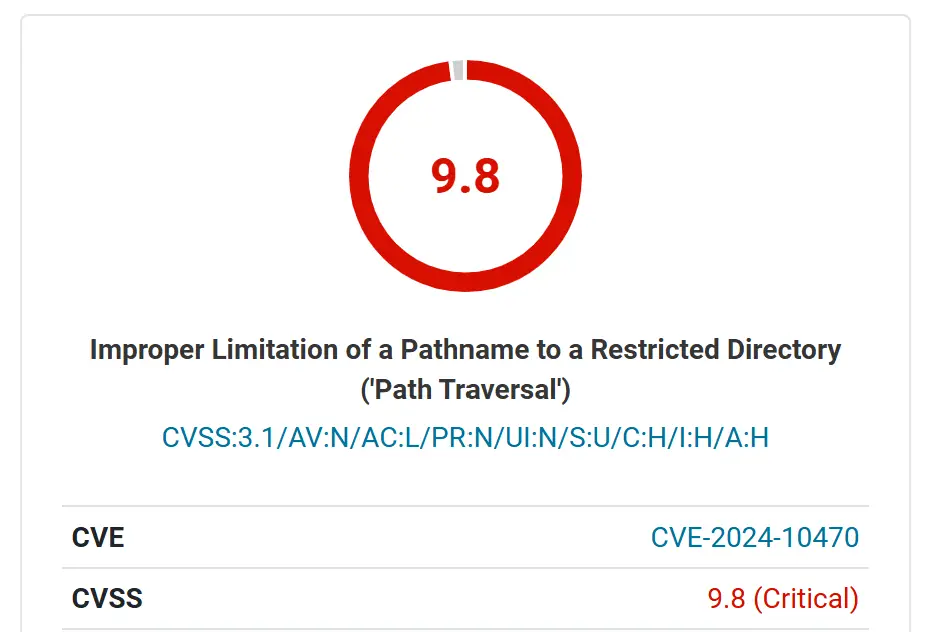
A critical vulnerability, tagged as CVE-2024-10470, has been identified in WPLMS, a WordPress premium theme widely used for online course management. Security researcher István Márton at Wordfence reported that this Arbitrary File Read and Deletion vulnerability poses a high security risk, with a CVSS score of 9.8, making it possible for unauthenticated attackers to read and delete sensitive files, including the essential wp-config.php file.
WPLMS, which boasts over 28,000 installations, is a feature-rich theme supporting courses, quizzes, and certificates, tailored to meet e-learning needs. However, István Márton’s analysis reveals a significant flaw in its code, allowing malicious actors to exploit the “envato-setup-export.php” file. “The code does not include a capability check, and nothing prevents direct file access,” Márton’s report explains, making the vulnerability exploitable even if the theme isn’t active but merely installed.
A central issue lies in the unsanitized “zip_file” parameter. This parameter lets attackers specify any file on the server, which is then read and deleted by the vulnerable code. Márton notes, “The file’s content is read with the readfile() function for download, and then it is immediately deleted with the unlink() function.” This sequence leaves WPLMS sites defenseless, as attackers can access and erase any file, from wp-config.php to user-uploaded content.
This vulnerability doesn’t just enable unauthorized file access and deletion; it opens a pathway to full site takeovers. By deleting the wp-config.php file, attackers force a vulnerable website into setup mode. “Deleting wp-config.php forces the site into a setup state,” the report states, “allowing an attacker to initiate a site takeover by connecting it to a database under their control.” This leaves users’ data and website content at serious risk of compromise.
The vulnerability was responsibly reported by cybersecurity researcher Foxyyy through Wordfence’s Bug Bounty Program, earning a $900 bounty for the discovery. Wordfence advises all WPLMS users to update their sites immediately, as “the latest patched version of WPLMS, version 4.963 at the time of this writing,” resolves the security flaw.
Related Posts:
- Unpatched WordPress bug puts your website at risk
- WordPress Issues Urgent Security Update to Patch Multiple Vulnerabilities