Image: huntress
In an increasingly connected world, security vulnerabilities are a persistent concern for businesses and individuals alike. The recent discovery of a compromised 3CX Desktop App highlights the continued prevalence of supply chain attacks, raising alarms for companies that rely on third-party solutions. In this article, we will delve into the specifics of CVE-2023-29059, a high-profile security vulnerability affecting multiple versions of the 3CX Desktop App, and discuss the implications of this attack for businesses worldwide.
The 3CX Desktop App Compromise:
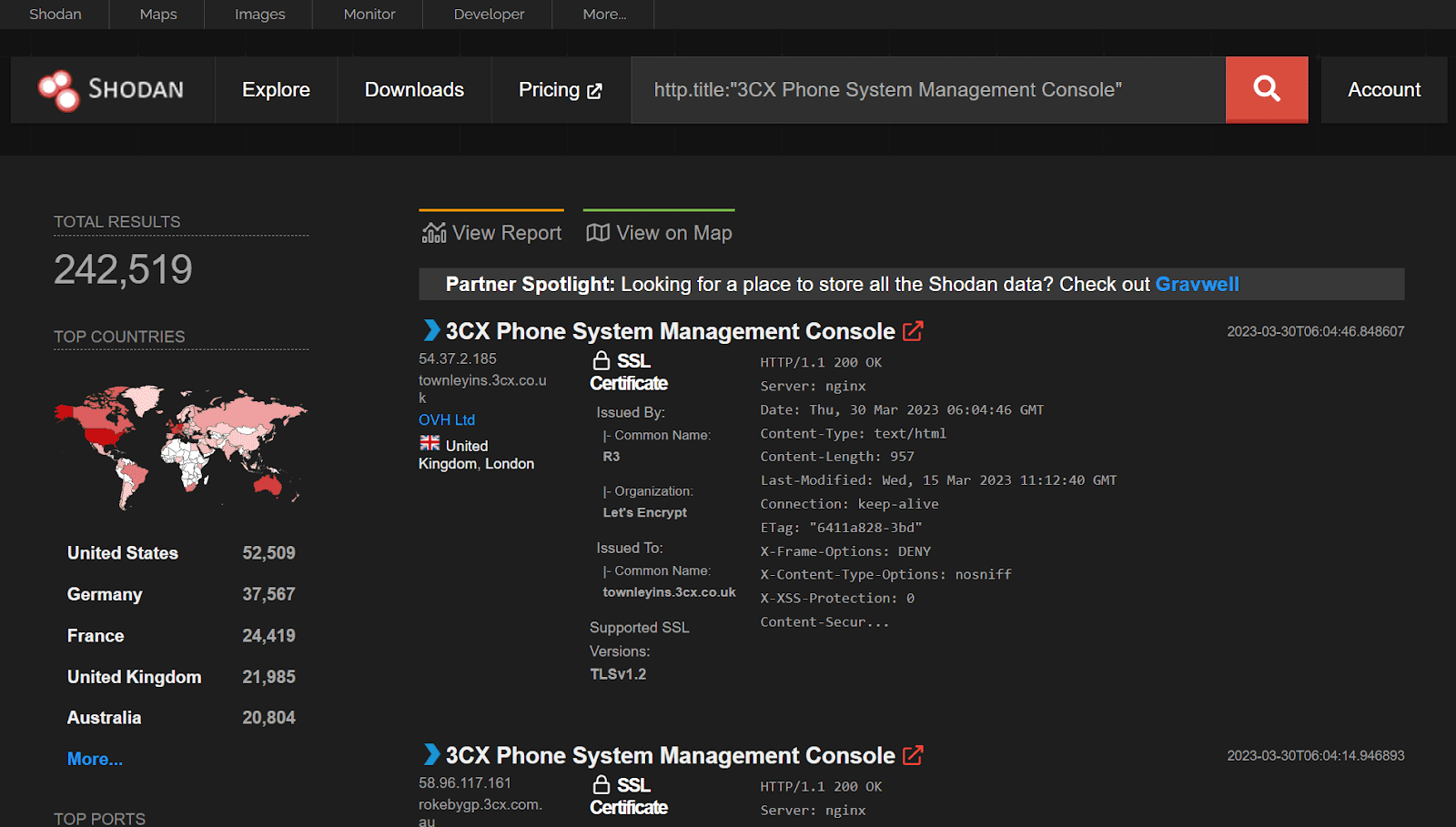
On March 29, reports emerged of a code-level compromise within the 3CX Desktop App, a multi-platform softphone application used by over 12 million daily users across more than 190 countries. This legitimate signed file from VoIP/IP PBX solutions provider 3CX had been trojanized, marking the latest high-profile supply chain attack since the SolarWinds and Kaseya incidents. Huntress reported that there are 242,519 publicly exposed 3CX phone management systems.

Affected Platforms and Versions:
The affected platforms include the Electron framework versions of the 3CX Desktop App for both macOS (versions 18.11.1213, 18.12.402, 18.12.407, and 18.12.416) and Windows (versions 18.12.407 and 18.12.416). Although initial reports suggested all platforms were compromised, subsequent investigations have narrowed the focus to these specific versions.
The Multi-Stage Attack:
The trojanized 3CX Desktop App is part of a multi-stage attack that utilizes a malicious sideloaded DLL, containing instructions and a payload within another DLL via an encrypted blob. This blob also contains shellcode, which attempts to pull ICO files from GitHub that contain various URIs for downloading the payload, ultimately loading and installing it to the target environment.
Mitigation and Best Practices:
In response to the attack, 3CX has revoked the certificate for the previous Windows app version and is working on a new release. As for the macOS version, no current status has been provided. In the meantime, 3CX recommends users migrate to the PWA app, a web-based alternative unaffected by the supply chain attack.
The CVE-2023-29059 incident serves as a stark reminder of the ever-present threat of supply chain attacks. Businesses need to remain vigilant and prioritize the implementation of robust security measures. By staying informed about emerging threats and adopting best practices, companies can better protect their networks and valuable data from potential breaches.