Your Boot Logo is Hackable: LogoFAIL Exposes Millions of Devices
In the intricate web of modern computing, a new threat has emerged, casting a shadow over the seemingly simple process of booting up a computer. This threat, known as LogoFAIL, comprises a series of vulnerabilities that target the very heart of a computer’s booting routine – the Unified Extensible Firmware Interface (UEFI), an integral part of any modern computer system.
Researchers at Binarly, a firmware supply chain security platform, have unearthed a critical weakness within the image parsing libraries used by various UEFI code from different vendors. The vulnerabilities, collectively named LogoFAIL, lie dormant within the routines that display branding logos during the boot process. These flaws, spanning across x86 and ARM architectures, have far-reaching implications, affecting a myriad of devices regardless of their operating system – be it Windows or Linux.
The vulnerabilities, tracked under CVE designations CVE-2023-5058, CVE-2023-39538, CVE-2023-39539, and CVE-2023-40238, pose a significant risk. They can be exploited to hijack the execution flow of the booting process, potentially leading to the delivery of bootkits. This could result in unauthorized access and control over the entire system, bypassing traditional layers of security.
- CVE-2023-39538 (CVSS score of 7.5): AMI AptioV contains a vulnerability in BIOS where a User may cause an unrestricted upload of a BMP Logo file with dangerous type by Local access. A successful exploit of this vulnerability may lead to a loss of Confidentiality, Integrity, and/or Availability.
- CVE-2023-39539 (CVSS score of 7.5): AMI AptioV contains a vulnerability in BIOS where a User may cause an unrestricted upload of a PNG Logo file with dangerous type by Local access. A successful exploit of this vulnerability may lead to a loss of Confidentiality, Integrity, and/or Availability.
- CVE-2023-40238: A LogoFAIL issue was discovered in BmpDecoderDxe in Insyde InsydeH2O with kernel 5.2 before 05.28.47, 5.3 before 05.37.47, 5.4 before 05.45.47, 5.5 before 05.53.47, and 5.6 before 05.60.47 for certain Lenovo devices. Image parsing of crafted BMP logo files can copy data to a specific address during the DXE phase of UEFI execution. This occurs because of an integer signedness error involving PixelHeight and PixelWidth during RLE4/RLE8 compression.
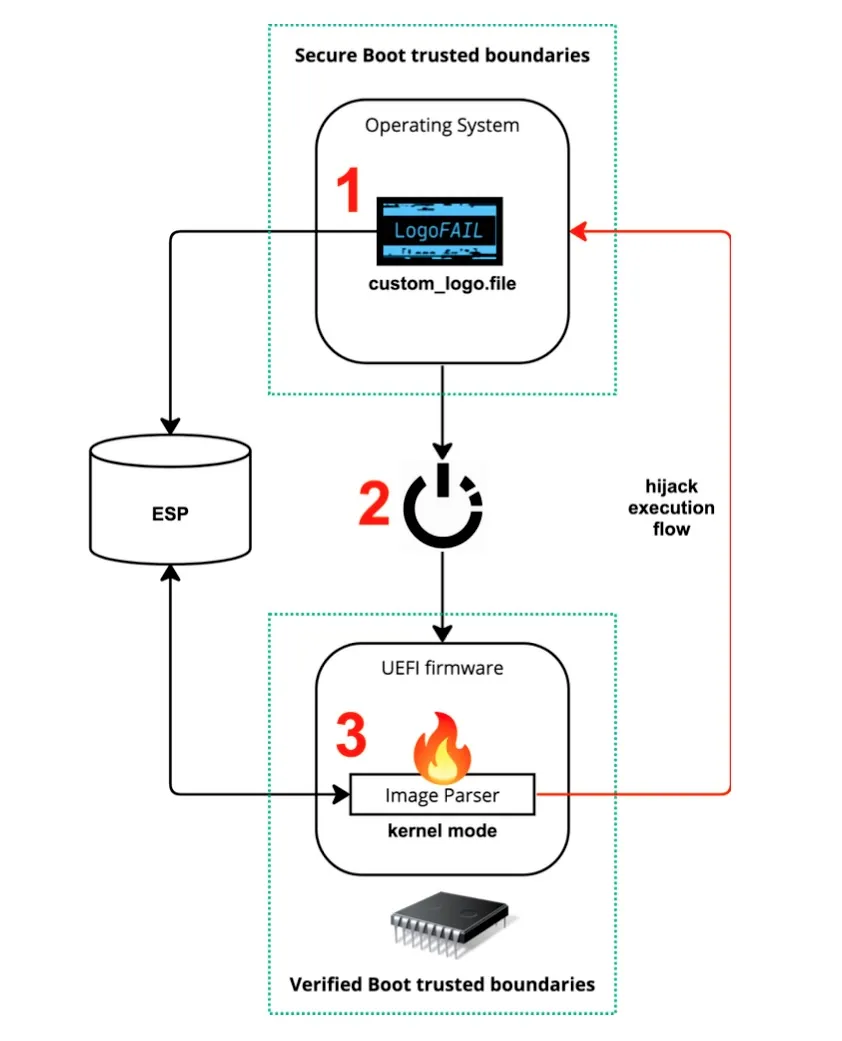
The exploitation occurs during the ‘Driver Execution Environment’ (DXE) phase of the boot process, a critical stage where various boot and runtime services are loaded, and hardware components are initialized. In this phase, LogoFAIL replaces the UEFI boot-up logo with an exploit, which then loads during the DXE phase, gaining control over the system before the operating system even starts.
