The News & Blog Designer Pack WordPress plugin is a popular plugin that allows users to create custom news and blog pages for their websites. However, a recent vulnerability, tracked as CVE-2023-5815, has been discovered in the plugin that could allow unauthenticated attackers to execute arbitrary code on vulnerable websites.
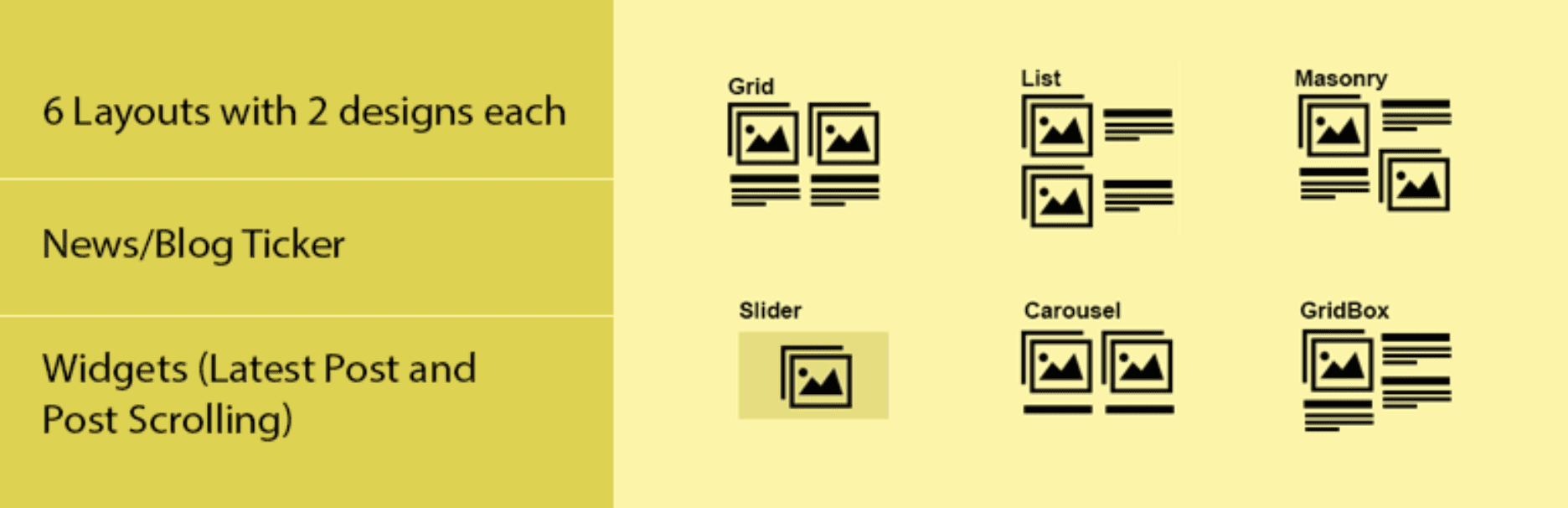
The News & Blog Designer Pack prides itself as a handy tool for digital creators, enabling them to design catchy news pages and blogs. With over 30,000 installations, it’s no surprise that this plugin has found favor amongst bloggers, journalists, and news portal admins. Its ability to seamlessly display WordPress posts in myriad designs, be it through grids, sliders, carousels, tickers, or masonry layouts, has indeed cemented its position as a must-have for many.

All versions of the plugin, up to and including 3.4.1, are vulnerable to a Remote Code Execution (RCE) flaw.
The root cause of this vulnerability is the bdp_get_more_post function, which has been found to be tethered to a nopriv AJAX hook. The key issue stems from the function’s unsavory decision to utilize the extract() method in an unsafe manner, pulling values directly from the POST variable. To those not immersed in the nuances of code, this might seem like mere technical jargon. However, this flaw enables unauthenticated attackers to not only craft PHP files on the host but also incorporate them. The end result? A gateway to remote code execution.
With a CVSS score of 9.8, CVE-2023-5815 isn’t just a minor hiccup. It’s a glaring oversight that demands immediate remediation. If you’re one among the 30,000 using this plugin, the call to action is clear: update immediately and secure your WordPress website.
The best way to protect yourself from this vulnerability is to update to the latest version (3.4.2) of the News & Blog Designer Pack WordPress plugin. If you are unable to update the plugin immediately, you can take the following steps to mitigate the risk:
- Disable the plugin until it is updated.
- Block all access to the bdp_get_more_post function.
- Implement a web application firewall (WAF) to block malicious requests.