Google has released a critical security update to address a zero-day vulnerability in its Chrome browser. This actively exploited flaw, tracked as CVE-2023-6345, could allow attackers to remotely execute code on affected devices.
The vulnerability stems from an integer overflow issue in Skia, an open-source 2D graphics library used by Chrome. This means that attackers could craft malicious websites or content that could trick the browser into processing data in a way that causes it to crash or execute arbitrary code. Benoît Sevens and Clément Lecigne of Google’s Threat Analysis Group (TAG) have been credited with discovering and reporting the flaw on November 24, 2023.
Google has acknowledged that an exploit for CVE-2023-6345 exists in the wild, meaning that attackers are already actively using it to target Chrome users. This underscores the importance of promptly applying the latest security updates to protect your devices.
What Other Vulnerabilities Did Google Fix?
In addition to the zero-day vulnerability, Google also fixed six other security issues with the latest Chrome update. These vulnerabilities include:
- CVE-2023-6348: Type Confusion in Spellcheck
- CVE-2023-6347: Use after free in Mojo
- CVE-2023-6346: Use after free in WebAudio
- CVE-2023-6350: Out-of-bounds memory access in libavif
- CVE-2023-6351: Use after free in libavif
What Can You Do?
To safeguard your computer from this zero-day vulnerability, it is crucial to update your Chrome browser to the latest version (119.0.6045.199 for Mac and Linux and 119.0.6045.199/.200 for Windows) as soon as possible. Here’s how to do it:
-
Open Chrome and click on the three dots in the top right corner.
-
Select “Settings” from the drop-down menu.
-
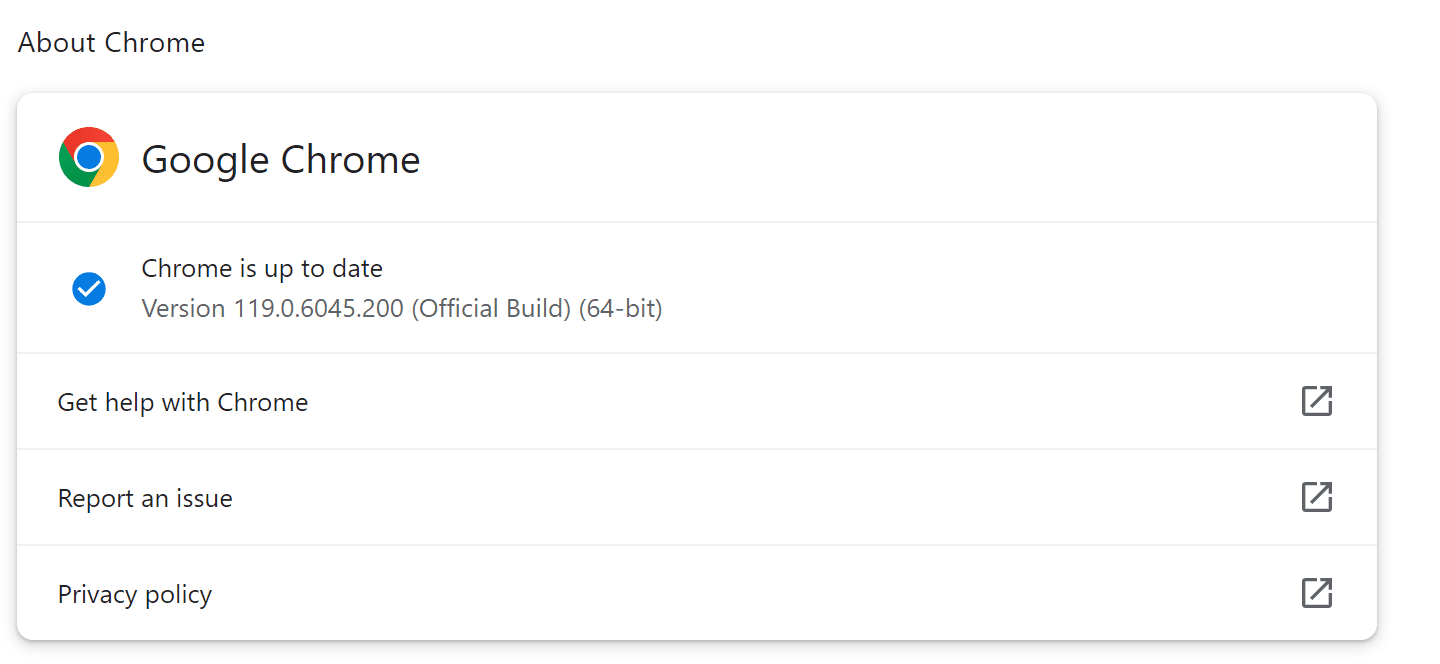
Scroll down to the bottom of the page and click on “About Chrome.”
-
Chrome will check for updates. If an update is available, it will automatically download and install it.
-
Once the update is installed, restart Chrome to ensure it is running the latest patched version.