Ivanti Avalanche, a mighty tool in the realm of Mobile Device Management (MDM), serves as a beacon, guiding organizations through the maze of managing an array of devices, from robust warehouse scanners to sleek retail tablets.
The issue assigned the CVE identifier CVE-2023-41474, discovered in Avalanche Server v6.3.4.153, was revealed by the security researcher JBalanza. It presents itself as a limited unauthenticated path traversal vulnerability. In simpler terms, this means that unauthorized attackers can stealthily navigate through certain directories and access files within the system.
In a default setup, attackers can access files located under `C:\\PROGRAM DATA\\Wavelink\\AVALANCHE\\Web\ webapps\AvalancheWeb`. However, only specific file extensions like `.xml` or `.html` are at risk, contingent on `.htaccess` rules.
An attacker can exploit this weakness using a URL pattern: `<domain>/AvalancheWeb//faces/javax.faces.resource/<file>?loc=<directory>`.
For instance, they could potentially access the `web.xml` file in the `WEB-INF` directory. The impact of such an attack cannot be understated. Simple tools like wget or curl can be utilized to execute this exploit, making it dangerously accessible.
In a real-world scenario, CVE-2023-41474 can be a gateway to more sinister activities. An unauthenticated attacker could access configuration settings and internal information. While this may seem of low confidentiality impact at first glance, the true danger lies in the potential for session hijacking and complete server compromise.
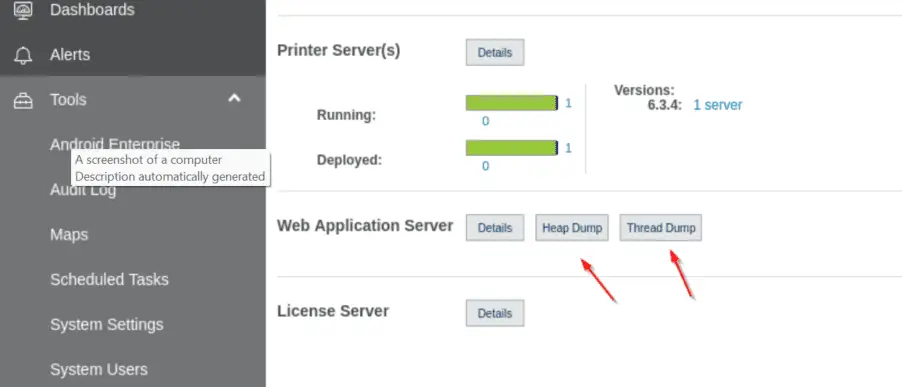
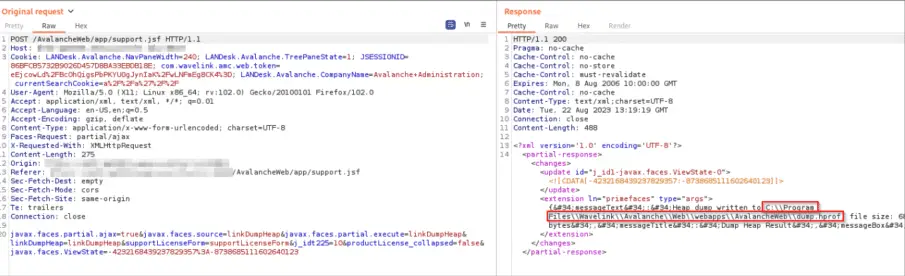
An alarming twist to this tale is the possibility of accessing a heap dump of the Avalanche process, a feature originally intended for debugging. If an attacker, or even an unwitting administrator, performs a heap dump, the file `dump.hprof` becomes a treasure trove of sensitive information, readily accessible through the path traversal attack.

An attacker, armed with the `wget` command, can download the dump file and sift through it for login request bodies. These bodies, still lingering in memory, may contain usernames and passwords, leaving the door wide open for privilege escalation or lateral movement within an organization’s network.
“Via performing some basic string searches, it’s possible to find the login request’s bodies still in memory,” the researcher explained.
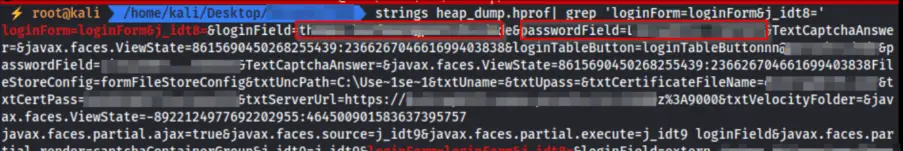
“Within the bodies, username and passwords are exposed to attackers. They can use this information to elevate privileges or move laterally within the environment.“