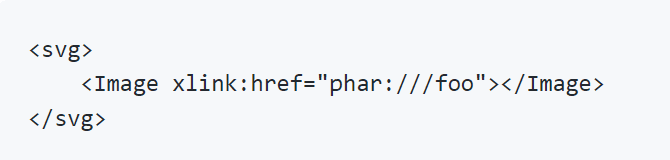
A critical-severity security flaw has been disclosed in the open-source Dompdf PHP library that, if successfully exploited, could lead to remote code execution on a target server.
“An attacker might be able to exploit the vulnerability to call arbitrary URL with arbitrary protocols, if they can provide a SVG file to dompdf. In PHP versions before 8.0.0, it leads to arbitrary unserialize, that will leads at the very least to an arbitrary file deletion, and might leads to remote code execution, depending on classes that are available,” developer Bsweeney wrote in the advisories.