Image: vulncheck
Recently, VulnCheck unveiled in a report a critical privilege escalation vulnerability (CVE-2023-30799, CVSS score 9.1) present within the MikroTik RouterOS system. This vulnerability enables attackers to execute arbitrary code, thereby gaining complete control over the affected devices. Preliminary estimates suggest hundreds of thousands of devices are potentially impacted.
At its core, this vulnerability facilitates the escalation of privileges from an administrator to a super administrator. Despite the exploitation of this vulnerability necessitating authentication, acquiring credentials for the RouterOS system is considerably simpler than anticipated. This is primarily because the MikroTik RouterOS operating system lacks any safeguards against brute-force password attacks, and prior to October 2021, it came with a well-known default ‘admin’ user whose password was an empty string. It was only upon the release of RouterOS version 6.49 that administrators were prompted to update this blank password.

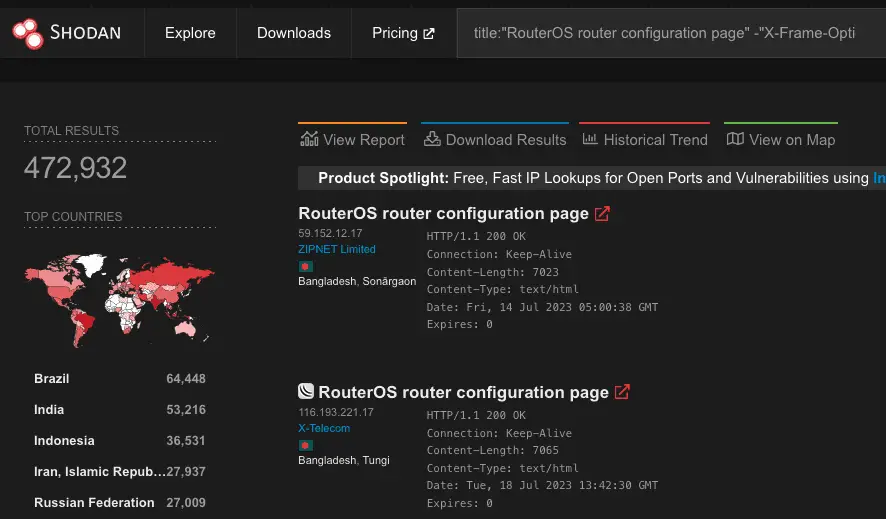
Researchers employed Shodan to gauge the CVE-2023-30799 vulnerability’s impact, discovering that around 474,000 devices, due to their exposed web-based administration page, were vulnerable to attack. However, given that this vulnerability can also be exploited via the Mikrotek management client Winbox, a total of 926,000 devices were exposed, making the actual impact significantly larger.
The researchers further noted that such attacks, once successful, are challenging to detect. RouterOS’s Web and Winbox interfaces implement a custom encryption scheme that neither Snort nor Suricata can decrypt or inspect. Once attackers establish a connection with a device, they can easily cloak their presence within the RouterOS user interface.
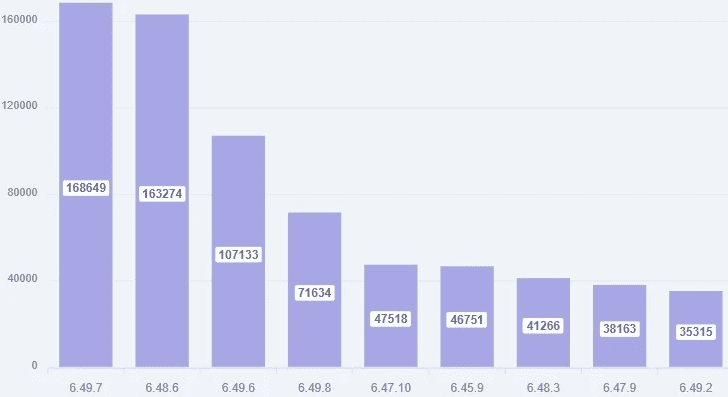
Typically, miscreants exploit such vulnerabilities to construct distributed denial-of-service (DDoS) botnets, such as Mēris. To mitigate the risk of attack, users are advised to promptly upgrade to the latest version (6.49.8 or 7.x) to patch this vulnerability. Additional mitigative measures may include deleting the MikroTik management interface, restricting the IP addresses permitted for administrator login, disabling Winbox and Web interfaces and using SSH, and configuring SSH to employ a public/private key rather than a password.