what will be executed next. Although it’s vital for performance, it can leave traces that savvy attackers can analyze to obtain otherwise secured data.
Inception combines two techniques – the older ‘Phantom speculation’ (CVE-2022-23825) and the new ‘Training in Transient Execution’ (TTE) – to create a formidable attack that can leak privileged secrets and data.

Phantom Speculation and TTE
Phantom speculation enables attackers to create a speculative execution period at arbitrary XOR instructions, triggering mispredictions without needing any branch at the source.
TTE, on the other hand, manipulates future mispredictions by injecting new predictions to create exploitable speculative executions. The combination of these two turns supposedly benign transient windows into dangerous ones.
How Does Inception Work?
Inception plants an “idea” in the CPU while it’s in a sense “dreaming,” causing it to take incorrect actions. This approach allows Inception to hijack the transient control-flow of return instructions on all AMD Zen CPUs, resulting in speculative execution at an attacker-controlled address, potentially leading to information disclosure.
Similarities with Previous Attacks
Inception’s nature aligns with previous attacks like Spectrev2 and Branch Type Confusion (BTC)/RetBleed. However, to exploit, an attacker must have extensive knowledge and control over the target. AMD believes this vulnerability is potentially exploitable locally through malware.
Vulnerability Across Models and Mitigation
All AMD Zen-based Ryzen and EPYC CPUs, from Zen 1 to Zen 4, are vulnerable to Phantom and Inception. While Intel CPUs may be impacted by TTE variants, Phantom is hard to exploit on Intel thanks to specific mitigations.
The proof-of-concept developed by ETH Zurich is applicable to any OS using vulnerable AMD CPUs. A strategy to counteract this would be to fully flush the branch predictor state when switching between distrusting contexts. However, this introduces a substantial performance overhead, ranging from 93.1% to 216.9% on older CPUs.
Recommendations and Updates
AMD has released microcode updates for Zen 3 and Zen 4 CPUs, and owners of Zen-based processors are urged to install the latest updates. AMD has been transparent with its updates and plans, recommending either standalone µcode patches or BIOS updates.
For Zen and Zen 2 CPU architectures, no patch is needed, as these designs are already built to flush branch-type predictions.
Inception exposes a new class of transient execution attacks that poses a significant threat but can be addressed through vigilance and immediate action. AMD has already taken steps to mitigate the CVE-2023-20569 flaw, and users must heed the company’s recommendations to secure their systems.
While no exploit has been observed outside the research environment, the unveiling of Inception serves as a sobering reminder of the persistent and evolving challenges in the cybersecurity landscape. It underscores the necessity for continuous collaboration between researchers and tech companies and the relentless pursuit of security in an increasingly interconnected digital world.