A server humming in the digital backdrop, a potent Content Management System (CMS) operating, an unwary user typing away on their keyboard – this is a scene commonplace across the world wide web. For Grav CMS, a file-based web platform admired for its speed, simplicity, and flexibility, the illusion of security has been shattered with the revelation of four critical vulnerabilities. With zero installation requirements and a robust package management system, Grav’s easy deployment and maintenance were its strength. But the same features that endeared Grav to users now serve as conduits for potential cyber threats.
CVE-2023-34253 (CVSS score of 7.2): Grav Server-side Template Injection (SSTI) via Denylist Bypass Vulnerability
The first vulnerability (CVE-2023-34253) is a Server-side Template Injection (SSTI) exploiting a denylist bypass. Introduced in commit 9d6a2d, the denylist aimed to block dangerous functions from being executed via injected malicious templates. However, this safety measure was insufficient, and there were multiple avenues for subversion, including using unbanned unsafe functions, capitalised callable names, or fully-qualified names for referencing callables.
The astute security researcher jacobsoo discovered this flaw, stating that a low-privilege attacker with login access to the Grav Admin panel and page creation or update permissions could exploit it to achieve remote code execution.
CVE-2023-34448 (CVSS score of 7.2): Grav Server-side Template Injection (SSTI) via Twig Default Filters
The second critical vulnerability (CVE-2023-34448) also falls under the SSTI category, exploiting Twig’s default filters. A patch designed to fix an earlier vulnerability (CVE-2022-2073) failed to block other built-in functions provided by Twig’s Core Extension. As a result, these functions could potentially invoke arbitrary unsafe commands, leading to remote code execution. Again, the eyes behind the discovery belong to jacobsoo. The affected population remains the same – those with admin access or non-admin users given access to the Grav admin panel and page creation or update rights.
CVE-2023-34252 (CVSS score of 7.2): Grav Server-side Template Injection (SSTI) via Insufficient Validation in filterFilter
The third vulnerability (CVE-2023-34252), discovered by the same vigilant researcher, jacobsoo, is another SSTI via Insufficient Validation in filterFilter. It revolves around a logical flaw in GravExtension.filterFilter(). It only performs validation against a denylist of unsafe functions when the argument passed to filter is a string. Bypassing the validation check is as simple as passing an array as a callable argument, offering another avenue for remote code execution for those with the right permissions.
CVE-2023-34251 (CVSS score of 9.1): Server Side Template Injection (SSTI)
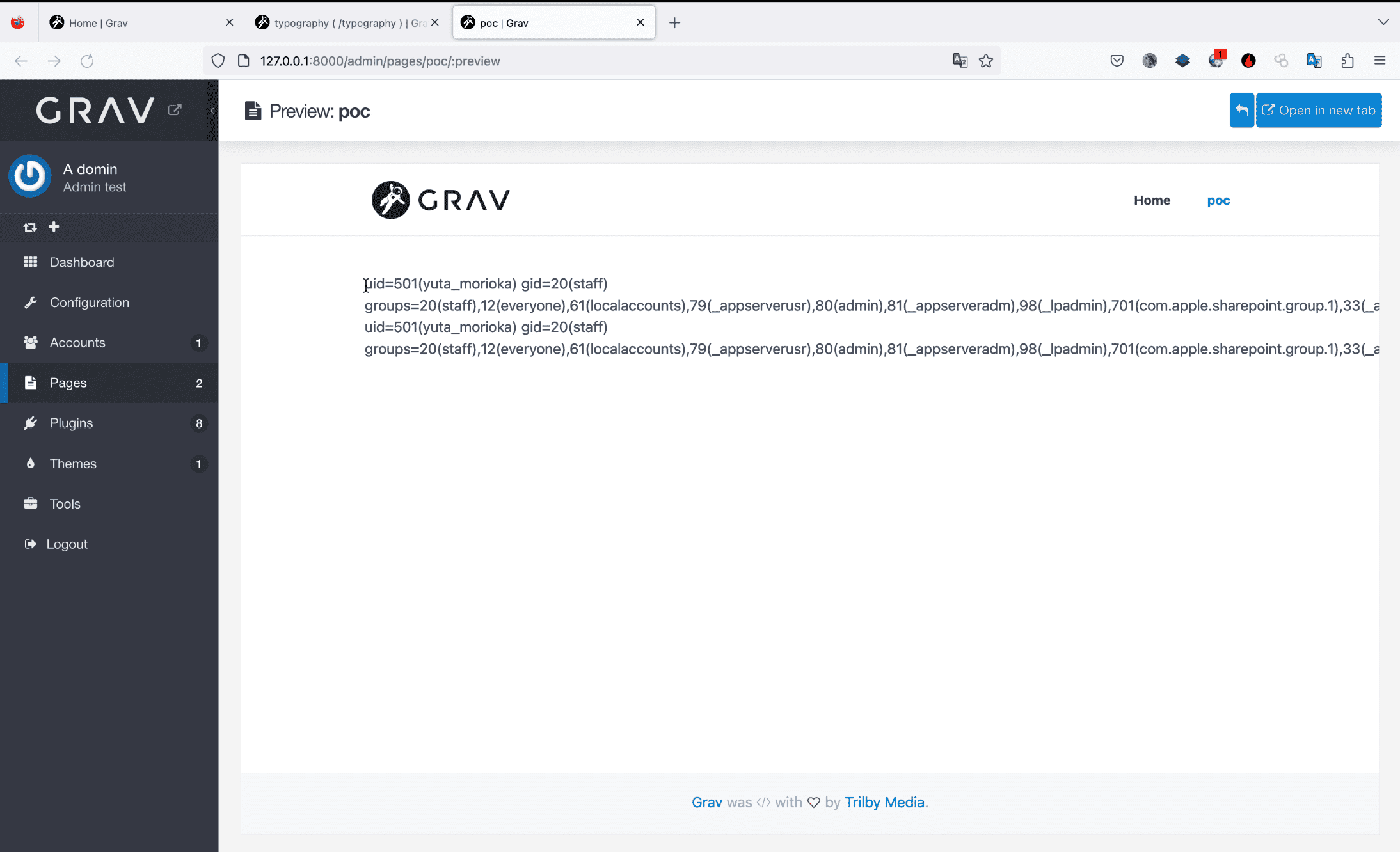
Finally, we have CVE-2023-34251, a vulnerability with the highest CVSS score of 9.1, indicating its high severity. It’s an SSTI vulnerability that allows Remote Code Execution by embedding malicious PHP code on the administrator screen. The flaw was discovered by security researcher scgajge12. To exploit this, an attacker only needs page editing privileges. The proof-of-concept is chillingly simple: log in, access the edit screen of the default page, open the console, and execute arbitrary commands.

These vulnerabilities underscore the stark reality of web security – the constant vigilance required from both developers and users. Without immediate action, these security flaws can expose Grav CMS users to potential cyber-attacks, data breaches, and an array of security nightmares. It’s crucial for Grav CMS users and administrators to keep abreast with the latest security patches, frequently review user permissions, and encourage responsible CMS usage.