
MinIO, the high-performance object storage solution, is widely used for machine learning, analytics, and application data workloads due to its compatibility with the Amazon S3 cloud storage service. Despite its popularity and growing adoption, recent security vulnerabilities have been discovered that could pose significant risks to users. These flaws have recently been identified in MinIO deployments: CVE-2023-28432, CVE-2023-28434, and CVE-2023-28433.

- CVE-2023-28432: Information Disclosure in Cluster Deployment
This vulnerability, with a CVSS score of 7.5, impacts MinIO deployments in a cluster configuration, specifically in versions RELEASE.2019-12-17T23-16-33Z to RELEASE.2023-03-20T20-16-18Z. Due to this security flaw, MinIO returns all environment variables, including sensitive information like MINIO_SECRET_KEY and MINIO_ROOT_PASSWORD, leading to information disclosure. The PoC for this flaw has been released publicly.
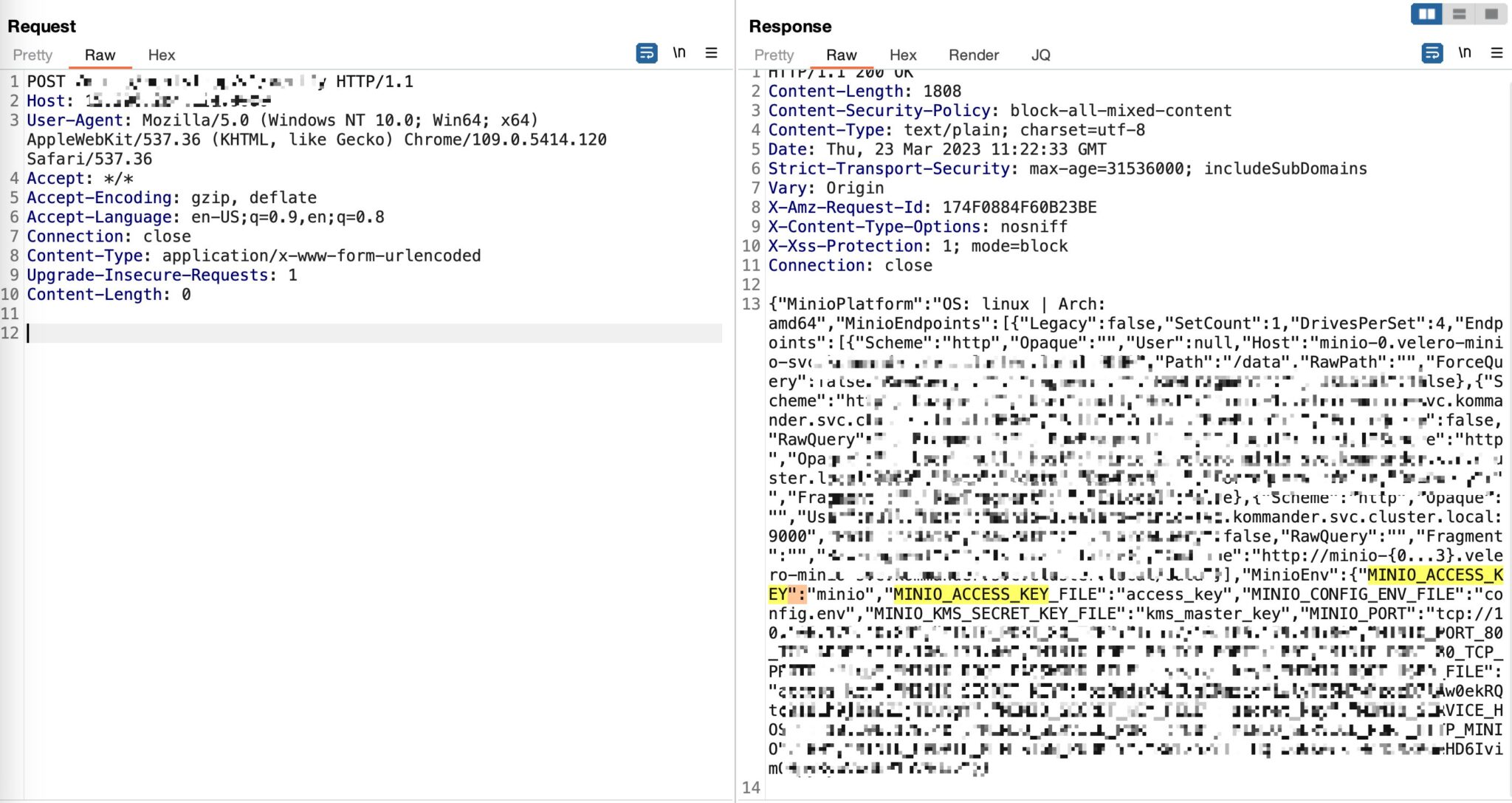
Affected users: All users of distributed deployments.
Solution: Upgrade to RELEASE.2023-03-20T20-16-18Z. Unfortunately, there are no known workarounds for this vulnerability.
- CVE-2023-28434: Privilege Escalation on Linux/MacOS
With a CVSS score of 8.8, this vulnerability allows an attacker to bypass metadata bucket name checking and insert an object into any bucket while processing PostPolicyBucket. To execute this attack, the attacker requires credentials with arn:aws:s3:::* permission and enabled Console API access. This vulnerability affects MinIO versions before RELEASE.2023-03-20T20-16-18Z on Linux and MacOS platforms.
Affected users: All Linux and MacOS users with enabled Console API access.
Solution: Upgrade to RELEASE.2023-03-20T20-16-18Z. As a workaround, enable browser API access and disable MINIO_BROWSER=off. Note that browser API access must be enabled for this workaround to be effective.
- CVE-2023-28433: Privilege Escalation on Windows via Path Separator Manipulation
This vulnerability, also with a CVSS score of 8.8, affects all MinIO Windows users prior to version RELEASE.2023-03-20T20-16-18Z. The issue lies in MinIO’s failure to filter the \ character, which allows for arbitrary object placement across buckets. Consequently, a low-privileged user with access to a specific bucket can exploit this vulnerability to create an admin user.
Affected users: All Windows users.
Solution: Upgrade to RELEASE.2023-03-20T20-16-18Z. There are no known workarounds for this vulnerability.
Conclusion
Security vulnerabilities in MinIO, such as the ones discussed in this article, can have severe implications for users and their data. It is crucial to keep your deployments up-to-date and implement recommended security measures to protect your systems. By staying informed and promptly addressing any identified vulnerabilities, you can continue to use MinIO with confidence, leveraging its high-performance capabilities for your machine learning, analytics, and application data workloads.