Image: SEC Consult Vulnerability Lab
A severe security vulnerability (CVE-2024-0670, CVSS 8.8) has been exposed in Checkmk, a popular IT monitoring solution utilized by organizations across various industries, including tech leaders like Adobe, Cisco, Siemens, HP, and Volkswagen. Michael Baer, a security expert at SEC Consult Vulnerability Lab, is credited with the discovery of this concerning flaw.
Understanding the Exploit
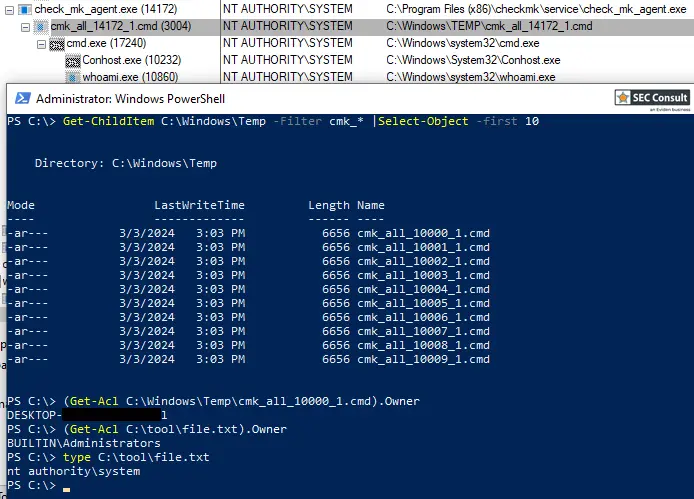
This vulnerability takes advantage of the manner in which the Checkmk Windows agent handles temporary files. Adversaries can manipulate this by preemptively placing specially crafted malicious files with read-only permissions within the C:\Windows\Temp directory. When Checkmk interacts with these files, it inadvertently runs them under the highest level of Windows access – SYSTEM privileges.

“In order to execute some system commands Checkmk Windows agent writes cmd files to C:\Windows\Temp\ and afterwards executes them. The permissions of the files were set restrictive but existing files were not properly handled. If a cmd file already existed and was write protected the agent was not able to rewrite the file but did not handle this case and executed the file nevertheless,” Checkmk wrote in its security advisory.
The Danger: What Could Go Wrong
A successful attack using CVE-2024-0670 gives threat actors extensive control over compromised systems. Here’s what could happen:
- Data Theft: Sensitive information could be stolen with ease, potentially leading to data breaches with considerable legal and reputational consequences.
- Malware Deployment: Threat actors could further infect a system with ransomware, crippling operations and extorting money, or other malicious payloads for espionage purposes.
- Network Infiltration: This foothold on a single machine could pave the way for attackers to escalate their attacks and infiltrate other vulnerable systems within the organization’s network.
Who’s at Risk?
Any organization using the following Checkmk versions needs immediate action:
- 2.0.0
- 2.1.0
- 2.2.0
Protect Yourself – Patching & Monitoring
Checkmk has commendably released patched versions to address this vulnerability. Immediate updates to 2.1.0p40 or 2.2.0p23 are the top priority. You can download these from the official Checkmk website: https://checkmk.com/download
While the patch is crucial, proactivity extends beyond just patching:
- Look for Signs: Monitor your C:\Windows\Temp directory for files with names like cmk_all_\d+_1.cmd. This pattern could hint at attempted exploitation.
- Security Tools: Utilize endpoint protection solutions and intrusion detection systems to spot attacks leveraging this or other vulnerabilities.