A critical security vulnerability has been discovered in Milesight Industrial Cellular Routers that could allow attackers to expose sensitive information and gain unauthorized access to devices. The vulnerability (CVE-2023-43261) has a CVSS score of 7.3, making it a high-severity threat.
The vulnerability stems from a misconfiguration that results in directory listing being enabled on the router systems. This means that attackers can view a list of all the files and directories on the router, including log files. These log files may contain sensitive information such as admin and other user passwords, even though they are encrypted.

To make matters worse, the JavaScript code for the router’s web interface contains a hardcoded AES secret key and initialization vector (IV). This means that attackers can decrypt the passwords in the log files, even if they are encrypted.
Security researcher Bipin Jitiya, who discovered and reported the vulnerability, has published a blog post with a proof-of-concept exploit and additional technical details.
The following Milesight Industrial Cellular Routers are affected by the CVE-2023-43261 vulnerability:
- UR5X
- UR32L
- UR32
- UR35
- UR41
- Potential other Industrial Cellular Routers – still under investigation.
However, the waters are murky for earlier versions, requiring vendor verification. Despite Bipin’s outreach, a formal response from Milesight remains elusive.
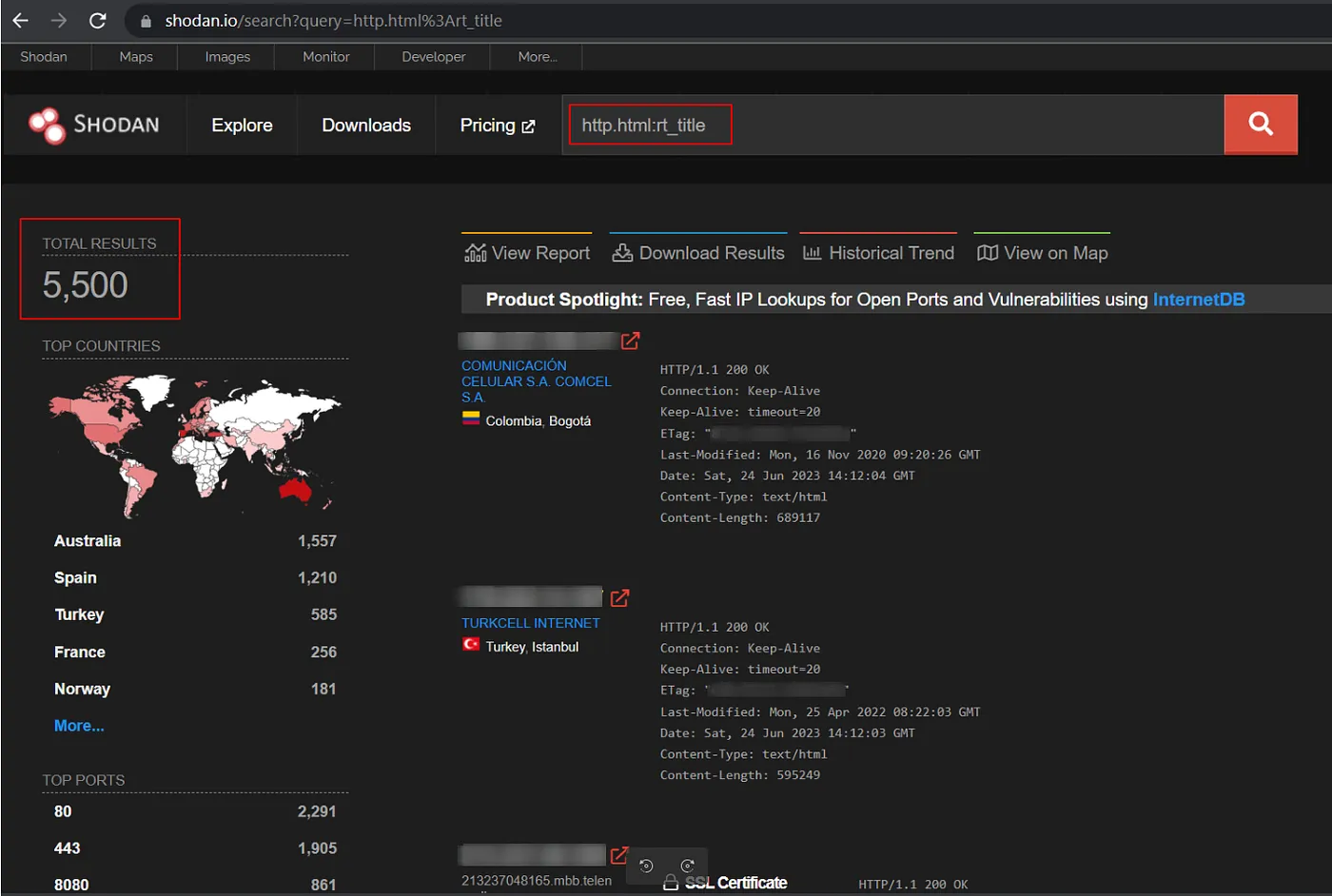
A Shodan search confirms that more than 5,500 Milesight routers are currently reachable over the Internet. This means that a large number of devices are at risk of being exploited by attackers.

Milesight has released a patch for firmware v35.3.0.7. Users are urged to update their routers to this version as soon as possible.
Furthermore, Bipin’s deep dive into debugging and analysis unveiled additional vulnerabilities. However, a shroud of company confidentiality keeps these findings under wraps.
What can you do to protect yourself?
If you are using a Milesight Industrial Cellular Router, you should take the following steps to protect yourself:
- Update your router to firmware v35.3.0.7 or later.
- Change the default username and password for your router.
- Disable the directory listing on your router.
- Enable two-factor authentication for your router web interface.
- Consider using a firewall or other security solution to protect your router from unauthorized access.