Contact Form 7 Flaw (CVE-2023-6449): Patch Now to Prevent Website Exploitation
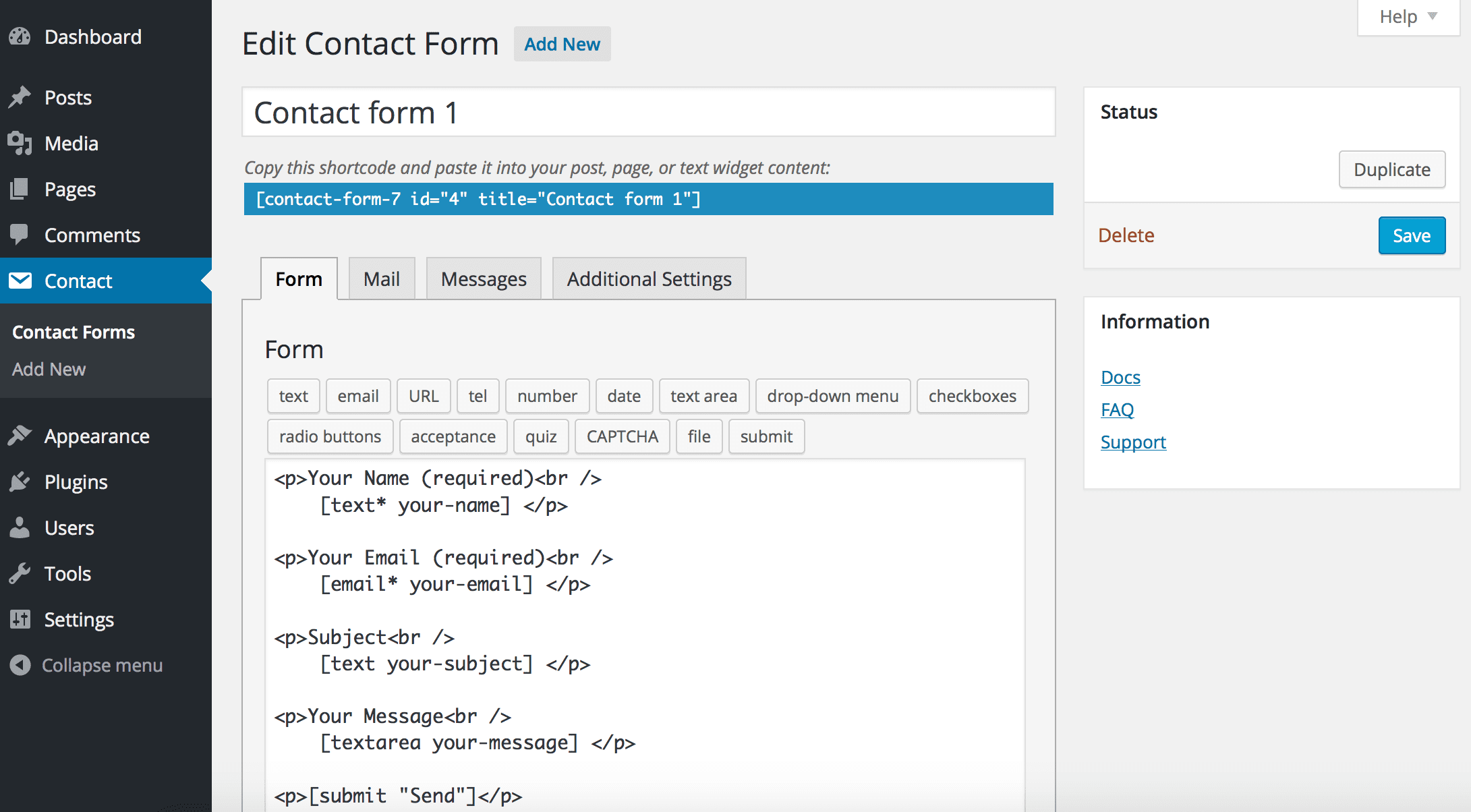
Contact Form 7, a popular WordPress plugin with over 5 million installations, has been found to harbor a vulnerability (CVE-2023-6449, CVSS score of 6.6) that could allow malicious actors to upload arbitrary files to an affected website. This vulnerability poses a significant security risk, as it could be exploited to gain unauthorized access to the website or even execute malicious code.
The vulnerability stems from insufficient file type validation and blocklisting mechanisms within the Contact Form 7 plugin. This oversight allows authenticated attackers, such as those with editor-level privileges, to upload any type of file to the affected website. While the uploaded files are typically deleted immediately due to the htaccess configuration, some plugins may inadvertently extend their lifespan on the server.

In scenarios where the uploaded files remain on the server, attackers could potentially exploit them to execute malicious code. This could involve leveraging local file inclusion vulnerabilities to gain remote code execution capabilities, effectively granting them complete control over the compromised website.
To address this vulnerability and safeguard your website, it is crucial to upgrade Contact Form 7 to the latest version, 5.8.4 or later. This update rectifies the file validation and blocklisting issues, effectively closing the loophole that attackers could exploit.
Apart from updating Contact Form 7, consider implementing additional security measures to further protect your website:
-
Regular Plugin Updates: Maintain an up-to-date plugin environment by regularly checking for and installing security patches and updates.
-
Strong Passwords: Enforce strong password policies for all website users to minimize the risk of unauthorized access.
-
Vulnerability Scanning: Regularly scan your website for vulnerabilities using reputable security scanners to identify and address potential weaknesses promptly.
-
Web Application Firewall (WAF): Implement a WAF to filter and block malicious traffic, providing an additional layer of protection against web-based attacks.
By taking these proactive steps, you can significantly enhance your website’s security posture and mitigate the risk posed by vulnerabilities like CVE-2023-6449.