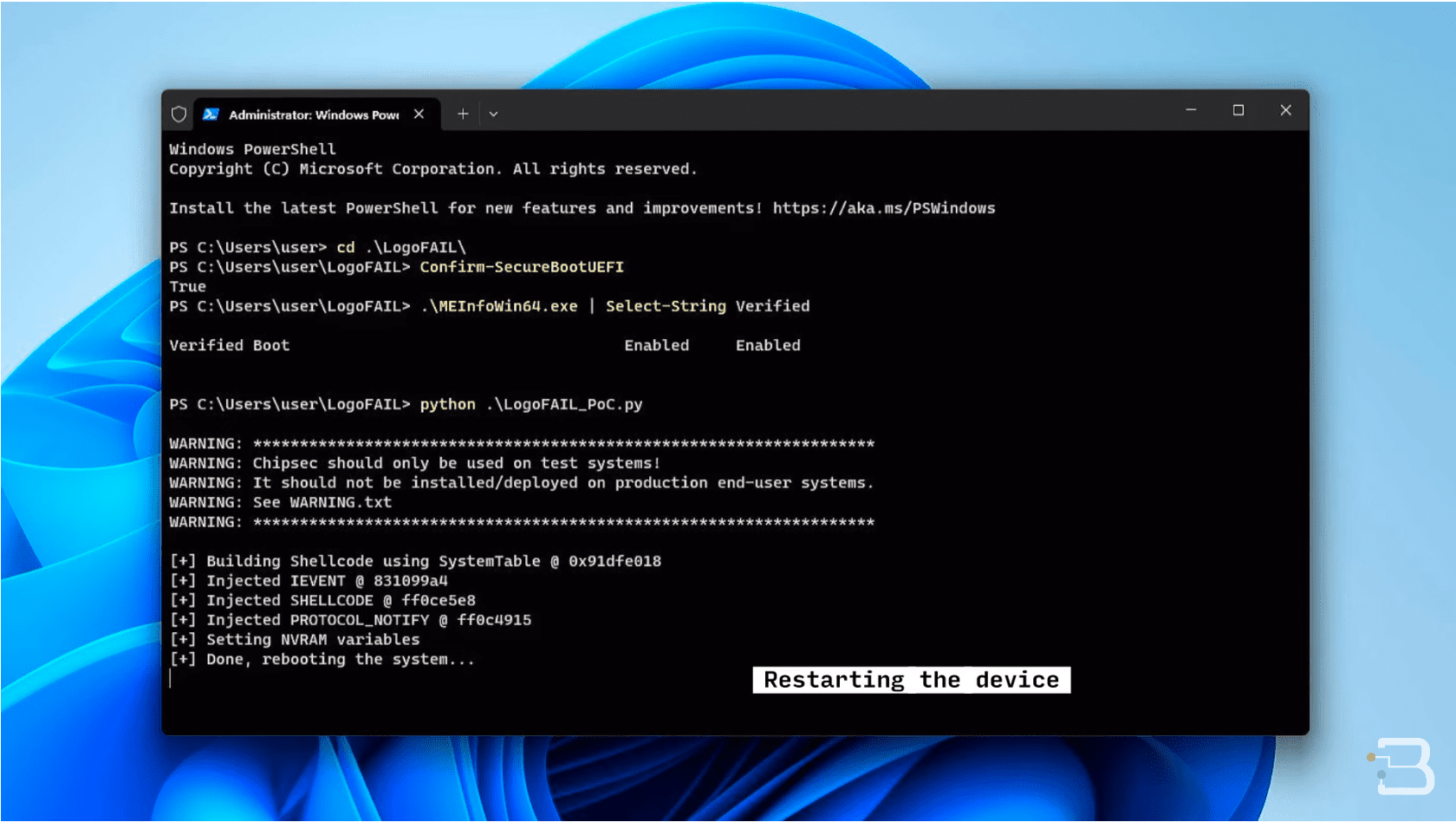
Binarly has demonstrated this vulnerability in action. A proof-of-concept (PoC) exploit showed how an attacker with administrative permissions on the operating system could escalate privileges to the firmware level. The exploit was successfully executed on a Lenovo ThinkCentre M70s, equipped with an Intel 11th generation CPU, with all the latest security features like Intel Secure Boot and Boot Guard enabled.
As Alex Matrodov, the founder and CEO of Binarly, points out, this vulnerability is particularly dangerous because it bypasses all CPU, operating system, and third-party security solutions. The exploit, being UEFI-level and not stored on the storage drive, remains undetected and unremovable, even after an OS reformat. This makes it a formidable delivery mechanism for bootkits.
In response to this discovery, vendors such as AMI, Insyde, Lenovo, and others have issued advisories. However, given the widespread nature of the issue, there is no complete list of affected companies. Users are urged to check with their OEM/motherboard manufacturer to ascertain if their systems are vulnerable.
The most effective defense against LogoFAIL attacks is to install UEFI security updates provided by device or motherboard manufacturers. Additionally, configuring UEFI to utilize multiple layers of defenses, including Secure Boot, Intel Boot Guard, and, when available, Intel BIOS Guard, is recommended. Similar protective measures are advised for devices running on AMD or ARM CPUs.





