In the ever-evolving world of cybersecurity, it is crucial to stay ahead of emerging threats. One such security vulnerability has been discovered in cPanel, the widely-used web hosting control panel software. With an astounding 1.4 million installations exposed to the internet, the potential fallout from this vulnerability is significant.
CVE-2023-29489, a reflected cross-site scripting (XSS) vulnerability, was recently identified by researchers Shubham Shah from Assetnote and Sergey Temnikov. Worryingly, this vulnerability can be exploited without any authentication and affects even cPanel management ports that are not exposed externally.
The Vulnerability Unveiled
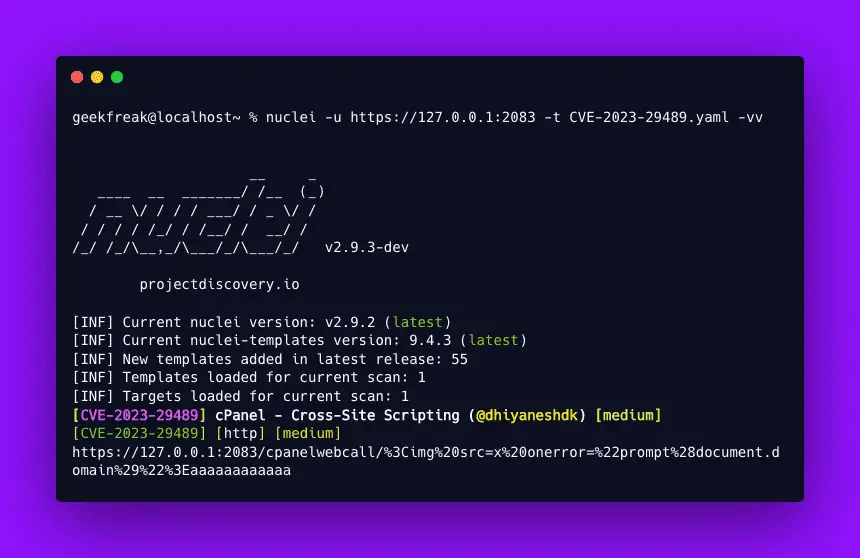
At the root cause of CVE-2023-29489 lies an invalid webcall ID that can contain XSS content. When this content is displayed on the error page for cpsrvd, it is not appropriately escaped, thus enabling the XSS attack.
The consequences of this vulnerability are alarming. Malicious actors can execute arbitrary JavaScript pre-authentication on almost every port of a web server using cPanel in its default setup. This is due to the proxy rules that allow the /cpanelwebcall/ directory to be accessed even on ports 80 and 443.
Potential Impact
The presence of this vulnerability on cPanel management ports opens the door for attackers to hijack a user’s cPanel session. Once they have assumed the identity of an authenticated cPanel user, it’s typically a breeze for the attacker to upload a web shell and gain command execution.
More concerning is that this XSS vulnerability isn’t just limited to cPanel management ports – it also extends to applications running on ports 80 and 443. This means that millions of websites managed by cPanel are at risk, even if their management ports are not exposed externally.
Proof of Concept
The researchers provided the following proof of concept URLs to demonstrate the vulnerability:
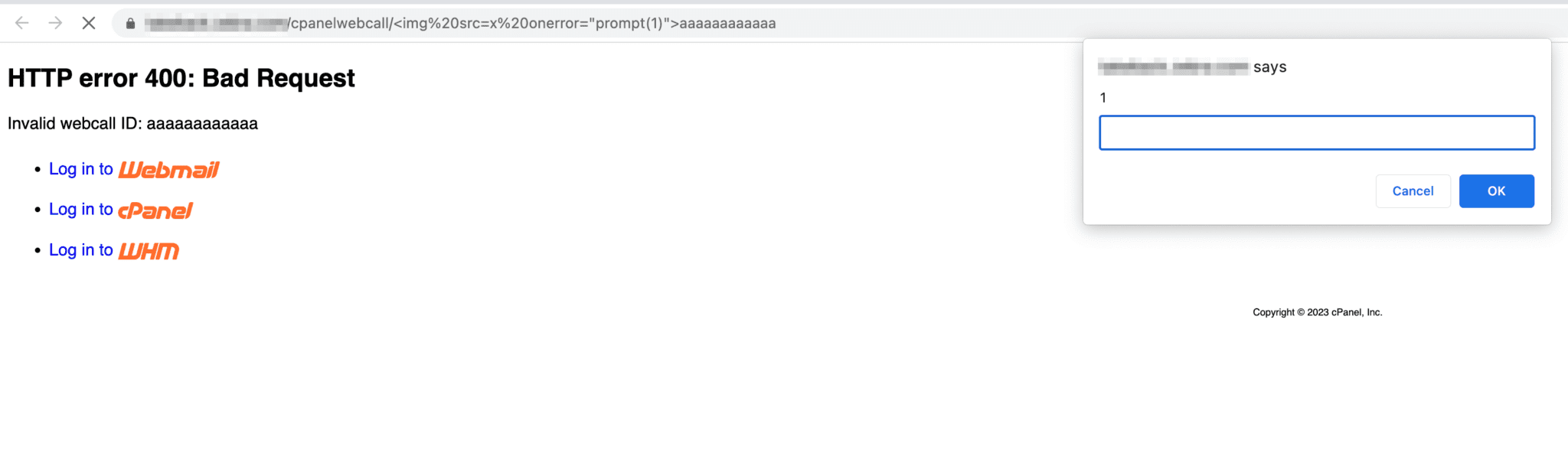
- http://example.com/cpanelwebcall/<img%20src=x%20onerror=”prompt(1)”>aaaaaaaaaaaa
- http://example.com:2082/cpanelwebcall/<img%20src=x%20onerror=”prompt(1)”>aaaaaaaaaaaa
- http://example.com:2086/cpanelwebcall/<img%20src=x%20onerror=”prompt(1)”>aaaaaaaaaaaa
- http://example.com:2082/cpanelwebcall/<img%20src=x%20onerror=”prompt(1)”>aaaaaaaaaaaa
How to Remediate
To address this security vulnerability, users are advised to upgrade their cPanel installations to any of the following versions or above:
- 11.109.9999.116
- 11.108.0.13
- 11.106.0.18
- 11.102.0.31
Unfortunately, many cPanel installations remain vulnerable as they do not have the auto-update feature enabled. It is essential for users to take immediate action to protect their websites.
As one of the most popular web hosting control panel software, cPanel requires increased attention from the security researcher community. While this particular vulnerability can be mitigated by updating to the latest version, there may be other yet-to-be-discovered vulnerabilities lurking within cPanel’s vast attack surface.